Applocker is a windows feature which can be used to block already installed application from running or prevent installing certain applications. It was introduced with Windows 7 and Windows Server 2008R2 while replacing software restriction policies. AppLocker rules are much more powerful and very easy to implement than Software restriction policies
With Windows 10, AppLocker can be used only with Enterprise and Education editions. AppLocker can be used to control the following file types.
- Executables: exe and com
- Scripts: js, ps1, vbs, cmd and bat
- Windows Installer files: msi and msp
- Dynamic-link libraries: dll and ocx (This rule collection has to be enabled as it is not enabled by default)
- Packaged app Rules : aappx (Windows 8 & 10 only)
Benefits of using AppLocker
According to the Microsoft, following benefits can be archived using AppLocker in your organization.
- Application inventory
AppLocker has the ability to enforce its policy in an audit-only mode where all application access activity is collected in event logs for further analysis. Windows PowerShell cmdlets are also available to help you understand application usage and access.
- Protection against unwanted software
AppLocker has the ability to deny applications from running simply by excluding them from the list of allowed applications per business group or user. If an application is not specifically identified by its publisher, installation path, or file hash, the attempt to run the application fails.
- Licensing conformance
AppLocker can provide an inventory of software usage within your organization, so you can identify the software that corresponds to your software licensing agreements and restrict application usage based on licensing agreements.
- Software standardization
AppLocker policies can be configured to allow only supported or approved applications to run on computers within a business group. This permits a more uniform application deployment.
- Manageability improvement
AppLocker policies can be modified and deployed through your existing Group Policy infrastructure and can work in conjunction with policies created by using Software Restriction Policies. As you manage ongoing change in your support of a business group's applications, you can modify policies and use the AppLocker cmdlets to test the policies for the expected results. You can also design application control policies for situations in which users share computers.
Implementing AppLocker
With Windows 10, AppLocker can be implemented using local security polices or centrally by Active directory group policies. In following example I’m implementing AppLocker using local security polices of a Windows 10 machine. You can follow the same steps when you implement it in Active directory environment using Group Polices.
AppLocker is very powerful tool, if you mistype a path or select all executables, it can block every application on the targeted machines. So it’s advisable first to test the configurations in a test machine and then only publish to the production machines.
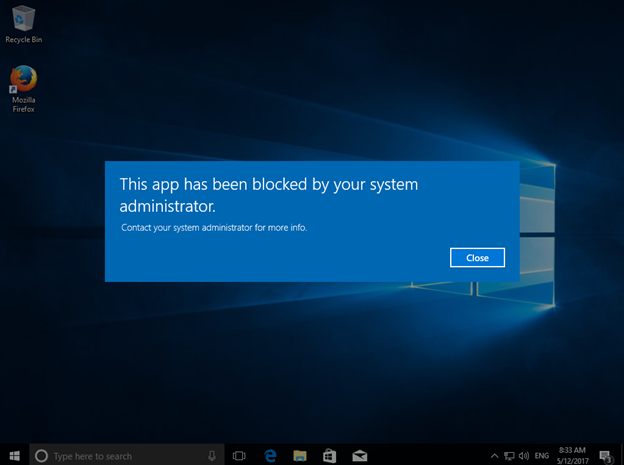
In following example I’m blocking Mozilla Firefox application from a Windows 10 client.
- Open local security polices by running gpedit.msc on run
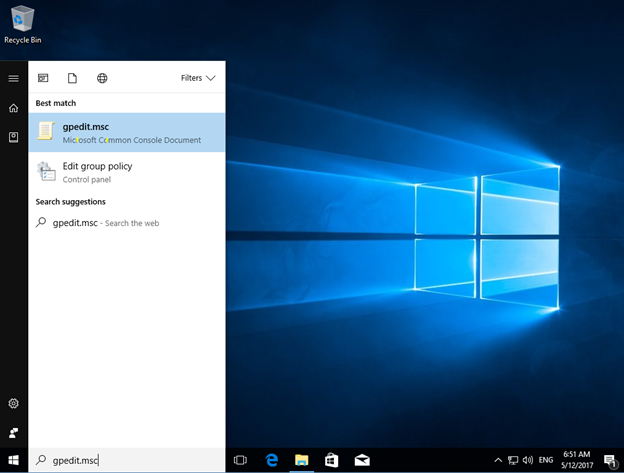
- Go to Computer Configurations, Windows Settings, Security Settings, AppLocker
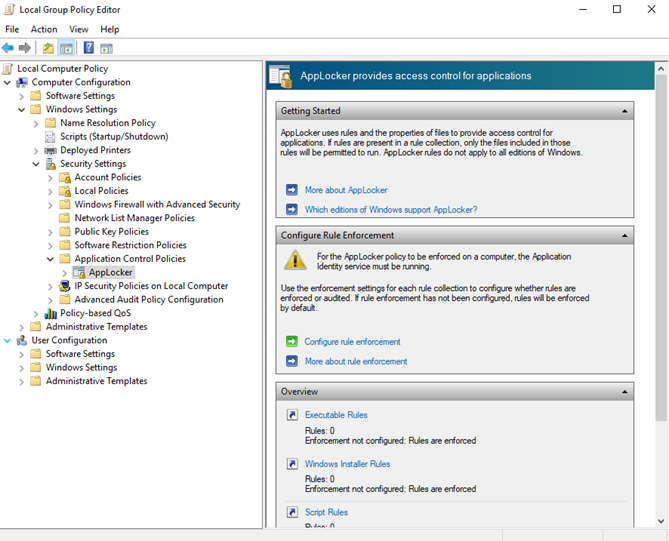
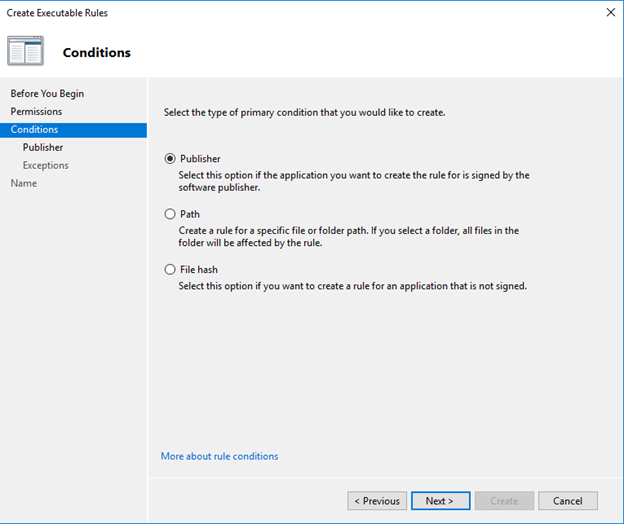
- In my example I’m going to block a executable program, right click on the executable rules and select Create New Rule
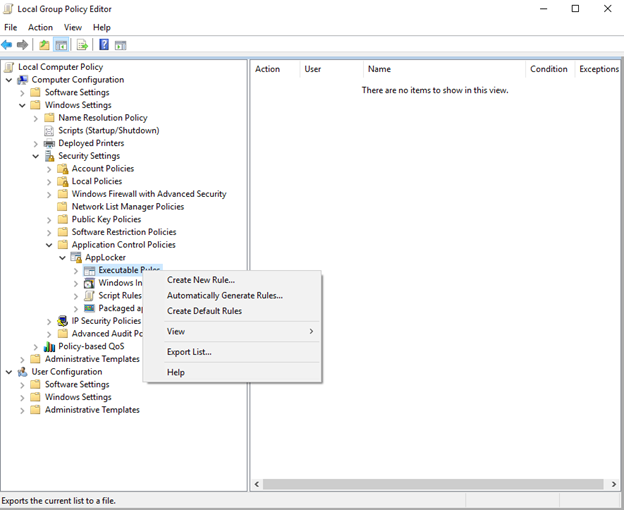
- Follow the wizard and select Deny
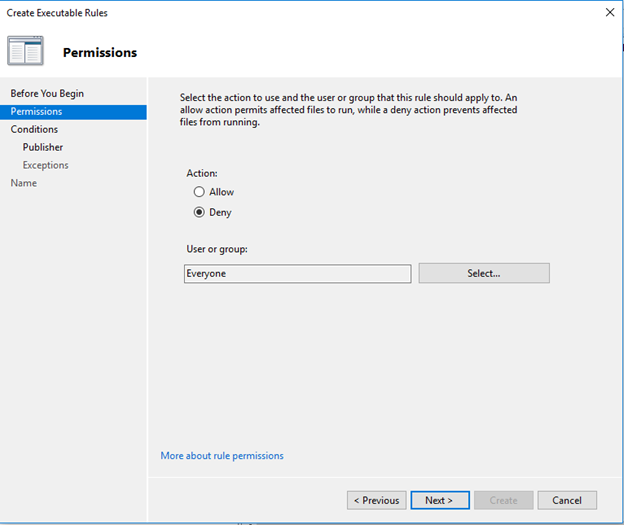
- I’m blocking a particular application, so select the publisher and browse the application EXE in the reference file.
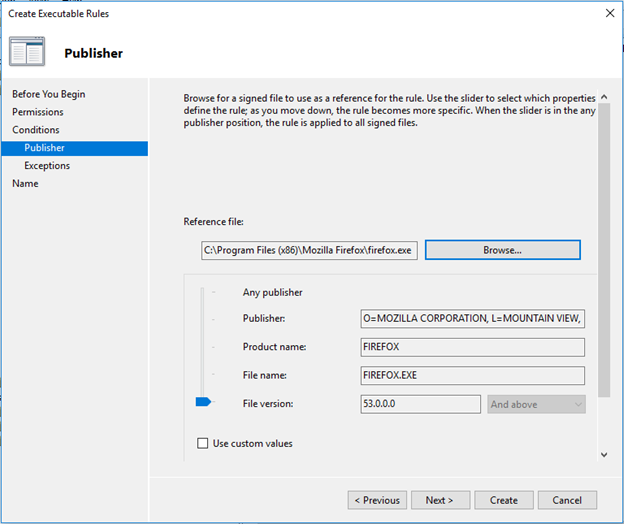
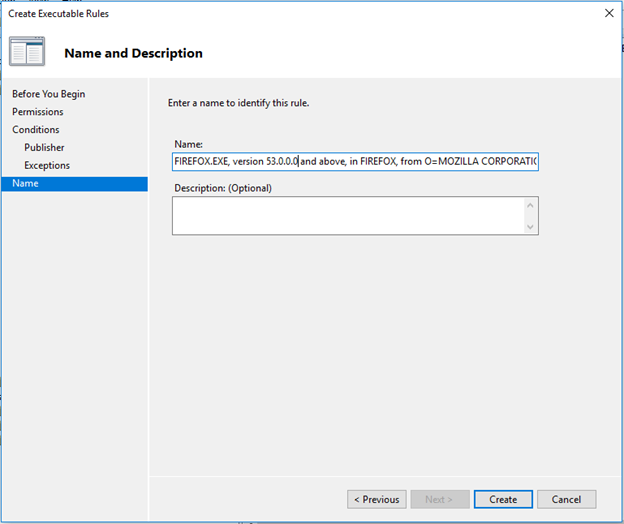
- Click Next in the exceptions and give a name to the rule, Create the rule
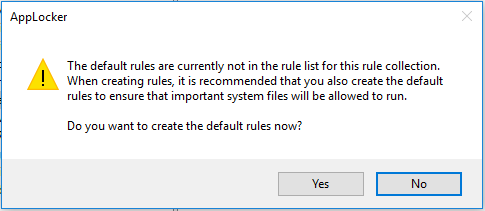
- When creating the first rule, AppLocker will be creating default rules to enable other applications.
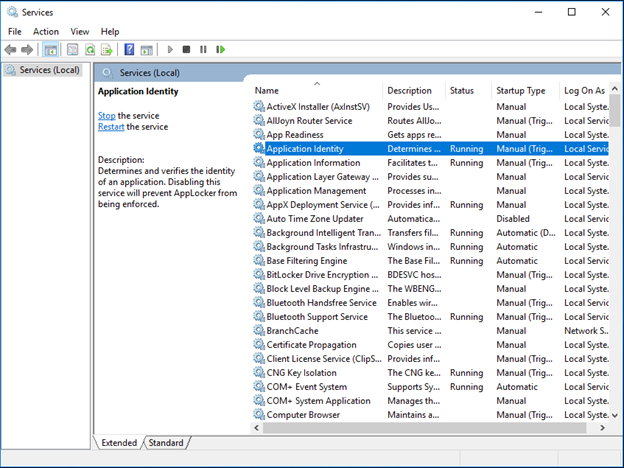
- Check Application identify service is running, if not start the service, you can set the startup type to automatically. This service is required to identify the applications running.
- Test the Application, it should be blocked. also you cannot install this application after implemented this policy.
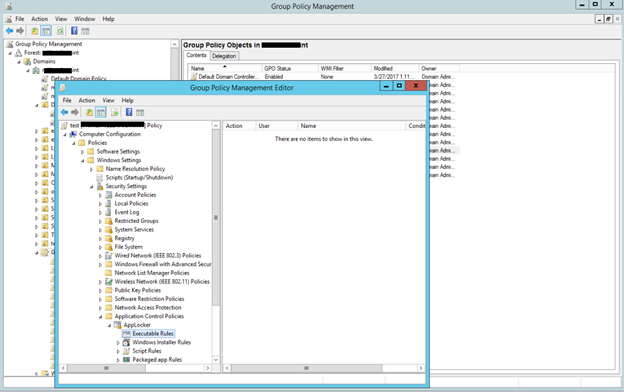
Centrally Manage AppLocker rules
As discussed earlier, you can centrally deploy AppLocker rules using Group Policies, Create a group policy object in the Domain controller and use the above steps to create the rule. Be sure to test the rule before deploying to the production users.
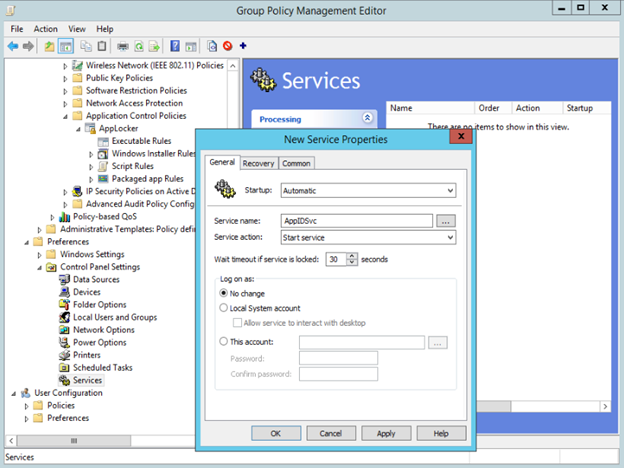
If the target computers Application Identify service is not running, you may have to run it using another GPO. Go to the Preferences – Control Panel Settings – Services – New – Service, Select the Application Identify service and select the startup type to Automatic and service action to start.
Deploy the GPO to the target machines.
Rule Enforcement – Audit Mode
Without enforcing the rules right away, you can also Audit/Monitor the activities. According to the previous example of blocking Firefox, with the Audit mode you can see who is using the application and the frequency of usage. Every time application is used, an event will be generated in the event log. If you did not configure the rule Enforcement, Rule will be enforced by default.
References - Microsoft Technet
Hope this post is useful
Cheers
Asitha De Silva













