From my previous post of AppLocker with Windows 10, I have discussed about AppLocker and how to implement it with Windows 10. From this post I’m hoping to discuss how to centrally deploy and manage AppLocker polices with Windows Intune.
Configuration service providers (CSP) can be used to configure device settings in Windows 10. MDM service providers such as Windows Intune can use CSP to define configurations and settings to Windows 10 devices. Open Mobile Alliance Device Management (OMA-DM) protocol uses the XML-based Synchronization Markup Language (SyncML) for data exchange between compliant servers and clients. CSP policies should be written using this format.
From this post let’s see how to create the configurations XML for AppLocker and deploy it using OMA-DM settings for AppLocker CSP.
These are the high level steps you have to follow
- Use a Windows 10 client to create the AppLocker policy and export it as XML
- Change XML settings as required
- Create Configurations policy
- Add AppLocker OMA-URL Settings
- Test the configurations
Exporting AppLocker Policy
As discussed in the introduction, CSP require the configurations from a XML format. And for the AppLocker, the easiest method is to create the XML is from a Windows 10 machine using the local policy to define the AppLocker policy and exporting it as a XML. Let’s see how to do this.
- Login to a Windows 10 computer and open the Local policy to create the AppLocker policy. You can follow my previous post for creating the policy,
http://www.terminalworks.com/blog/post/2017/05/16/applocker-with-windows-10
- Select the AppLocker policy, right click and export,
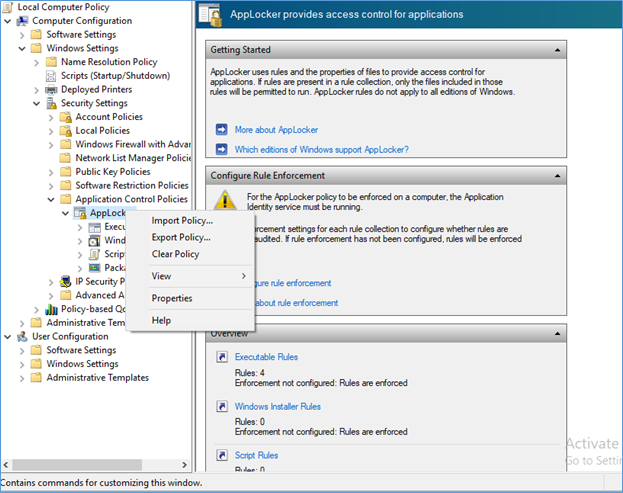
- Open the saved XML and select only the AppLocker policy part, in example my AppLocker policy is to deny Bittorrent App and following part is need to be copied.
<RuleCollection Type="Exe" EnforcementMode="Enabled">
<FilePathRule Id="921cc481-6e17-4653-8f75-050b80acca20" Name="(Default Rule) All files located in the Program Files folder" Description="Allows members of the Everyone group to run applications that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="a61c8b2c-a319-4cd0-9690-d2177cad7b51" Name="(Default Rule) All files located in the Windows folder" Description="Allows members of the Everyone group to run applications that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="fd686d83-a829-4351-8ff4-27c7de5755d2" Name="(Default Rule) All files" Description="Allows members of the local Administrators group to run all applications." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
<FilePublisherRule Id="2a4b27b4-681f-40f2-a1e4-18b6f1cfcf98" Name="BITTORRENT.EXE, version 7.10.0.0 and above, in BITTORRENT, from O=BITTORRENT INC, L=SAN FRANCISCO, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=BITTORRENT INC, L=SAN FRANCISCO, S=CALIFORNIA, C=US" ProductName="BITTORRENT" BinaryName="BITTORRENT.EXE">
<BinaryVersionRange LowSection="7.10.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
Create the Custom Configurations Policy
- Login to the Intune portal, I’m still using the Intune Classic portal J
- Navigate to Policy – Configuration policy – ADD
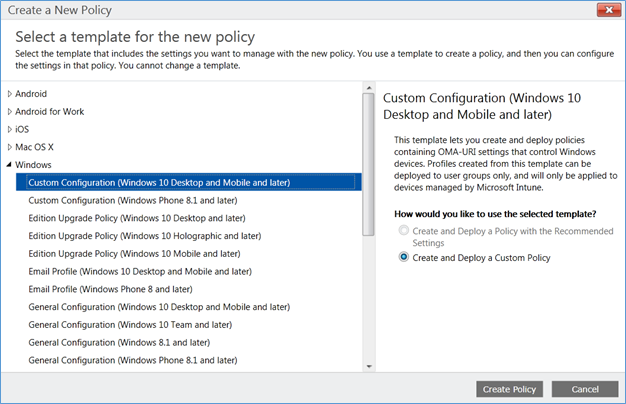
- In create new policy, open Windows and Custom configuration Window 10, select Create policy
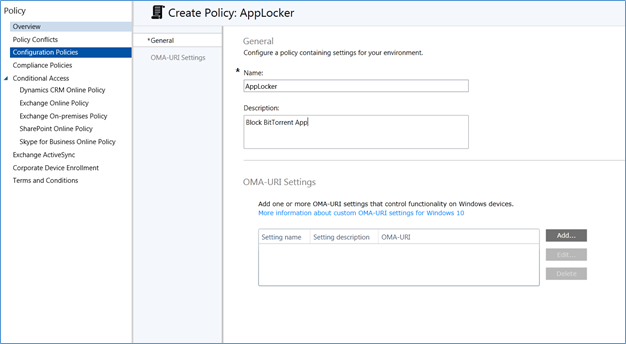
- In Create policy window provide the name and description of the policy and click ADD in the OMI-URL settings
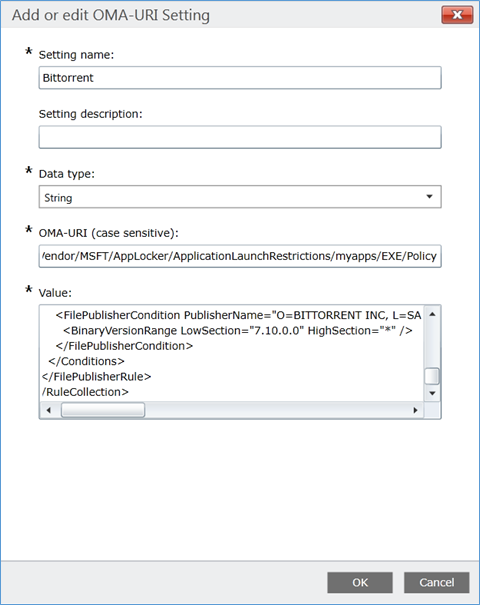
- In the OMA-URI settings, fill the settings according to the below details
Setting Name – Bitlocker Block
Setting description – description
Data type – String
OMA-URL – ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/myapps/EXE/Policy
Value – XML file
<RuleCollection Type="Exe" EnforcementMode="Enabled">
<FilePathRule Id="921cc481-6e17-4653-8f75-050b80acca20" Name="(Default Rule) All files located in the Program Files folder" Description="Allows members of the Everyone group to run applications that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%PROGRAMFILES%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="a61c8b2c-a319-4cd0-9690-d2177cad7b51" Name="(Default Rule) All files located in the Windows folder" Description="Allows members of the Everyone group to run applications that are located in the Windows folder." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePathCondition Path="%WINDIR%\*" />
</Conditions>
</FilePathRule>
<FilePathRule Id="fd686d83-a829-4351-8ff4-27c7de5755d2" Name="(Default Rule) All files" Description="Allows members of the local Administrators group to run all applications." UserOrGroupSid="S-1-5-32-544" Action="Allow">
<Conditions>
<FilePathCondition Path="*" />
</Conditions>
</FilePathRule>
<FilePublisherRule Id="2a4b27b4-681f-40f2-a1e4-18b6f1cfcf98" Name="BITTORRENT.EXE, version 7.10.0.0 and above, in BITTORRENT, from O=BITTORRENT INC, L=SAN FRANCISCO, S=CALIFORNIA, C=US" Description="" UserOrGroupSid="S-1-1-0" Action="Deny">
<Conditions>
<FilePublisherCondition PublisherName="O=BITTORRENT INC, L=SAN FRANCISCO, S=CALIFORNIA, C=US" ProductName="BITTORRENT" BinaryName="BITTORRENT.EXE">
<BinaryVersionRange LowSection="7.10.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>
- Save policy
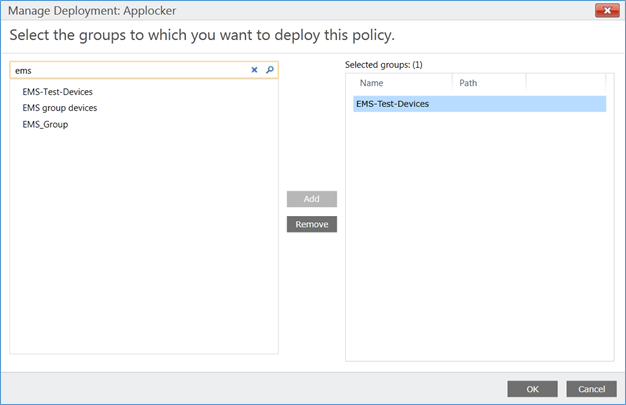
- Select the policy and click Manage Deployment
- Select the group you want to add the AppLocker policy and press OK
Test the configurations
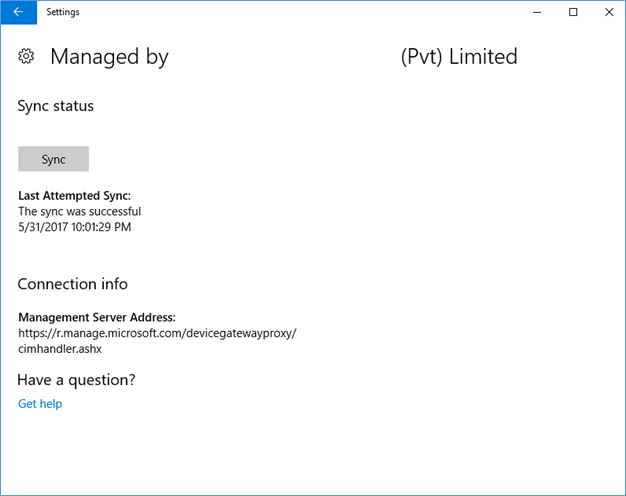
- Login to the Intune manage PC and wait a while till the policy kicks in, also you can refresh the policy from Settings – System – about – Manage or disconnect and select info of organization connected setting, then click Sync
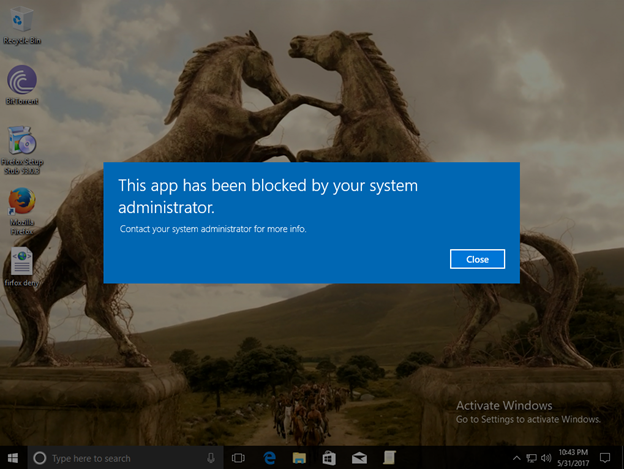
- Test the AppLocker policy by opening the Bittorrent app
Hope this post is useful
Thanks
Asitha De Silva







