Microsoft has released New Azure AD connect with two new features, Pass Through Authentication and Seamless Sign On, Both of this features are still under preview but can be used. This post is all about the Single Sign On feature and how to use it with domain join or Azure AD join computers.
When password sync configured on office 365, it sync the Active directory password hash to azure active directory and when you are sign in to Office 365, you have to provide the same AD credentials. This is called Same Sign On. So it’s like two authentication systems with same credentials, if you changed the password on local active directory, its sync the password to cloud immediately. So this has removed you from managing two passwords in local AD and Office 365, but still you need to type user name and passwords when accessing Office 365 Portal or Outlook Application using domain join or none domain environments.
With the release of SSO feature in AD connect, users total login experience is changing to single sign on. They are no longer required to put the user name or password to access the Office 365 web portal. Also Outlook app no longer ask for the password and you don’t need to save the password in outlook.
How SSO works with Azure AD Connect
SSO is a new feature that you have to enable from AD connect tool. After enabling, account called AZUREADSSOACCT is created in the local active directory and the Kerberos decryption key is shared securely with Azure AD. In addition to this two Kerberos service principal names (SPNs) are created to represent the cloud URLs that are used during authentication between the client and Azure AD. This is a onetime process which is happening after you enable SSO.
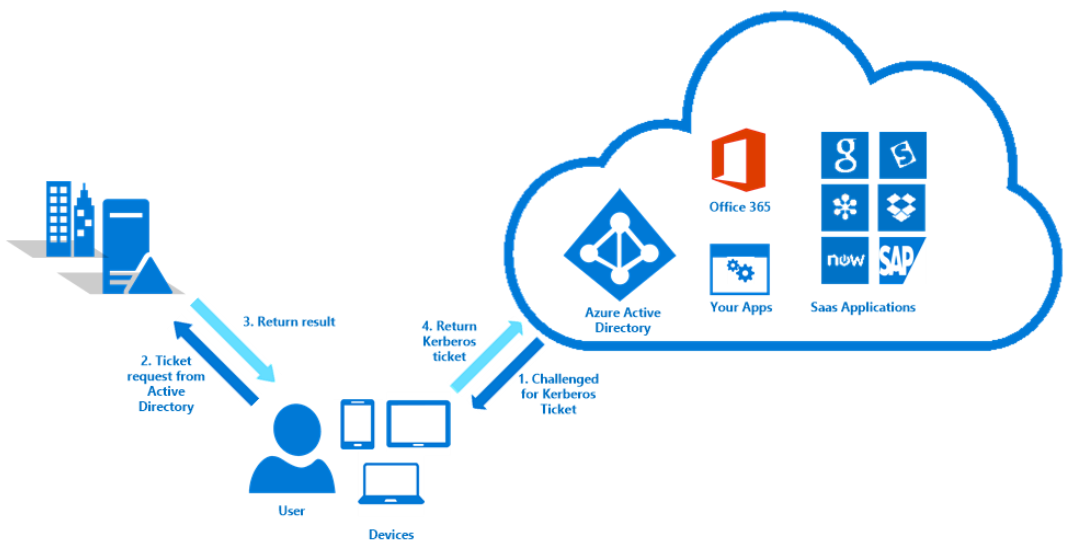
Authentication process for Domain joined PC’s
- When user access a cloud resource, Azure active directory will send a request\ challenge a Kerberos ticket
- User device will send the ticket request to local active directory
- Active directory first generate the Kerberos ticket for the user and locate the account created by AD connect, and encrypt the Kerberos ticket by that machine account secret, and then pass it to the client
- Client return the encrypted Kerberos ticket Azure AD
- Azure AD decrypt the ticket using pre shared decryption key and the validate it with user account information which synced by the AD connect, User name ect.
- After successfully validated, if multi factor or other validation enabled, Azure AD will challenge those requests, else it will provide the access to the Cloud resource
Authentication for None Domain but Azure AD joined PC
- If you have windows 10 devices you can get this Seamless SSO experience by doing the Azure AD join. Azure AD will handle the authentication process and experience is same as the domain join.
- Download the latest version of AD Connect tool
- If you are already having the latest version, you can reconfigure it with the SSO feature or you have uninstall the current version and install the latest version.
- Logon as a domain administrator before installing the AD Connect
- Select custom installation and then tick Password Synchronization and Enable Single Sign On
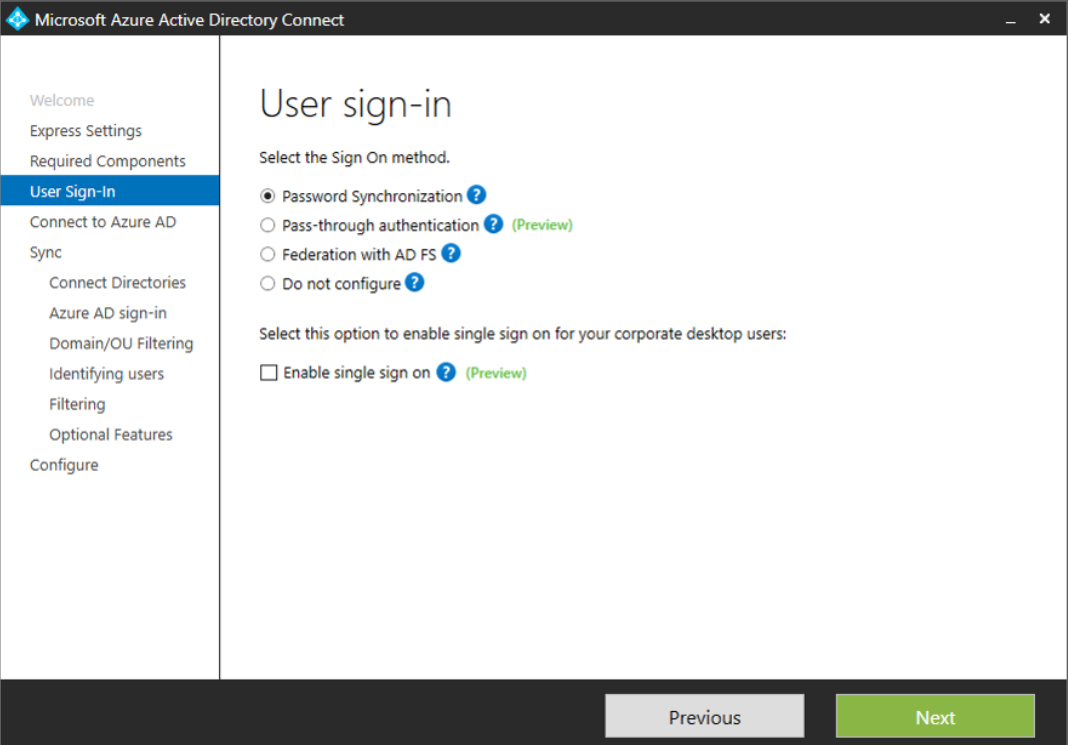
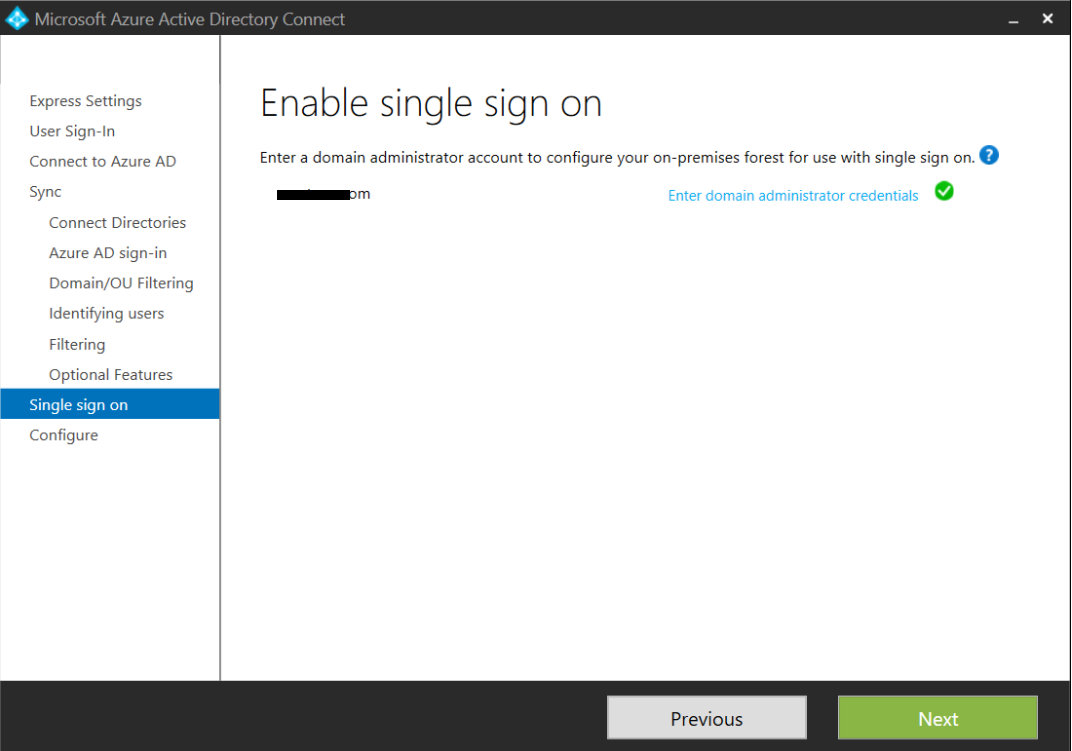
- Click configure to finish the setup
Enable Modern Authentication
Modern authentication is required to enable from Office 365 tenant to experience the single sign on in Microsoft Outlook application. Also it enables sign-in features such as Multi-Factor Authentication (MFA), SAML-based third-party Identity Providers with Office client applications, smart card and certificate-based authentication, and it removes the need for Outlook to use the basic authentication protocol.
By default Modern authentication is enabled to SharePoint Online. Exchange online and Skype for business is switched off. To use SSO feature you have to enable this from PowerShell.
Enable Modern Authentication for Exchange Online
- Connect to the Exchange Online PowerShell
$UserCredential = Get-Credential
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $UserCredential -Authentication Basic –AllowRedirection
Import-PSSession $Session
https://technet.microsoft.com/library/jj984289(v=exchg.160).aspx
- Run the following command in the PowerShell
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
- Use the following command to verify the change
Get-OrganizationConfig | Format-Table -Auto Name,OAuth*
Enable Modern Authentication for Skype for Business
- Connect to Skype for Business Online using PowerShell
$credential = Get-Credential
$session = New-CsOnlineSession -Credential $credential
Import-PSSession $session
- Check modern authentication enabled or not
Get-CsOAuthConfiguration | select *Adal*
- Enable Modern authentication
Set-CsOAuthConfiguration -ClientAdalAuthOverride Allowed
In the client side, Modern authentication is enabled for Office 2016. You can use that version without any changes, but if you are using Office 2013 there is a registry key that you need to change.
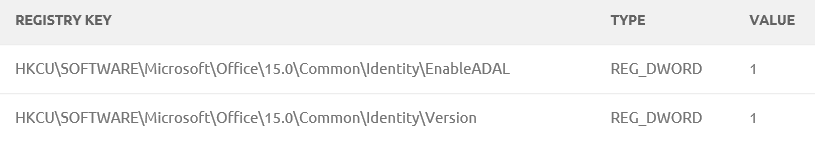
Client Experience Domain Joined PC
Prerequisites
- Domain joined computer
- Login to the user which the Office 365 license assigned
- Connectivity to the DC (Corporate network)
- Define the Kerberos end-points in the cloud as part of the browsers Intranet zone.
Add end points to the Intranet Zone
Following two URL’s need to be added to the intranet zone of the browser. Best way to do this is to create a group policy and deploy from the domain.
https://autologon.microsoftazuread-sso.com
https://aadg.windows.net.nsatc.net
- Create a group policy and add the two URL’s to the following policy
User Configuration\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page and select Site to Zone Assignment List.
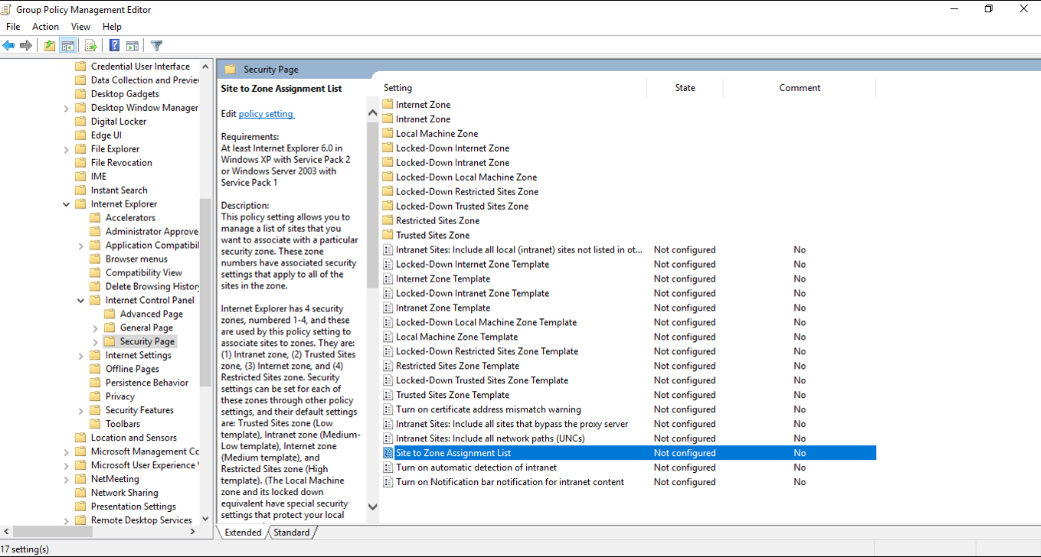
- Enable the policy and add the value as 1
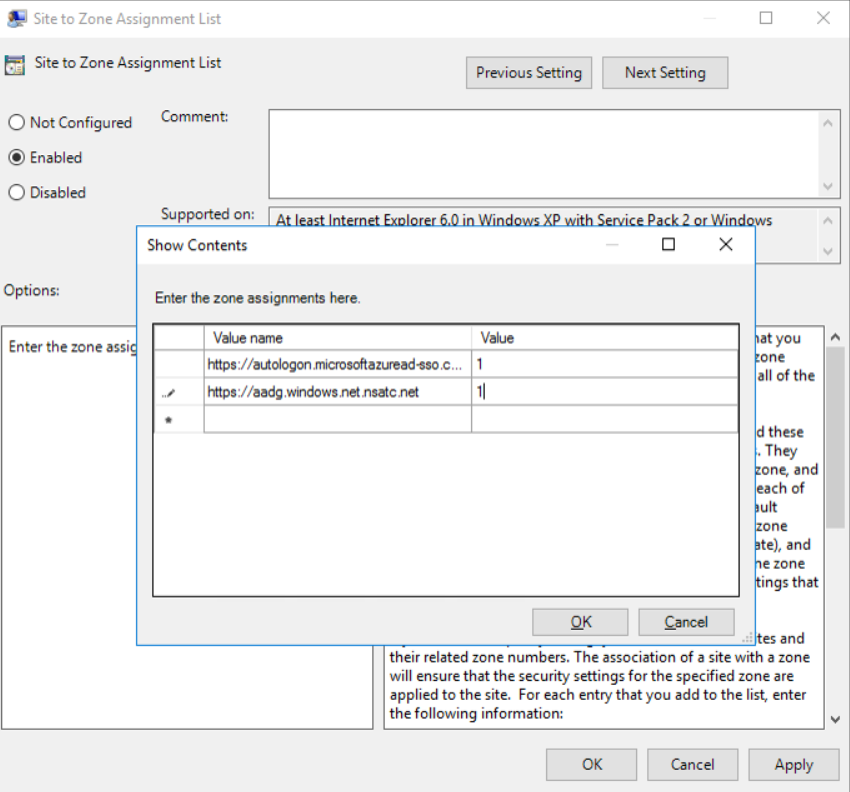
- Deploy the policy to the Office 365 Users
Testing the Experience
- Login to the domain join computer
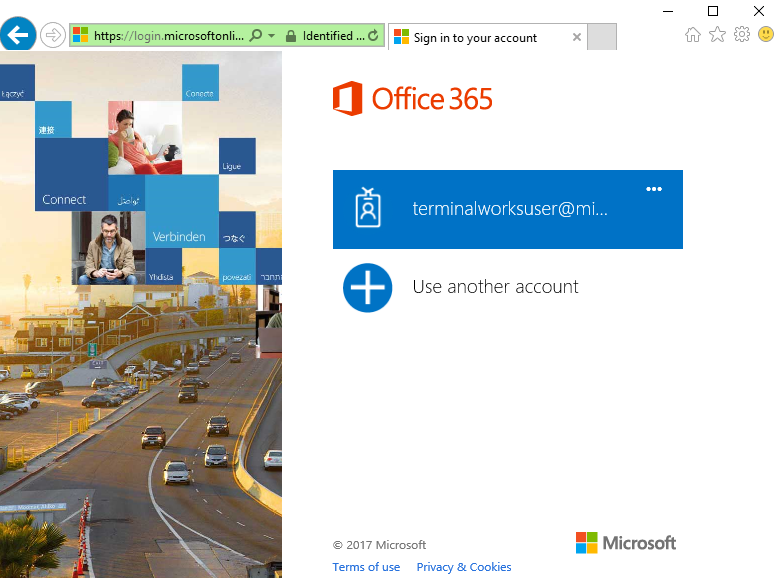
- When you access the portal.office.com using internet explorer, you only need to type the username. You will be directed to the office welcome page
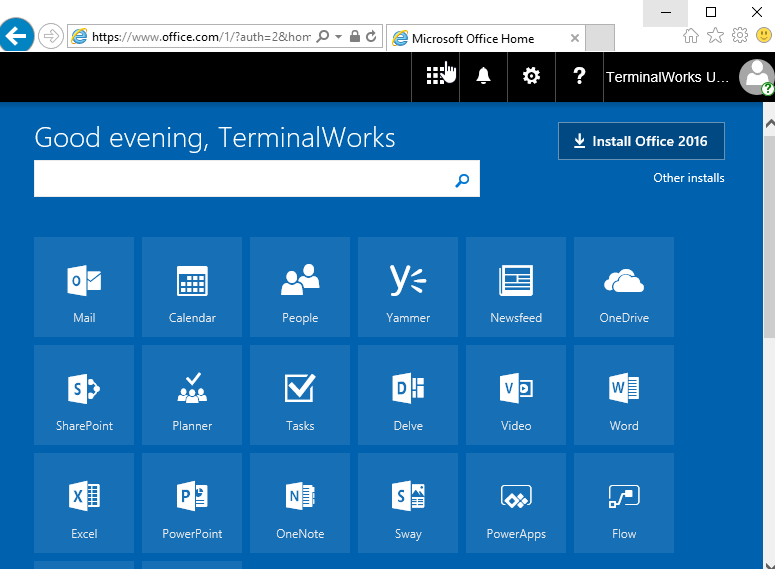
- Before login to Microsoft Outlook 2016 you need to sign in to office, easiest way to do this is Open Word and sign in to the Office.
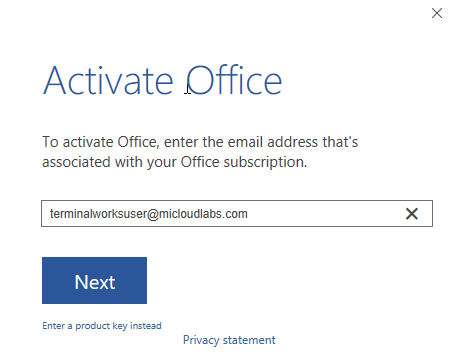
- If required activate the Office, it will not ask for the password.
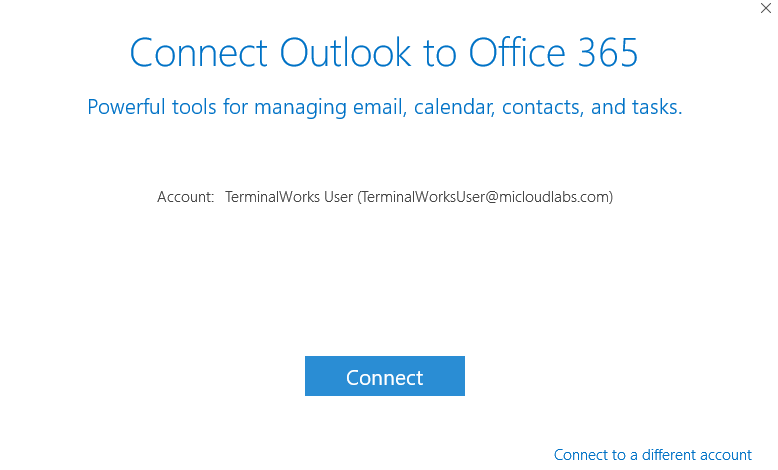
- Open outlook, you only need to click connect to configure the account. It will not ask for the username and password.
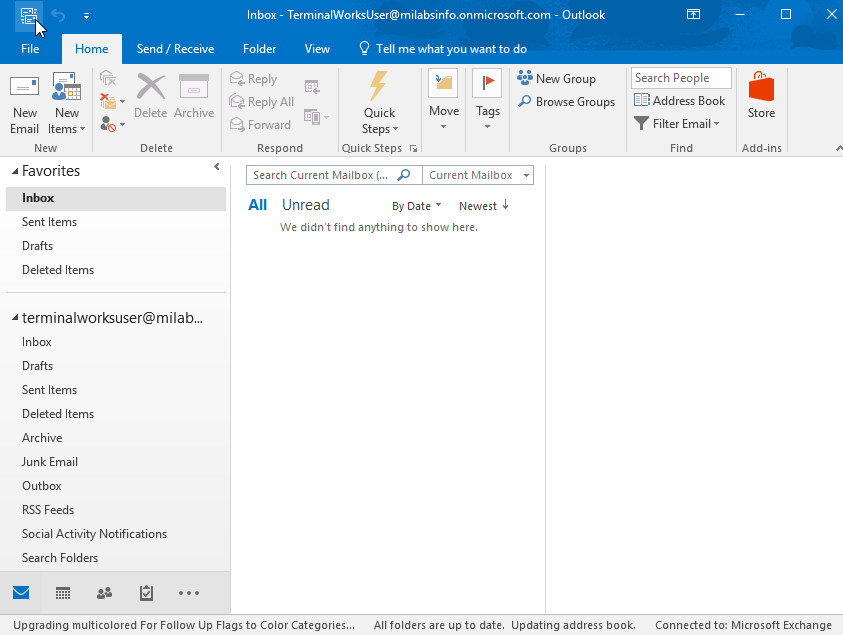
Note – if the domain join computer access the emails from outside the corporate network, public internet. Office 365 portal will ask the password.
Client Experience Azure AD Joined
Most of the large organizations having computers that are not joined to the Active directory domain. Also some organization finding ways how to stay separated from domain join environments because the lack of connectivity to the datacenters. For those environments Azure AD join is useful option. It is not an alternate to the Domain environment but some features like SSO for cloud services can be archived.
You can enable AD connect SSO feature to the Azure AD joined environments. User experience is much superior to the domain join environment because not only the password, it does not ask for the user name when you login to the Portal.office.com.
Prerequisites
- AD connect configured with SSO
- Computer should be Azure AD joined
- Login to the user which the Office 365 license assigned
Note – Password sync is not mandatory, you can use without password sync
Testing the Experience
Follow the same steps above in an Azure AD joined computer. The experiences would be the same and User name will not be asked when you are login to the Portal.office.com.
Final thoughts
If you want to know more information about how the SSO works and the technology behind that please follow the following URL’s.
https://jairocadena.com/2016/11/08/how-sso-works-in-windows-10-devices/
https://docs.microsoft.com/en-us/azure/active-directory/active-directory-azureadjoin-devices-group-policy
References
https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnect-sso
Microsoft ignite conference 2016
Cheers
Asitha De Silva












