Accounts getting locked and unlocking these accounts had become a day to day routing of a system administrator. Problem getting worse when some users complaining they are repeatedly getting their accounts locked in time to time. This is common to most organizations and system administrator need to troubleshoot and find what cause this lockout. From this post let’s discuss why getting locked accounts and how to troubleshoot it using Microsoft Account lockout tool set.
Most common reason for the account lock out is number of wrong password attempts by a user or a program where user saved the password. This is happening because in a domain environment default domain account policies have configured to lock the account when specified number of invalid logon attempts are made.
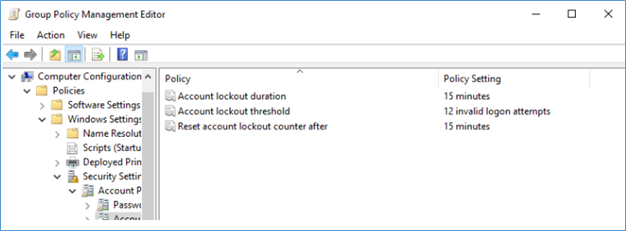
This policy is very important to an organization and should not be removed. It’s very useful when avoiding brute force attacks. Other than brute force, Users tend to save their passwords in mobile phone applications, desktop applications and sometimes run as a service. So soon after a user change the password to a new one these saved location passwords are not getting updates and they become obsolete and when these apps run in the background, they will throw the older invalid password so the domain account policy will lock the account.
Most common users are not knowing or cannot remember where they saved the password to update it. But domain event logs have traces where this logon failure attempt is made and a system administrator can pin point these locations so users to update their passwords from those source location.
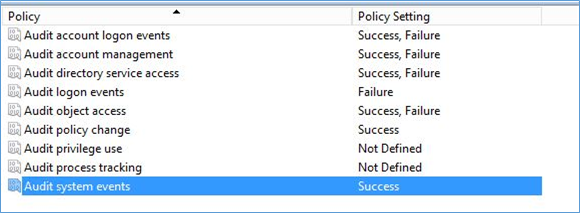
Enable Auditing
Before tracing failed logon attempts, make sure you have already enabled auditing and set audit policy to capture Audit Logon Events – Failure
Using Microsoft Account Lockout and Management Tools
Account lockout and management tools is an old tool kit from Microsoft and you can still use it with latest ADDS environments like server 2016. From these tools first you have to identify which domain controller locked the account and then filter the event log to find the relevant event log information.
- Lockoutstatus.exe
Examines all DCs in a domain, letting you know when the target account last locked out and from which DC. In addition, it provides the locked-out account’s current status and the number of bad password attempts that have been made.
- EventCombMT.exe
Collects and filters events from the event logs of domain controllers. This tool has a built-in search for account lockouts, it gathers the event IDs related to a certain account lockouts in a separate text file.
- Download and extract the Account lockout and Management tool to a Domain controller.
https://www.microsoft.com/en-us/download/details.aspx?id=18465
- Run the Lockoutstatus.exe as run as Admin and in Select target type the User Name of the locked user.
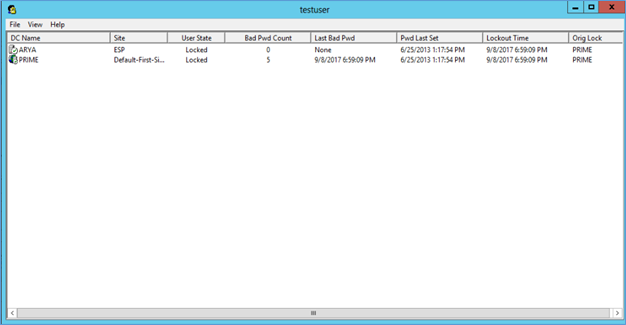
- It will display the User state as locked or not, bad password count and last bad password etc. also using right click account can be unlocked and password can be reset.
- Next run the EventCombMT.exe as run as admin and right click and add domain controllers to the search
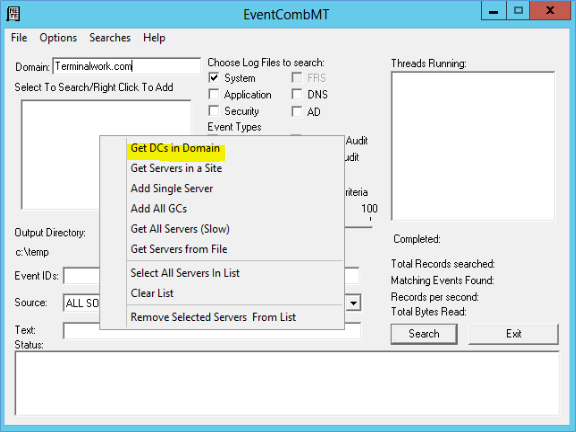
- Event ID 4771 is the login failed event for Active directory servers 2008 and above. So type 4771 in Event ID, select Security log, Event type – Failure audit and to the text type the User name of the locked user. Also if you only choose the domain controller which you found out from Logonstatus.exe, you can narrow the search.
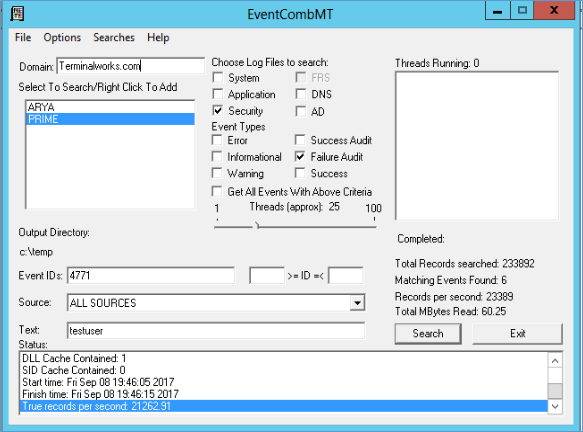
- Search will create a log in the output folder and log will show all the failed attempts with the source IP of the attempt.
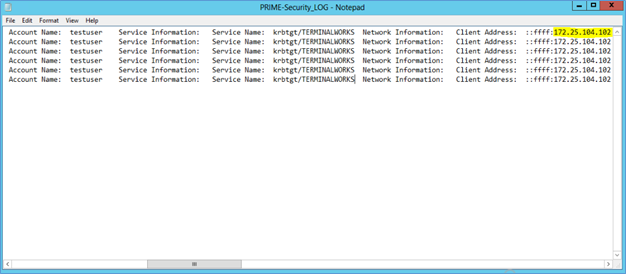
Source of the failed logon attempt can be used to find the traces of saved password, brute force attack or application which is cause to the lockout.
Hope this post is useful
Thanks
Asitha De Silva







