Information Protection can be defined as protecting sensitive data throughout its life cycle inside and outside the organization. Azure Information Protection is a cloud-based solution from Microsoft which will protect documents and emails by classifying and labeling according to the rules and permissions defined by the organization or by users themself.
Azure Information Protection, AIP is kind of new to your ears, but you might be familiar with the terms such as Rights Protection, AD RMS, Azure RMS. Azure Information Protection is evolved from Azure RMS with additional features to a complete document protection product. Let’s try to understand the evolution of Azure RMS to Azure Information Protection
Microsoft Azure RMS
Azure RMS is more about protecting Office 365 Emails from unauthorized use. It can be used to create policies to prevent forward, save, print and read/write. This is built on top of AD RMS with simplified capabilities to encrypt and protect emails and office documents. Azure RMS enables you to share documents within the organization and outside the organization such as suppliers, partners, and dealers, it can be described as following:
- Persistent Protection
- Storage independent solution
- Permit all companies to authenticate
- Authorization policies are enforced
- Tracking and Compliance
- Powerful logging for reporting
- End-user use/abuse tracking
- Ability to remote kill documents
- Enable IT to reason over data
- Ease of Use
- Works across all platforms
- Free content consumption
- Consistent user experience
- Integrated into common apps/services
How Azure RMS Protects data
It is important to understand how Azure RMS works and I’m referring Microsoft TechNet to explain this. A key fact of AIP is that data never leaves or is stored in Azure as part of the protection process. It just makes data unreadable to anyone other than authorized users by encrypting them. Let’s take the same cola formula scenario to explain the protection process.![]()
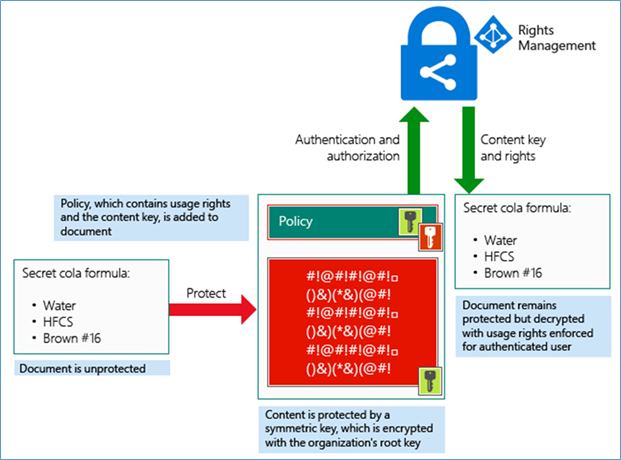
- When RMS policies applied to this document, it will first encrypt the data using a unique key called content key (Green key). This is a random key using AES symmetric encryption algorithm and Once the encryption is done this key will be added to the header of the document.
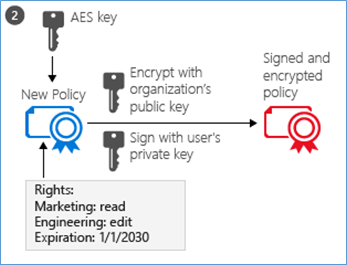
- The RMS client then creates a certificate that includes a policy for the document that includes the usage rights for users or groups, and other restrictions, such as an expiration date. This is the policy (label) that was previously configured.
- Next, the header which contains the policy certificate and content key will be encrypted using the tenant root key which is unique to your organization.
- When this document is shared with someone, if the user is in the same organization then the user shares the same tenant key, and the header can be decrypted by it. Azure will check whether the user has permission for the document by checking the policy, according to the level of permission document will be presented to the user while decrypting from the content key extracted from the header.
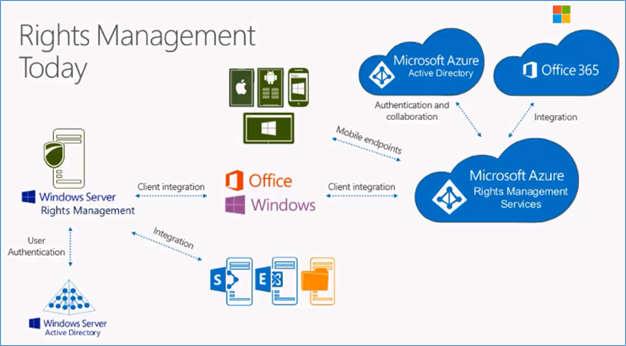
This is a common diagram which represents the Windows rights management integration with Azure Rights Management.
![]()
Azure RMS to Azure Information Protection
AIP is Azure RMS plus few things more. As described earlier Azure RMS provide Encryption, Access Control, and Policy Enforcement from protection view, Monitoring perspective it’s providing Document Tracking and Document Revocation. To complete the lifecycle of data, Microsoft has added Classification and Labeling to the Azure RMS and rename it as Azure Information Protection.
![]()
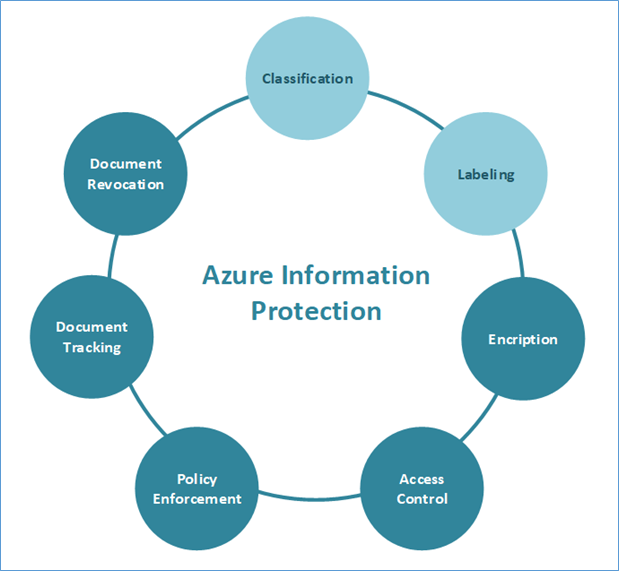
What are Classification and Labeling?
Classification is used to identify data according to the relevance of your organization. These can be categorized into sensitivity levels such as confidential, official use, restricted and public. Labels are created according to this classification. It will define what kind of a protection is applied to the data. By default there are few labels created such as Private, Personal, Public, and Confidential. In AIP you can create your own custom labels.
In Example If finance division regular deals with few banks, you can create a label adding the email domains of those banks and publish the label only to the finance division users. As referred in that scenario, labels are tags, when you deploy AIP client to a computer, Microsoft Office, Outlook, and other Microsoft apps get these predefined labels. Not only office apps, but Windows right-click menu also gets populated with these labels while enabling you to add a label when you send an email, save a document or create a file in your local machine.
![]()
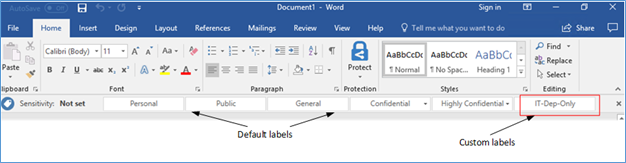
Labels are applied according to the classification, data can be classified according to following methods
Automatic – data will be classified automatically according to the rules set by the organization, in the example, if the file is containing credit card number, a file will be classified as a confidential and confidential label applied. AIP P2 license required.
Recommended – data will be classified according to the rules but prompt the user as the recommended classification.
Manual – the user has to select the label according to the relevance of the data.
Reclassification – classification is done by Azure, but it lets the user override the classification.
Licensing and AIP Plans
There two main plans for Azure information protection, AIP Premium P1, and AIP Premium P2. Also with Office 365 E3 and above few features of AIP included. The main difference between both plans is as follows:
AIP Premium P1
Provides additional rights to use the on-premises connectors, track and revoke shared documents, and enable users to manually classify and label documents.
- Included in Microsoft Enterprise Mobility + Security E3
- List Price – 2$
AIP Premium P2
Builds on Azure Information Protection Premium P1 with automated and recommended classification, labeling, and protection, with policy-based rules and Hold Your Own Key (HYOK) configurations that span Azure Rights Management and Active Directory Rights Management.
- Included in Enterprise Mobility + Security E5
- List Price – 5$
Note - Following article describes full features of all the license plans available:
https://azure.microsoft.com/en-us/pricing/details/information-protection/
My aim of this post is to provide a better understanding of Azure information protection and how it’s evolved from Azure RMS. Also, we discussed on underline technology and AIP data protection mechanism. From my next post, I’m hoping to provide step by step on enabling and configuring Azure Information protection. Catch you soon.
Cheers
Asitha De Silva
References
https://docs.microsoft.com/en-us/information-protection/understand-explore/what-is-information-protection
Ignite 2017 Sessions





