Azure information protection is used to protect sensitive data when sharing internally and externally to the organization. This is my third post on AIP, from my first post of Overview of Azure Information Protection, I discussed what is Azure Information protection, its relation to Azure RMS, how its protection works and licensing. Next is about Implementing and configuring protection of AIP. From this post, I’m going to talk about an important feature called, superuser access and how to implement that to your AIP tenant. First, let’s look why it’s important to enable this feature.
Why it’s important to configure Super User Access in AIP / ARMS
Rights Management is the underline technology in Azure Information protection. It protects data from encryption. A user can send a mail encrypted so only the receiver can decrypt to read it or the user can protect his own data which only he can open. What if the user leaves or management wants to reveal the protected data? This is impossible without user’s credentials unless you have configured master key of decryption, in other words - superuser, to read protected items from any user of your organization. Enabling superuser access is important to face the following situations.
- Employee leaves the organization and company needs to reveal the data
- Remove purposeful or mistakenly added protection
- Data needs to be accessed by government or compliance audit purpose
- IT administrators want to remove the current protection policies and add new protection to data
- Other services such as DLP, Anti-malware need to access the data for inspection purpose.
Configuring Super User for AIP
Superuser is not enabled by default. You can enable this at any time and add a role to selected admin users or service accounts. It is also possible to add a domain group and add relevant users to this group from active directory. but according to TechNet and Microsoft suggest to add users individually by command rather than adding users to the group, this will make superuser decrypt the data immediately.
Use the following sequence to enable and add super users
- Enable Super User feature
Enable-AadrmSuperUserFeature
- Add Users to Super User
Add-AadrmSuperUser
- Add Groups to Super User
Set-AadrmSuperUserGroup
Step by Step Configuration
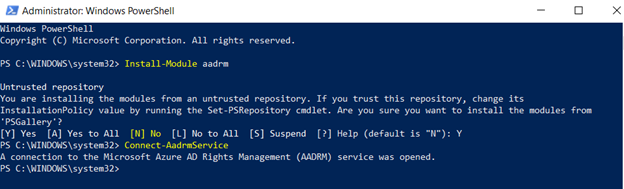
- Open PowerShell as Administrator and connect to AADRM services using global admin credentials. If the AADRM module is not installed, install and import AADRM module
Install-Module AADRM
Import-Module AADRM
Connect-AADRMService
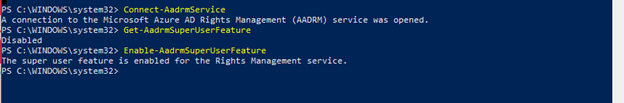
- After connecting to AADRM check superuser feature already enabled from
Get- AadrmSuperUserFeature - Enable the superuser feature from
Enable- AadrmSuperUserFeature
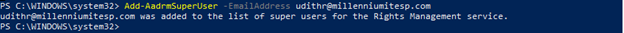
- After adding the superuser, this user has full access to all the protected files. The user can open and edit permissions.
Useful tips for Superuser Feature
- Superuser can be enabled at any time and it can open data encrypted long before feature enablement. So, it’s not necessary to enable or define superusers for the organization. You can always do it when required.
You can disable super user feature by- Disable-AadrmSuperUserFeature (PowerShell)
- Enabling super user feature and defining users can be done by using global permissions of the tenant. So any person with global admin permissions can enable and define super users (or themselves) for rights protection and decrypt all files of the organization protect. So, it’s important to restrict and monitor the administrators with global admin permissions.
- Superuser access can be monitored by following
- Superuser enabled user list - Get-AadrmSuperUser
- Superuser enabled group list - Get-AadrmSuperUserGroup
- adding or removing super users are logged and can be audited by - Get-AadrmAdminLog
- superuser actions (decrypt files) can be monitored by – usage logging
Hope this post is useful
Cheers
Asitha De Silva



