Microsoft Intune helps organizations provide their employees with access to corporate applications, data, and resources from virtually anywhere on almost any device while helping to keep corporate information secure. It is a Mobile Device Management Solution (MDM) which comes with the Enterprise Mobility Suite.
If you pursuit my previous blog posts, I have talked about Enterprise mobility suit, Intune and Intune mobile management policies. From this post I’m hoping to discuss, how to secure corporate Office 365 emails access in BYOD or Manage device scenarios.
To enable these security options, you need to have Intune and Azure Active directory conditional access policies.
Intune App Protection policy’s
Intune App protection policy enables you to protect data on device applications. You can define the apps and set of policies to control the actions. These protected apps are called managed apps. You can define policies such as prevent cut, copy, save as, screen capture, also you can allow data transfer only within the managed apps. As an example, if the policy targeted to Outlook and Word when you get an MS Word attachment through email, you can only open it using Microsoft Word and cannot move data beyond that.
Azure Active directory conditional access
With Azure AD conditional access, you can fine-tune how authorized users can access your resources. For example, you can limit the access to your cloud apps to trusted devices. When you configure app-based conditional access policies, you can limit access to your cloud apps to client apps that support Intune app protection policies. For example, you can restrict access to Exchange Online to the Outlook app.
Securing Office 365 mail – Scenario
As described above, we will use these two features to achieve the following
- Intune App protection policies will restrict following features in Outlook and other managed apps
- Restrict cut, copy, and paste with other applications.
- Require simple PIN to access Outlook and other manage apps
- Prevent Save as to Device, OneDrive can be configured to save
- Block screen capture – Android Only
- Block managed apps from running on jailbroken or rooted
- Encrypt app data
- Prevent cloud backups
- Conditional access will prompt the user to enroll the device to Intune before configuring email to it.
- Conditional access will restrict access of Exchange Online only to the Outlook app. Or else native Exchange active sync apps will not honor the Intune App Protection policies.
Configuring Intune Protection Policies to restrict access
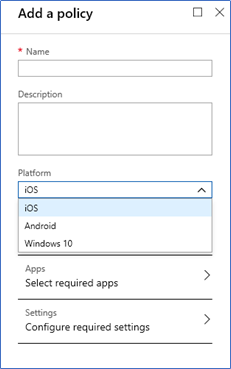
- Log in to the Azure Portal – Intune – Client apps – App protection policies
- Add Policy, select platform from iOS, Android or Windows
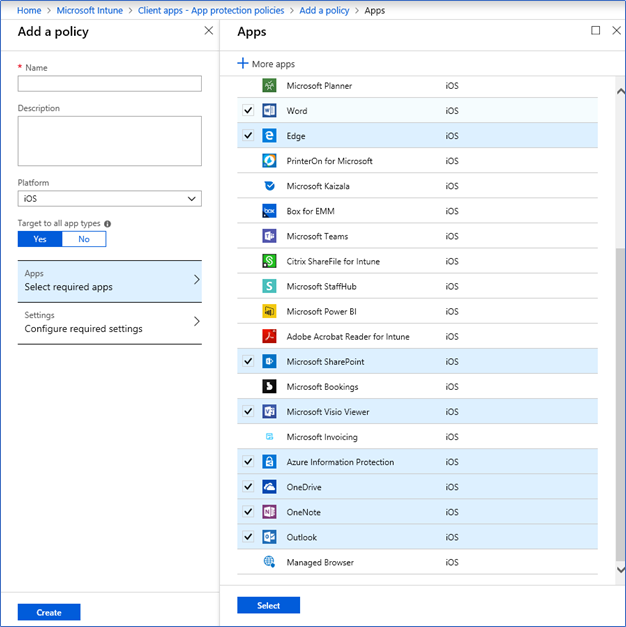
- Select the apps (Manage apps) where you want to add data protection
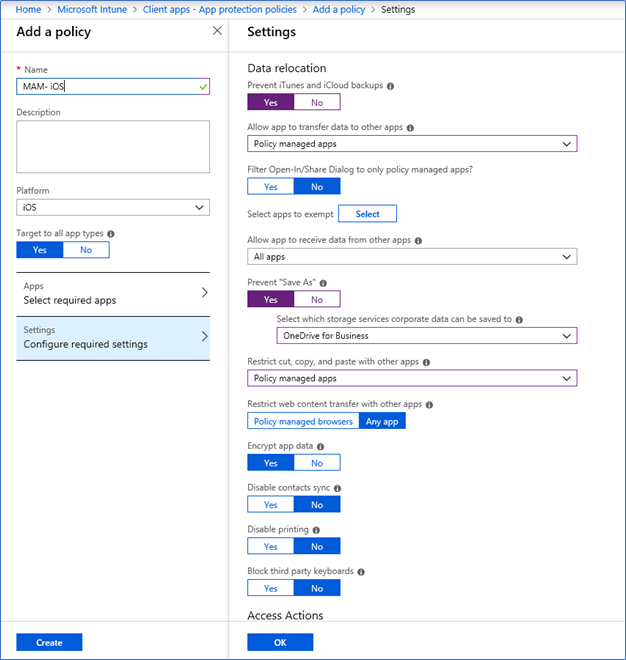
- Select the settings as below, these are the basic settings, however, you can secure more
- Prevent cloud backups
- Allow apps to transfer data to other apps – Policy Managed Apps
- Prevent save as – Only to OneDrive
- Restrict cut, copy, paste with other apps – Policy Managed Apps
- Encrypt app data – Yes
- Require PIN access
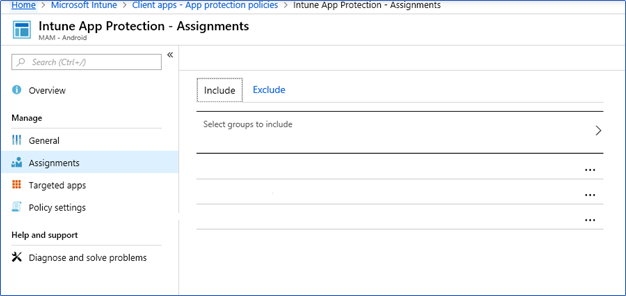
- Save and target the policy to a group of users
- Sync the user from portal to test the policy or wait few hours for it to get applied.
Configuring Conditional access policies to allow only enroll devices and Outlook App can access corporate Office 365 emails
- Log in to the Azure portal – Intune – Conditional access – New Policy
- Name the policy and select the user group should be assigned
- From cloud apps select Office 365 Exchange online
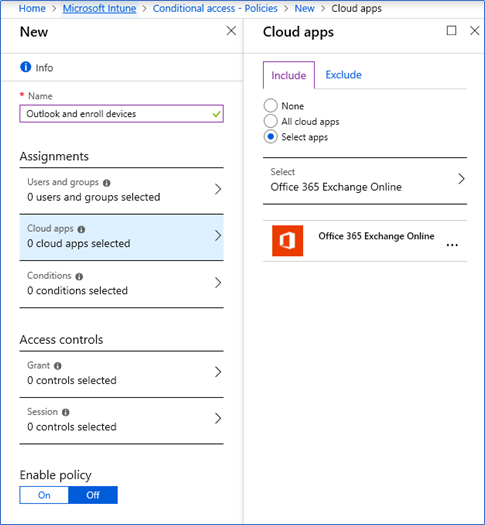
- From the conditions tab select the following
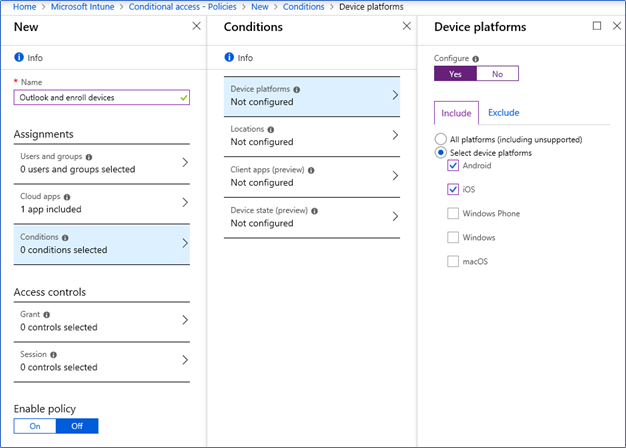
- Device platform – select Android and iOS if you want to apply this only to mobile devices,
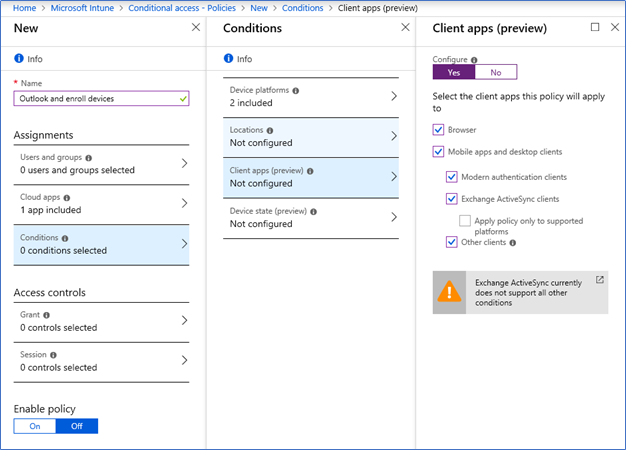
- From client apps select Browser, Modern authentication clients, Exchange active sync clients and Other clients.
- From access control click Grant tab, and select
- Require device to be marked as compliant – this policy will make sure the device is enrolled.
- Require approved client app – this policy will make sure Outlook app and Manage browser will only work as Office 365 mail client.
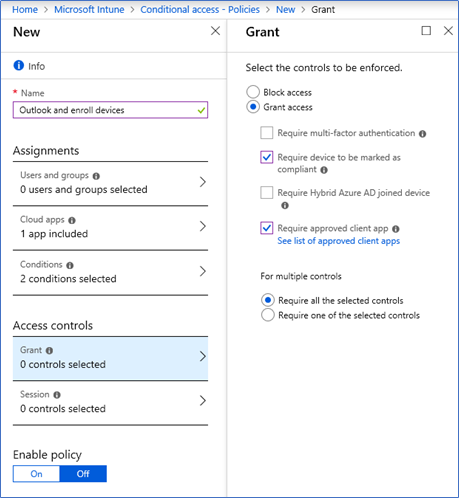
- Click Enable policy
Conditional access policies are a bit faster than the MAM policy, but again it will depend on how many users you have targeted the policy. After the policy has kicked into the device. If the device is already configured the mail you can see will not come to the native client, also user is prompted to enroll the device to receive the office 365 emails.
Hope this post is useful
Cheers
Asitha De Silva








