
Introduction to MDM
When it comes to IT related security concerns of an organization, the IT department has the responsibility to safeguard the internal network from both internal and external threats. Network administrator’s duty is to configure the computers attached to the network including firewalls, software implementations, user access levels etc. With the influx of mobile devices in the workplace, new types of security concerns emerged as a result of that. Since mobile devices use a different approach than traditional devices, new methods need to be implemented to manage the enterprise functions. It’s easy to manage the company owned devices within the internal network. As emerge of mobile technologies, circulation of both company-owned devices and personal mobile devices increases in the workplace and these devices often use the different service providers and operating systems. This complex arrangement of mobile devices made the traditional device management processes obsolete. Therefore, as a solution to these newly arising issues, organizations shifted to Mobile Device Management (MDM) systems from traditional device management methods. MDM is security software that helps to manage the mobile devices of employees within an organization. MDM software is also considered as the main part of Enterprise Mobility Management (EMM). MDM allows IT admins to deploy all corporate applications and policies to mobile devices including smartphones, tablets, mobile printers, some IoT (Internet of Things) devices. Then, IT admins are able to control the areas like what type of information employees can access? What types of mobile apps they can use? Authorized networks to connect etc. These are some of the important features that include in every MDM software
- Mobile Policy Management
- Security Management
- Inventory Management
- Management of Mobile Applications
- Service Management
With the rapid growth of mobile device usage, employees are allowed to take their personal mobile devices to a workplace in order that they could use their own devices for work purposes. This new policy, also known as BYOD (Bring your own device), permitted employees to connect to the corporate network and also could access the sensitive business information. But these devices have different service providers and also run on multiple operating systems. This complex nature of work environment exposed the corporate network to new security risks. It’s impossible for the IT department to monitor each device individually, therefore, deploying an MDM software would be an ideal solution to avoid the risk factors. Overall, MDM solutions will secure the corporate network from security risks, ensure the safety of sensitive business information and by that, it will improve the efficiency and productivity of employees.
Why MDM is important for business?
It’s inevitable the influx of mobile devices to the workplace after the rapid growth of mobile technologies. Adaptation of mobile technologies to the work environment brings enormous benefits to the businesses. Mobile technologies streamline the business processes by permitting employees to work from remote locations and it affects positively to the in-house operations of workplace too. Also by deploying BYOD concept, organizations could gain many benefits including, lessen the purchasing cost of mobile devices, getting quick responses from employees and since, employees use their own mobile devices, they are well familiar with the devices, consequently they will cause fewer troubles to the IT department. With all these pluses, BYOD policy raised some critical security issues for organizations as well, but it’s almost impossible to ban the use of mobile devices at the workplace as a solution. Therefore, it’s important to implement some kind of technical solution to overcome the risks. Mobile Device Management software is the ideal solution to ensure the protection of corporate data while allowing employees to use mobile devices. MDM uses a centralized platform to manage all the mobile devices including BYOD devices and company-owned devices.
Before implementing an MDM solution for organization, it’s essential to consider about the areas including how new system will effect to the existing security system? Will the solution fit with company policies? What type of business data can access from their employees’ devices? What type of architecture should use when deploying the solution? Etc. Also, a good MDM solution provides features such as:
- Register new mobile devices with the system by creating user profiles and define user access levels.
- Configure the devices according to the corporate policies. Data should be encrypted and protected with passwords.
- Monitoring user activities 24/7 and manage the device applications.
- Protect the corporate data from harmful incidents including unauthorized access, data breach, hacking etc.
- Ability to wipe data remotely, in case of loss or theft of devices.
- Protection from malware, spyware and viruses.
- Provide geofencing capabilities.
- Enable to take backups from devices and restore the data in case of damage or data loss.
- Ability to troubleshoot the devices remotely.
- Stop access to corporate data and wipe the sensitive information from personal devices, in case of termination of work.
How MDM works
Selecting the right architecture is important before deploying the MDM solution. You can choose either cloud-based or on-premises MDM solution for your organization. Compared to the cloud-based solutions, on-premises MDMs requires more employees and need to have good technical knowledge to manage the system.
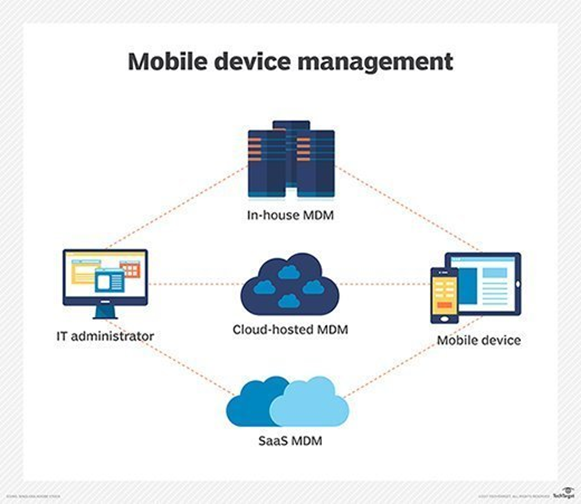
When deploying an MDM, it should be configured on both MDM servers and client devices or in this case, employees personal devices. MDM offers a management console to handle the operations from the IT department side and client apps to install on employee devices. Once the IT admins configure the server component (MDM server), it gathers the information from a client device (MDM agent) and then sends policies over the air to the client device in order to apply them on the device. Some MDM systems are automated to detect the new devices which connect the corporate network and apply corporate policies in order to continue the connectivity.


