Azure AD Password protection eliminate weak passwords and custom passwords that may relate to the organization. My previous post of Azure AD Password Protection and Smart Lockout, I have discussed what is password protection, how it works, its architecture and the required licenses. From this post, I’m hoping to discuss step by step on implementing the password protection feature while addressing Microsoft best practices.
Deploying Password protection, On-premise Hybrid
Azure AD password protection can be deployed as cloud only or Hybrid when you have an on-premise Active directory. In this scenario, weak password list where you define in Azure will be sync to local active directory password policy and those passwords will be denied. When implementing it in on-premise following two components should be installed.
Azure AD Password Protection Proxy
You need to install the Proxy in a server where domain joined and have access to the internet. Proxy service will securely connect to the Azure Password Protection service in the cloud and forward the requests to the domain controller agents and receive them back. Proxy service will make sure you don’t need Internet connectivity on domain controllers to implement password protection. After installing the proxy, you need to register it with Azure using few PowerShell commands.
Azure AD Password Protection Agent
Password protection agent needs to be installed in Domain Controllers. This agent will connect to the proxy service and retrieve the policy forwarded by Azure. You can deploy agents to every domain controller to retrieve the password policy, however still, password policy will be distributed from SysVol replication to every domain controller if the agent is deployed to one Domain Controller of the Domain.
After installing the Password protection agent, you need to restart the server. Any modification from the Azure side will be synced to local by every hour.
Some important facts
- Users should have Azure AD Premium P1 or P2 licenses to use this feature
- 1000 custom passwords are supported
- After enabling the service password policy will be updated by 500 different weak passwords as banned passwords. This list is hidden and maintained by Microsoft.
- The domain should have at least one windows server 2012R2 Domain Controller.
Deploying Azure AD Password Protection Proxy
- Download the both Proxy and DC agent from Microsoft Download Center
https://www.microsoft.com/en-us/download/details.aspx?id=57071
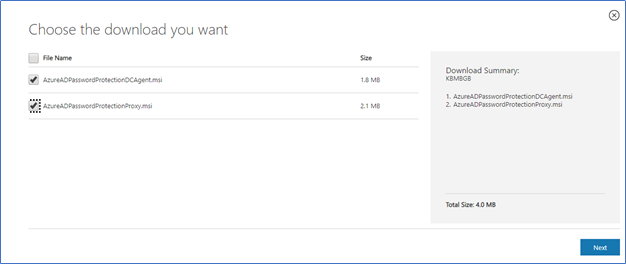
- Copy and install the Proxy agent on the server with internet connectivity
Register the Password Protection Proxy service
After installing the proxy agent, you need to register it with the Azure Password Protection service, for this, you need Azure global admin account and domain admin access for the root Domain. With that follow the below steps
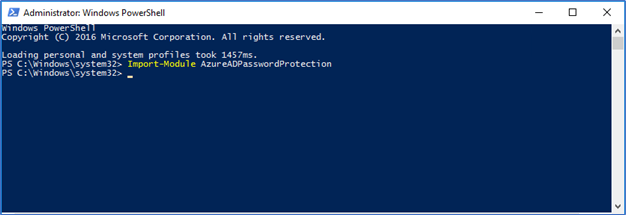
- To Import the Azure AD Password Protection module run the following command in PowerShell
Import-Module AzureADPasswordProtection
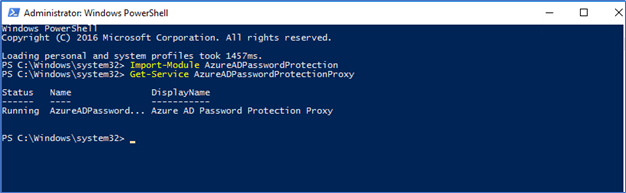
- Make sure the Proxy service is running
Get-Service AzureADPasswordProtectionProxy | fl
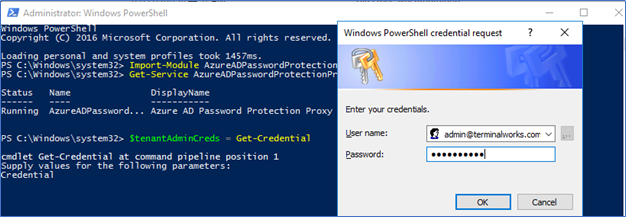
- Next register the Proxy service using Azure global admin credentials
$tenantAdminCreds = Get-Credential
Register-AzureADPasswordProtectionProxy -AzureCredential $tenantAdminCreds
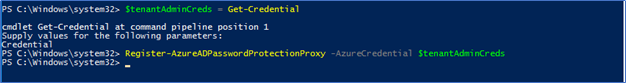
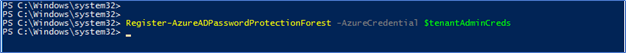
- Next, to register with local active directory forest, you need to run this command using domain admin or forest admin credentials if you have multiple domains. Use -ForestCredential switch to provide credentials when you are not logged to the server using the same credentials
Register-AzureADPasswordProtectionForest -AzureCredential $tenantAdminCreds
Installing Azure Ad Password Protection in domain controllers
- Login to the domain controller and run the setup of previously downloaded
AzureADPasswordProtectionDCAgent.msi
- After installing the agent Domain controllers need to be restarted.
Configure Azure AD Password Protection
After configuring the Hybrid connectivity to local AD or before you can configure the Password protection from Azure Portal,
Azure Portal – Azure Active Directory – Authentication Methods - Password protection (Preview)
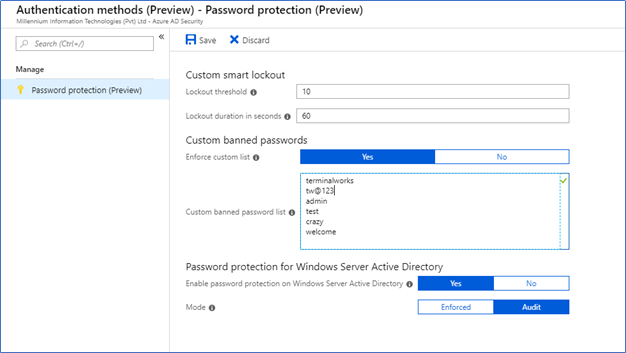
You can configure many passwords here. But please be selective, you don’t want complains from users saying they cannot set passwords or password is too complex to keep in mind.
Monitoring
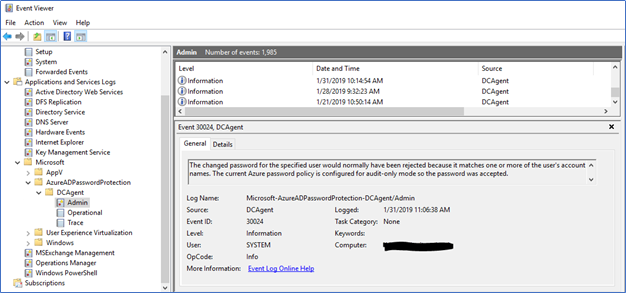
Attempts can be monitored from following event log in each DC
Event Viewer – Windows Events – Application and service logs – Azure AD Password Protection
Hope this post is useful
Cheers
Asitha De Silva












