A local administrator is the default highest privileged account in a windows computer client. This account is created when the operating system is installed for the first time. In a Domain environment, when computers are joined to the Active Directory environment, we tend to forget about this account. And that’s how it’s been with many of the organizations. But this practice has many security risks which are not limited to following.
- Local Admin Account is common to all machines – OS implementation is done by one or few technicians and they tend to stick to a single password.
- Technicians or admins who have knowledge about the local admin password have full access to the machine
- If an external party is able to crack the local admin password, they can access every machine sharing the same password and using attacking methods like session hijacking so they could access other domain infrastructure.
What is LAPS
Local Admin Password Solution also knows as LAPS is released by Microsoft to address the above issues. It was released in 2015 and frequently updated. LAPS provides centralized storage for local administrator passwords in Active Directory without additional resources. It resolves this issue by setting a different, random password for the common local administrator account on every computer in the domain. Domain administrators using the solution can determine which users, such as help desk administrators, are authorized to read passwords.
- Automatically manages local administrator password on domain-joined computers
- Password is unique on each managed computer
- Password is randomly generated
- All passwords are securely stored in AD infrastructure
- Built upon only on AD infrastructure, no additional resources required.
- Easy configuration and administration.
Why LAPS?
Using Group Policy Preferences, we were able to update the password of any local user, I do remember I used to do this very often. Create a new GPO, create a new local user, add a strong password, add that user to the local administrator’s group and finally disable the local administrator account and deploy the GPO to the domain joined computers. It was easy and convenient. Later there had been security concerns storing passwords in GPO and Microsoft had to address this from a Security bulletin. MS14-025: Vulnerability in Group Policy Preferences could allow elevation of privilege, that removes this functionality. After you installed this patch or Operating system which is newer than this patch, GP Preferences password fields are disabled as follows. So you are safer from the pass hash attacks targeted to GPO's.
This is where LAPS come in. it will provide much more secure functionality which you are safer from the pass hash attacks.
LAPS Architecture
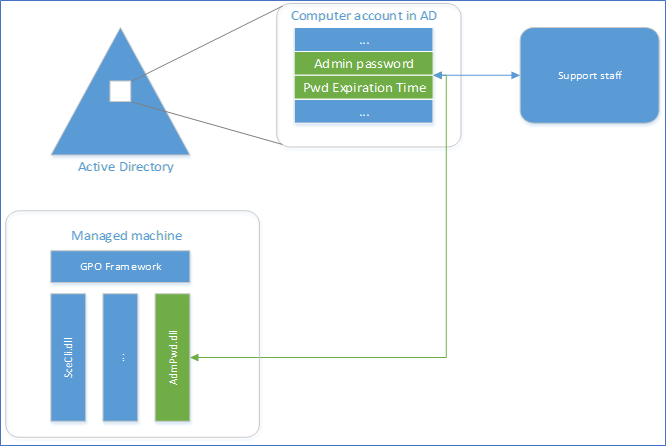
The core of the functionality of the solution is implemented as Client-Side Group Policy Extension (CSE), installed on every managed computer. This can be deployed as an MSI which will do the random password generation and event logging. AD schema needs to be extended and Password repository is implemented using newly defined attributes in the AD schema. A GPO will be responsible for Triggering the execution of CSE on the managed computer and managing the solution. Passwords can be retrieved from fat UI client, PowerShell or Active Directory Users and Computers (ADUC),
Security and Management of LAPS
Security
- A random password that automatically regularly changes on managed machines
- Effective mitigation of Pass-the-hash attack
- Password is protected during the transport via Kerberos encryption
- Password is protected in AD by AD ACL, so a granular security model can be easily implemented
Management
- Configurable password parameters: age, complexity, and length
- Ability to force a password reset on a per-machine basis
- Security model integrated with AD ACLs
- End-use UI can be any AD management tools of choice, plus custom tools (PowerShell and Fat client) are provided
- Protection against computer account deletion
- Easy implementation and minimal footprint
Supported Configurations
Supported Operating System
Windows 10, Windows 7, Windows 8, Windows 8.1, Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016, Windows Server 2019, Windows Vista
Active Directory: (requires AD schema extension)
- Windows 2003 SP1 or later.
Managed machines:
- Windows Server 2003 SP2 or later, or Windows Server 2003 x64 Edition SP2 or later.
Note: Itanium-based machines are not supported.
Management tools:
- .NET Framework 4.0
- PowerShell 2.0 or later
Hope you have a better understanding of the local admin password solution from Microsoft and what it provides you to your organization. From the next post, I’m hoping to write about Implementing LAPS steps by step. Stay tuned.
Cheers
Asitha De Silva
References
Microsoft docs
LAPS whitepaper plus documentation.


