Today's world security is not a choice, it’s something you must have. Microsoft Azure Security defaults provide you with a set of preconfigured security settings to minimize common attacks including password spray, replay, and phishing attacks.
Over the time Microsoft introduced many security procedures and settings to address various security concerns and possible attacks. Introducing multifactor authentication is one of the top identity security mechanisms. Using a second factor such as SMS, Pin code or app notification reduced more than 99.9% of organization account compromise. Moreover, disabling legacy authentication reduces compromise risk and able to completely put stop to password spry attacks which happen through legacy authentication. While analyzing these results Microsoft decided to enforce these security settings in a common configuration called security defaults. This helps users to follow common security baseline rather them self-finding and enabling each security setting. Let’s see what settings composed of security defaults.
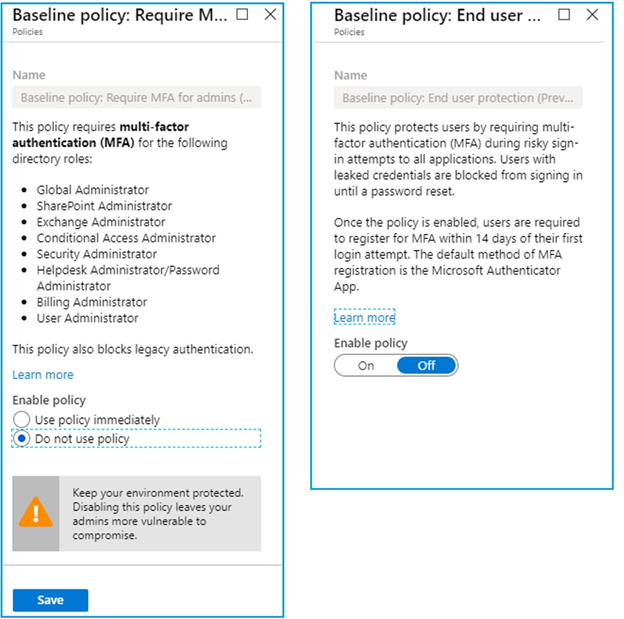
Multifactor authentication enforcement to Administrator roles
Using a second factor of authentication provides you with an additional layer of protection that makes you safe from many common password attacks. Azure Multifactor default/free version provides the second factor as the Microsoft authentication app. This is an app available in android and iOS stores, which is very easy to install and use. When azure multifactor is enabled, 14 days given to the users to register themself, after the 14 days, multifactor is enforced and users unable to login without the other factor. Users can self-register to the authenticator app without much involvement of the admin staff.
When enabling security defaults, you are enforcing all the portal admins to use Azure multifactor. This is to protect and safeguard the privileged accounts. The following admin roles are enforced.
- Global Administrator
- SharePoint Administrator
- Exchange Administrator
- Conditional Access Administrator
- Security Administrator
- Helpdesk Administrator/Password Administrator
- Billing Administrator
- User Administrator
Multifactor enforcement to all users
Not only administrator accounts, but attackers also tend to attack normal user accounts because they are vulnerable and easy to expose. After gaining access to a basic account attacker can start exploring more privileged accounts. So the best option is to secure all user accounts the same way you treat privilege admin accounts. Azure multifactor can enforce to all users using security defaults. Users must register themself to the authentication app and when every required second factor will be prompted.
Block legacy authentication
All authentication methods do not support modern authentication. Without modern authentication azure, multifactor authentication will not work. to facilitate the multifactor, legacy authentication should be disabled. With security defaults following legacy authentication protocols are disabled.
- Older Office clients that don't use modern authentication (for example, an Office 2010 client).
- Any client that uses older mail protocols such as IMAP, SMTP, or POP3.
Safeguarding privileged actions
Azure services are managed through Azure portal, Azure PowerShell and Azure CLI. Using these API’s privileged user can alter tenant-wide configurations, such as service settings and subscription billing. So, it’s very risky to use these management tools with single-factor authentication. After you enable security defaults in your tenant, any user who's accessing the Azure portal, Azure PowerShell, or the Azure CLI will need to complete additional authentication. This policy applies to all users who are accessing Azure Resource Manager, whether they're an administrator or a user.
Implementation Considerations
Before implementing you need to consider, security defaults support the second factor only using Microsoft Authenticator app notifications. However, if you want to use text to phone, phone call or hardware token you need to use conditional access which comes with Azure AD paid versions such as Azure AD Premium P1 or P2.
Conditional Access will provide more granular control over the multifactor authentication. conditional access policies can be targeted to specific users or groups. Also, you can exclude users or groups from the policy. However, you can use either conditional access or security defaults. If you are already using conditional access, then the security defaults will not available for you. Also, you can use security defaults until you move to conditional access.
Implementing Security Defaults.
- To enable Security defaults, login to the Azure Portal – Azure Active Directory – Properties
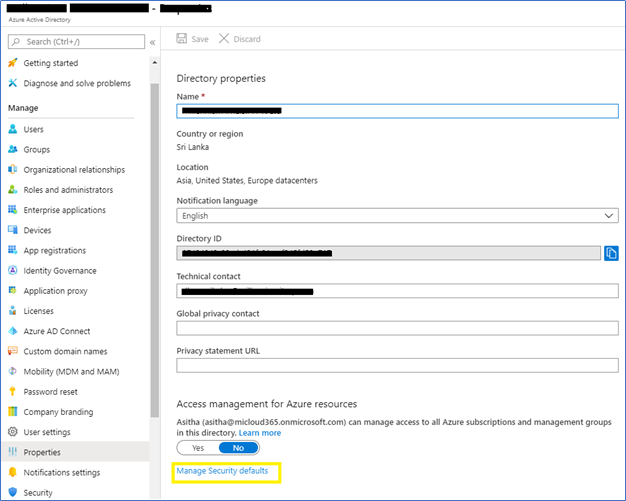
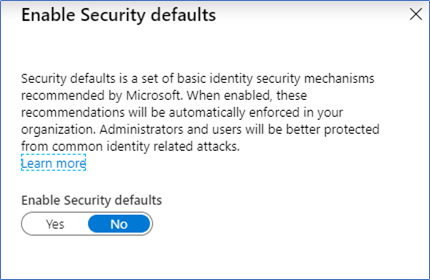
- Click Manage Security defaults, and select Enable Security Defaults
Conflicting with Baseline policies
If you aware, Security Defaults released to replace the Baseline conditional access policies. Microsoft announced they will stop enforcing them on Feb 29th and send a notification to the customers who are still using baseline policies to move to Security Defaults.
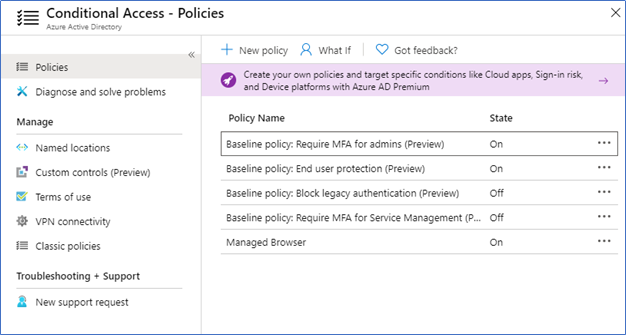
If you are using conditional access policies, you are been prevented of enabling security defaults,
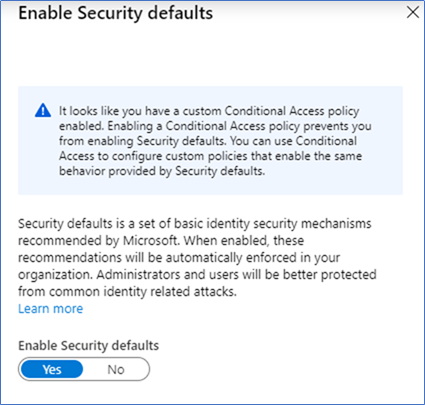
Remove or disable any conditional access policies, and then only you can enable security defaults, in my case I already enabled Baseline policies of MFA Admins, MFA All users and Disabling legacy authentication. You can click the policy and change the enablement to Do not use the policy as following snapshots.
Conclusion
Security defaults containing common security procedures mainly involve in enabling MFA for Admins and All users while disabling legacy authentication to support Azure multifactor authentication. It’s a replacement to Baseline conditional access policies, so you can either use conditional access policies or security defaults. If you have Azure Active Directory Premium directory it's better to have conditional access to enforce MFA to users because conditional access supports more control over MFA settings. However, if you are using free version of Azure Active directory better go and enable Security Defaults which will protect you from a vast variety of common attacks.
Hope this post is useful
Cheers
Asitha De Silva





