As of today, when I’m writing this article, the whole world experiencing a pandemic situation with the continuous spreading of COVID-19 Virus. Millions of people have moved to remote work and working from home. This is very unexpected, Sudden and we all thought it would be for a few weeks but it looks like social distancing and work from home will continue till the end of this year. Most organizations are not yet ready for working remotely, however, they are getting there with limited budgets and funds. Moreover, they must assess and manage security concerns when people working in the remote.
It is very important to make sure that the devices are protected in all possible ways starting from windows security patching, antivirus, and other security tools available on the device. from this article, I’m targeting organizations that are already having SCCM to deploy Microsoft updates through the internet to their work from home computers. Basically, utilization VPN split tunneling.
Using SCCM there are few options to deploy updates through the internet.
- Use Cloud Management Gateway and Cloud distribution point.
The cloud management gateway (CMG) provides a simple way to manage Configuration Manager clients on the internet. By deploying the CMG as a cloud service in Microsoft Azure, you can manage traditional clients that roam on the internet without an additional on-premises infrastructure.
- Use VPN to distribute updates.
100% of SCCM traffic will go through a VPN. Including software updates, management policies, agent communication, etc. although you can configure BITS in data transfer, this can flood your VPN bandwidth
- Use VPN split tunneling with boundary groups to direct update download to MU.
VPN split tunneling needs to be configured where all the Microsoft Update URLs will connect to direct internet without coming to the on-premises datacenter. Clients get management policies, agent communication from VPN connection, and for software updates, it will connect to the Internet.
From this post, we are discussing the 3rd option,
Using VPN Split tunneling with boundary groups to download updates from Microsoft Update sites.
This is the easiest option to implement which does not require any architectural changes to the current SCCM environment. Also, there are no new costs associated. However, it will depend on the following prerequisites.
You should have
- VPN with split tunneling possible
- SCCM client should be already deployed to connecting client PC’s
- Healthy Software Update point in SCCM
- Boundary group for VPN IP range and separate Distribution point.
- On-premises AD DNS TTL
SCCM update deployment can be configured to re-direct to Microsoft Update services if it cannot find the published updates in the relevant distribution point. So, we can leverage this feature to deploy the updates to the work from home PCs without many configurations. You need to configure boundary groups consist of VPN IP ranges to route all clients to empty distribution points. When clients cannot find the content it will try to connect to the internet. Then you configure the split tunneling in VPN where MU sites can access directly, SCCM will facilitate to download the content through the public internet. Let’s see how we configure this.
Configuring VPN Split tunneling to route traffic to Microsoft Updates services
When configuring split tunneling on your VPN, you can configure the following URL to connect to the internet without coming to the corporate network. These are the URL’s which you allow in firewall when giving access to WSUS or SCCM to get updates from the internet. Refer – (here)
Software Updates
- http://windowsupdate.microsoft.com
- http://*.windowsupdate.microsoft.com
- https://*.windowsupdate.microsoft.com
- http://*.update.microsoft.com
- https://*.update.microsoft.com
- http://*.windowsupdate.com
- http://download.windowsupdate.com
- http://download.microsoft.com
- http://*.download.windowsupdate.com
- http://test.stats.update.microsoft.com
- http://ntservicepack.microsoft.com
Manage Office 365
- officecdn.microsoft.com to synchronize the software update point for Microsoft 365 Apps for enterprise client updates
- config.office.com to create custom configurations for Microsoft 365 Apps for enterprise deployments
Windows 10 Servicing
- download.microsoft.com
- https://go.microsoft.com/fwlink/?LinkID=619849
- dl.delivery.mp.microsoft.com
Configuring Boundary groups and Distribution points.
As I mentioned earlier, you need to create a Boundary Group specific for VPN IP ranges. And this boundary group should only refer to a Distribution point with no updates. My advice is to create an empty new DP, so your existing configurations will not affect.
- Login to the SCCM Console – Administration – Site configurations – Create a new site system.
- Select Distribution point and complete the wizard to create the DP
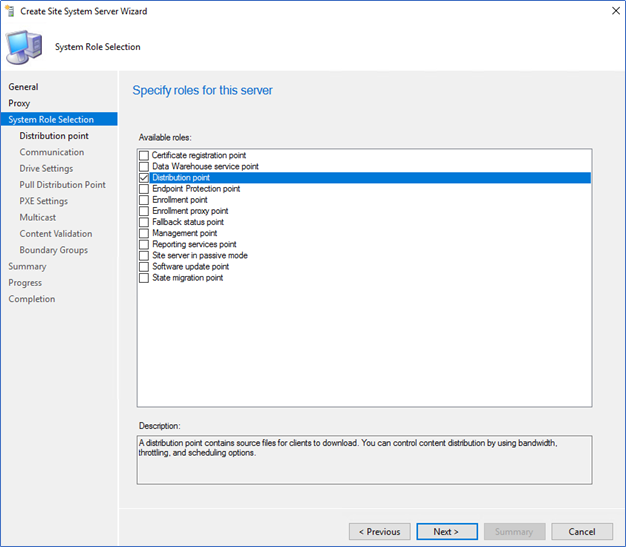
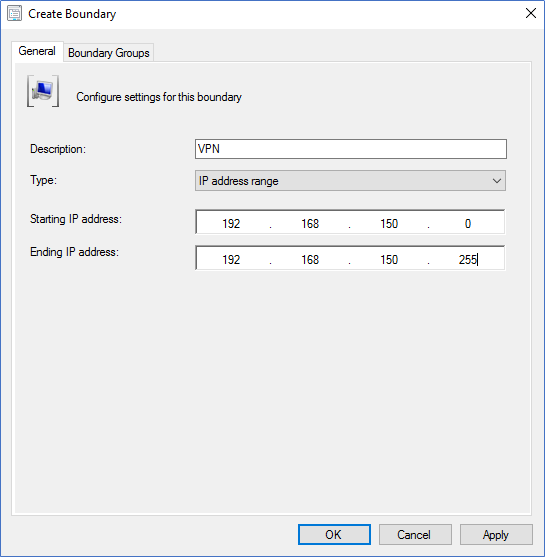
- Next, go to Boundaries – Create Boundary and create according to your VPN IP ranges.
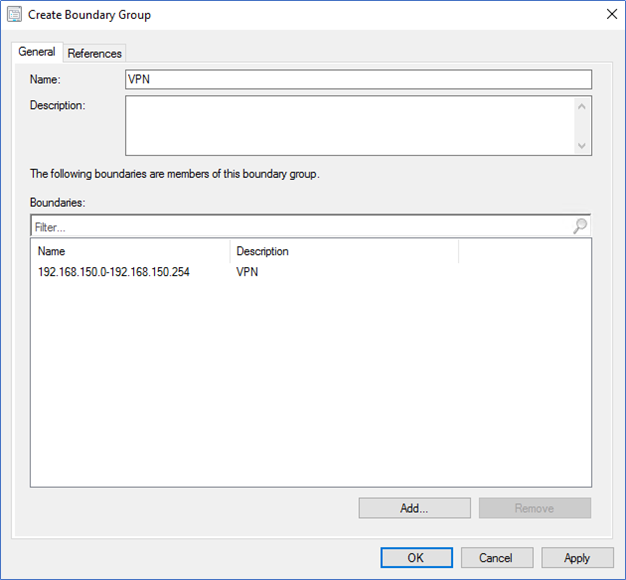
- Then create a Boundary Group to include all the VPN boundaries.
- In References tab select the DP where we created earlier
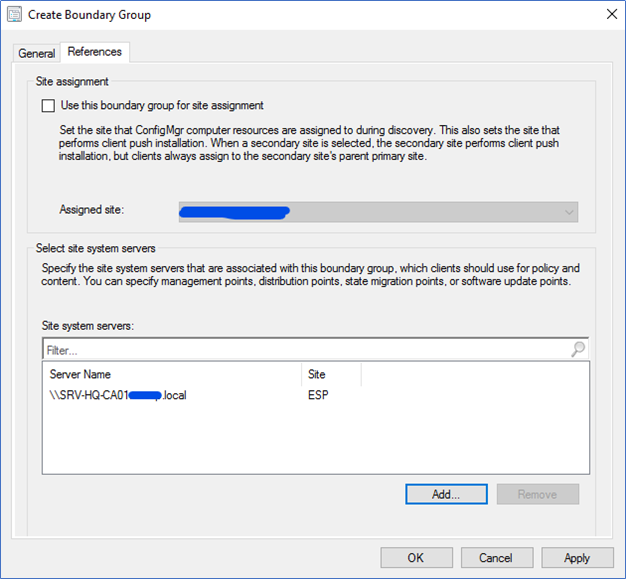
- After creating the BG, click Properties of the BG and configure the fallback relationships. You need to make sure your Boundary group should not fall back to any other Site systems. To configure that, click Add and select other Head Office boundary groups and select Never fallback.
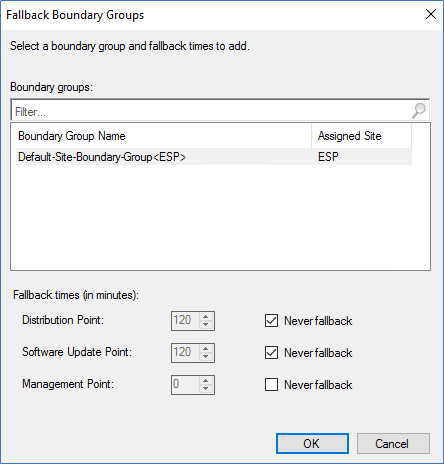
- In Options, remove tick on “Allow Peer downloads in this boundary group” because peer cache is not relevant in this scenario.
Deploy Updates
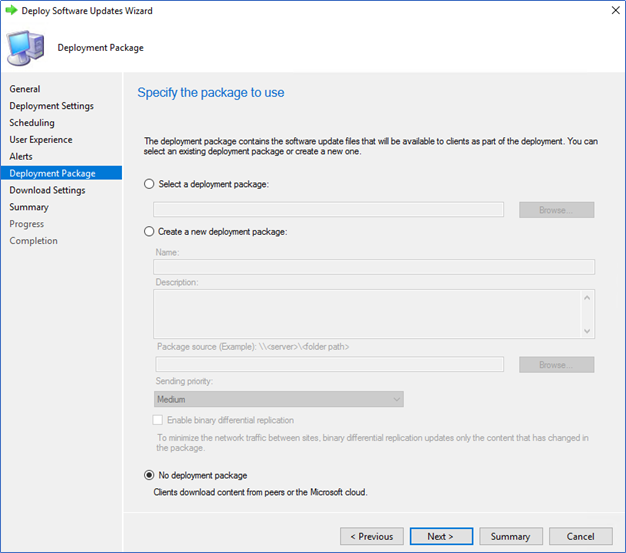
When deploying updates, you can follow the same process where you are doing before. However, make sure to skip distribute updates to Distribution Point. You can select the updates, create, or add to a software update group and Deploy it without selecting a Deployment package. When deploying tick No Deployment Package option as follows
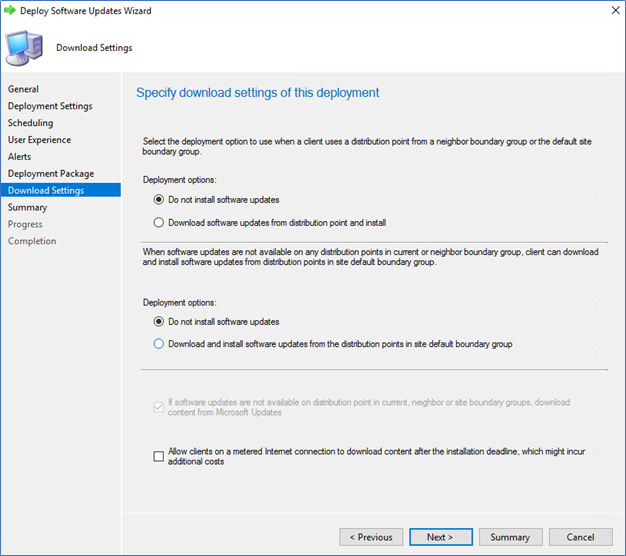
In download settings, tick Do not install the software updates option.
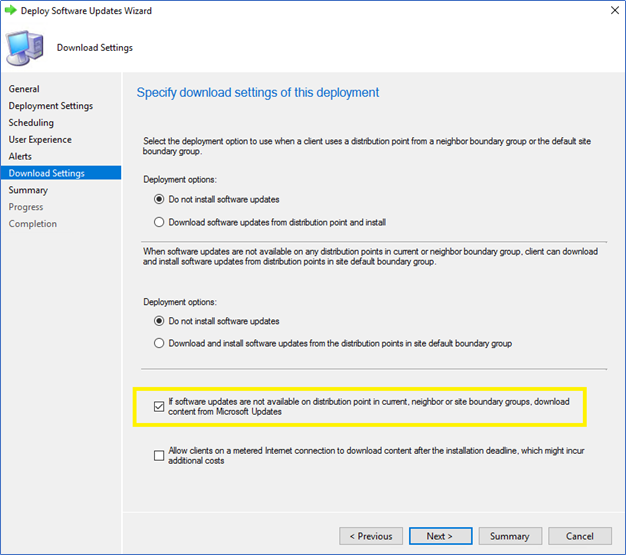
If you are deploying a Software Update group which is with Deployment Package, make sure to click Download contents from Microsoft Updates.
Monitoring from end-user end
Before pushing updates this way to all the users, it's better to test it with few users. From the following log files in the client end, you can find a source of updates to confirm it downloaded from the Internet.
ContentTransferManger.log
CAS.log
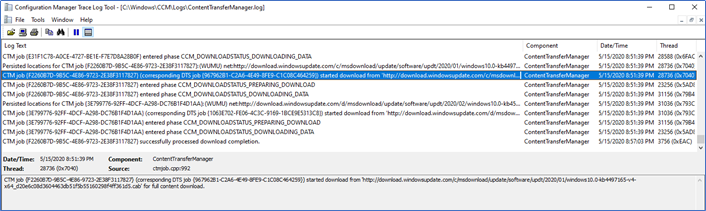
Also, to make sure, I disconnect the VPN when transferring started and check whether the update is still downloading. UpdateDeployment.log
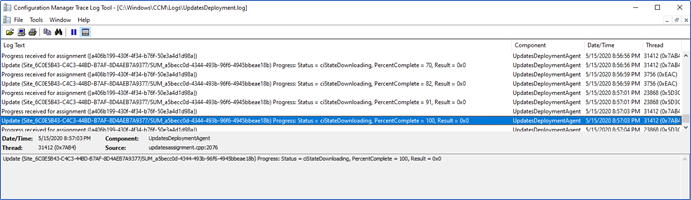
I hope this little configuration in SCCM will help you to deploy updates to Remote machines using a VPN.
Hope this post is useful
Cheers
Asitha De Silva










