
What is DMZ ?
Typically, an organization’s computer network can be divided into two parts; internal network and external network. Internal network, also known as Intranet or Local Area Network (LAN), shares the resources inside the organization and only the internal users can access them. External networks (e.g. internet) don’t have such restrictions; therefore anybody can access the publicly available resources. DMZ or Demilitarized Zone is an intermediate or sub network that place between the untrusted external network and the secure internal network. It can be set up as either a logical or physical network.
This term Demilitarized zone comes from the war neutralized area where set up between North Korea and South Korea at the end of the Korean War. DMZ lies along the geographic boundary between the two countries. Likewise, DMZ acts as a buffer zone between the internal and external networks and by that, it disintegrates the direct connectivity between them. It also known as a perimeter network and it adds an extra layer of protection to the networks which contain sensitive corporate data such as confidential business records, software source codes, financial data, customer information etc., from the untrusted outside world. While internal network resources securely lie behind the DMZ, external entities directly interact with the front end DMZ sub network. Therefore, DMZ is an ideal network configuration to manage the public corporate data such as press releases, job vacancies, marketing materials etc. Since the public data is detached from the internal network, external users do not need undergoing strict authorization procedures to obtain that data. Network resources such as web servers with public data, mail servers, DNS servers, authentication services, application gateways, VoIP servers etc., can be placed inside the DMZ. These servers could communicate with both internal LAN and internet, but high-security measures are imposed on LAN side access and firewalls are set up in order to scan all the traffic entering to the internal LAN. When the attackers try to breach the organization’s network, often their attempts will be limited to compromise of DMZ traffic. As servers in DMZ are being exposed to the public internet, organizations need to cautiously analyze and select the data which are going to DMZ.
It’s a protective approach that put web servers with public data inside the DMZ network. These web servers are allowed to communicate with internal database servers whenever necessary, but accord with the inbound security rules. They could place inside the internal network too, but then it needs to give permission to external users to access the system. This raises some security concerns which lead hackers to infiltrate the internal systems. Internal database servers which contain email data such as login credentials, private messages etc., are not directly linked to the internet. By placing the SMTP servers inside DMZ, organizations can scan the public emails at DMZ perimeter and only the filtered and non-infected emails forward to the internal database servers. FTP servers are used for transfer files between computers; therefore, it’s a best practice to isolate these servers from internal systems and placed inside the DMZs. DMZ networks have strict access restrictions to the internal networks because of their vulnerability to the potential malicious attacks. But, in case of a security breach, there’s a high possibility that hackers got stuck in the DMZ and they need to give another effort to go beyond the DMZ. By that, DMZ ensures that, when a part of the system went down, others functionalities remain intact. Likewise, the purpose of implementing a DMZ network would serve to the host organization in many different ways.
The architecture of DMZ network
Firewalls are the most important elements when constructing the DMZ networks. When creating a DMZ, organizations can adopt two approaches based on their requirements; single firewall or three-legged model and dual firewall model. Later, these basic models can be transformed into more complex architectures. Firewalls are configured based on the nature of the connectivity between network elements. In DMZ model, different types of traffic flows can be observed; external network - DMZ, DMZ – internal network and external network – internal network. When the firewall rules are set up, it needs to be specified the ports which accept the traffic from public internet and only the permitted traffic should allow to the DMZ and internal network. Dual firewall model is widely used when implementing DMZs.
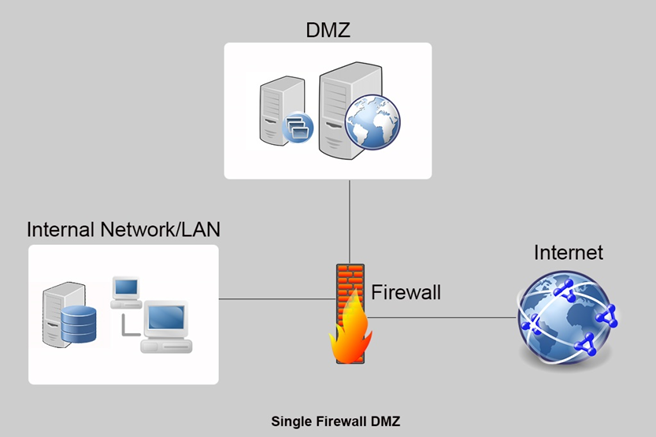
Single firewall DMZ model
As the name suggests, the single firewall model can be designed with a single firewall and it requires a minimum of three network interfaces to form the DMZ. The external network that connects to the public internet is formed from the first network interface, internal network or LAN is formed from the second network interface and finally, DMZ is created from the third network interface. Since a single firewall is used for this model, this is the cost effective option, but it requires to managing both DMZ and LAN traffics and access requests.
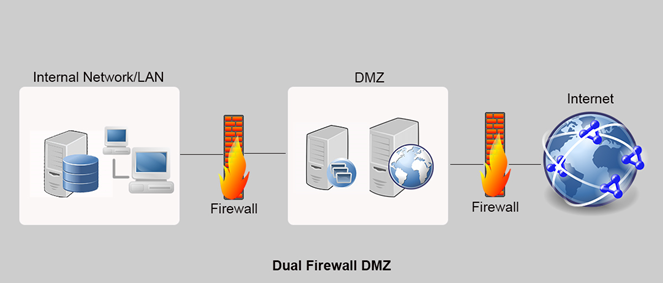
Dual firewall DMZ model
Dual firewall model is considered a more secure approach when creating a DMZ. The first firewall is called Front-end or perimeter firewall and it’s configured to manage only the traffic receives from the public internet to the DMZ. The second or Back-end firewall is configured to manage the traffic from DMZ to the internal network. This model has surely increased the security of the system and it can be further improved by selecting two firewalls from different vendors. Because it’s challenging for hackers to infiltrate two firewalls with different security measures.
DMZ network configurations can be used for both home and corporate networks. In-home networks, broadband routers establish the connection between the LAN and the internet. The broadband router acts as a firewall and ensures only filtered traffic enter to the LAN. But, these home routers cannot create a full DMZ network and it just allows one device to expose to the internet, therefore, benefits are limited in home DMZs. By adopting the DMZ model, video game consoles such as Xbox and PlayStation can be solved the connectivity issues. It separates the gaming console from the LAN and removes strict network restrictions on the console. Though many organizations no longer want to use the DMZ after turn into cloud computing, separating some critical network resources from the rest of the network still can be considered as a good security strategy.



