Windows Virtual Desktop is a full cloud Azure-based DAAS/PAAS solution. It is having both features of Remote desktop solution and Virtual desktop solution. WVD offers full desktop virtualization with Windows 10 Images; this has been more enhanced with multi-session Windows 10. Not only desktops, but you can also move your RDS environment to WVD with the same experience while reducing complex deployment components.
Shadow Session is a great feature where the Administrator can view and take control of the remote desktop session, which is the user connected to. This is a free built-in feature that can compete with solutions such as any desk or Teamviewer. With session shadow admin can view the session, take full control, or view and take full control with the user's consent, these settings can be configured centrally with Group Policy or Registry.
From this post, let's see how we can configure session shadowing and setting group policy and other relevant permissions.
Please refer my previous posts to Implement and configure Windows Virtual Desktop
01 – Working remotely and efficiently with Microsoft technologies
02 - Windows Virtual Desktop | Configuring Prerequisites and WVD Tenant Creation
03 - Windows Virtual Desktop | Create Host Pool and Access through Web, Client App, and Mobile Devices
04 - Windows Virtual Desktop | Configure FSLogix User Profiles using Azure Files and AD Authentication.
05 - Windows Virtual Desktop | Manage App groups and Publish Applications
06 - Windows Virtual Desktop | 2020 ARM Version | Deployment with Domain Services
07 - Windows Virtual Desktop | Extra security with Multi-Factor Authentication
Enabling session shadowing
Before connecting, you need to enable session shadow using group policy or registry edit.
Group Policy
Navigate the policy on Computer configurations – Administrative templates – Windows components – Remote desktop services – Remote desktop session host – Connections
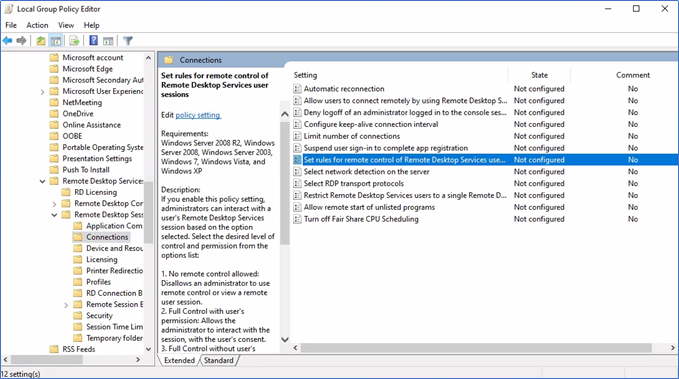
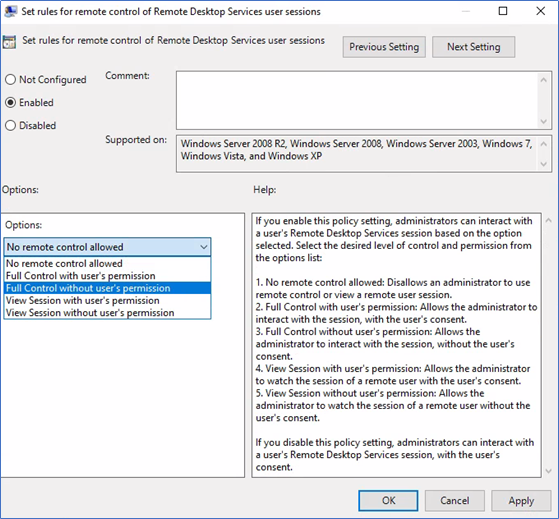
Enable "set rules for remote control…." and select the appropriate option from the list. If you choose an option with users' permission, the user will be prompted to allow the connection.
By Registry Settings
Instead of enabling the policy, you can set the necessary value in the DWORD registry parameter Shadow in the HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services registry key. The allowed values are:
0 – disable remote control;
1 — full control with user's permission;
2 — full control without user's permission;
3 — view session with user's permission;
4 — view session without the user's permission.
Enable Firewall exceptions
If you have enabled the windows firewall on WVD session hosts, make sure to add following firewall exceptions if it's not already added.
Remote Desktop – Shadow (TCP-In)
Remote Desktop – User Mode (TCP-In)
Remote Desktop – User Mode (UDP-In)
Run the following command on CMD to add the firewall rules
Netsh firewall set service type = remote desktop mode = enable
Initiate a shadow session
Shadow session can be initiated by the MSTSC command from a remote computer that has access to the WVD session hosts.
Mstsc.exe /shadow:<Session ID> /v:<Computer name or IP address>
The following options can be used with this command.
- /prompt – request user credentials to connect.
- /control – the mode that allows us to interact with the user session. If the parameter is not set, you will be connected to a user session in a view mode, i. e. you won't be able to control a user's mouse or enter data from the keyboard;
- /noConsentPrompt – allows not to prompt the user for confirmation to connect to a session.
Finding Session ID from WVD ARM version 2020
Login to the WVD console from Azure portal – Users and select the user which you need to connect
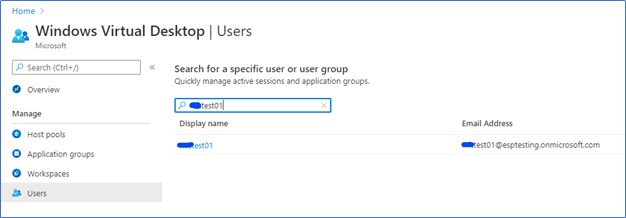
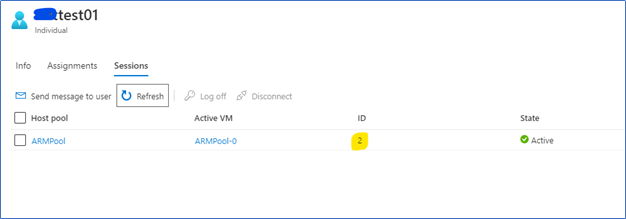
Click the Username, Sessions, and find the Session ID.
Finding Session ID from WVD GA version 2019 (PowerShell)
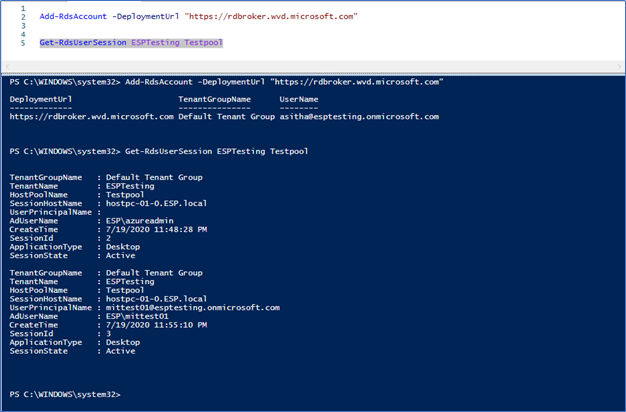
If you are using the 2019 version of WVD, you need to run the following PowerShell command to find the session ID of the user's session.
Connect to the WVD using PowerShell -
Add-RdsAccount -DeploymentUrl "https://rdbroker.wvd.microsoft.com"
Get the Session ID -
Get-RdsUserSession <TenantName> <HostPoolName>
Shadowing the session
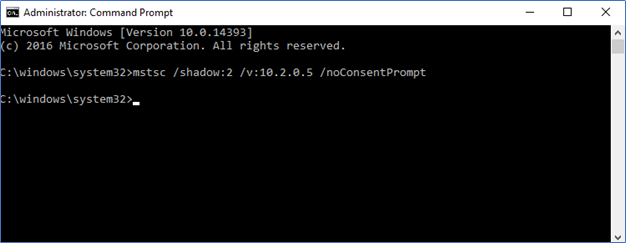
Open a Command Prompt or on RUN type Mstsc.exe /shadow:<Session ID> /v:<Computer name or IP address>
You will get the shadow session.
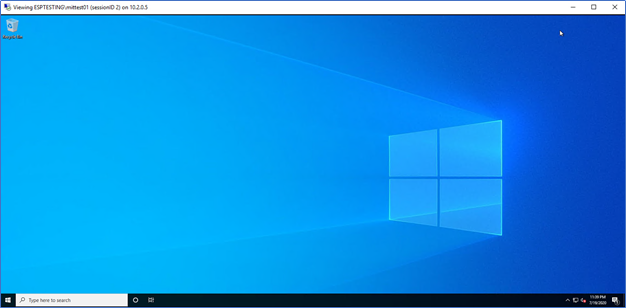
Note – Connecting users through the shadow option should have Administrative access to the WVD Hosts. Also, the connection should be initiate from a Jump host, which should be a separate VM that has RDS connectivity to the WVD Hosts; if not, you will get an Access denied error.
Windows Virtual Desktop shadowing is a great tool to have in an Enterprise Deployment where the organization has much more control over the user's sessions. It is a free built-in feature which is having a much faster response time compared to third-party solutions.
Hope this post is useful
Cheers
Asitha De Silva







