Cloud Management Gateway enables SCCM clients to connect to the site server management point through the public internet. Devices can be online from the public internet. The SCCM site server can deploy and sync software updates, applications, compliance, hardware-software inventory, and other configuration manager features without requiring users to connect to the corporate network.
From my previous article of “SCCM Cloud Management Gateway with Token-based Authentication,” I have discussed the new improvement with SCCM 2002, the Token-based Authentication. It helps users to connect to CMG without a client authentication certificate. With the previous article (here), I have covered what is Token-based authentication, how it is simplifying the CMG implementation and sample costing and sizing estimation, which is relevant when calculating Azure costs. Also, I have covered general prerequisites that require when deploying CMG with Token-based authentication. From this post, I am going to cover everything which is related to implement a new Cloud Management Gateway with token-based authentication.
Implementation Scenario
My solution consists of a Standalone Primary site server with SCCM 2002 version; all clients are upgraded to the latest. Single Cloud Management Gateway instance will be deployed in Azure. Cloud management gateway connection point co-exists with the primary site server along with the Management point and Software update point.
Confirming a Unique DNS name for CMG
As the first step of implementing CMG, you should pick a unique DNS name for your hosted CMG Service. SCCM uses *.cloudapp.net domain for CMG naming. To identify a unique “Cmgname.cloudapp.net” DNS name, you can use the first step of creating a classic cloud service. This will verify the uniqueness of the DNS Name.
If your tenant is not already registered for classic computing, go to the Subscriptions, Select - Subscription – Resource Providers, Type Microsoft.ClassicComputer and click Register.
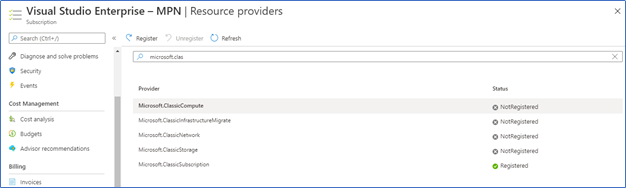
Next type of Cloud service (Classic) in search and Open Cloud Service
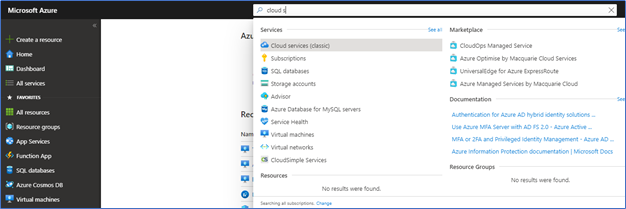
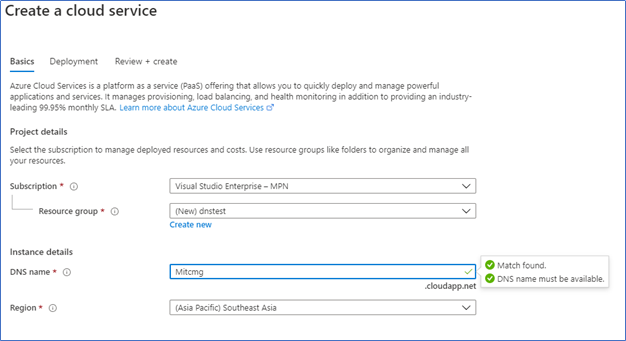
Click Add to get the Create Cloud Service window. From the DNS Name field, try to find your unique DNS name. This DNS name is required when creating the CMG and Server authentication certificate.
Fulfilling Certificate Requirement
With this scenario, we only need a Server authentication certificate. Client authentication with the CMG will be done with a self-sign certificate along with the token authentication. A server authentication certificate required when configuring CMG from the configuration manager site server. It will enable secure communication with the Configuration manager and Azure-hosted CMG through Internet. Also, CMG connecting clients should trust this Certificate to allow communication. Server Authentication certificate can be issued from
- Public provider – Public Certificate
- internal Public Key Infrastructure (PKI)
from this post, I am configuring internal Microsoft Enterprise PKI to issue the Certificate.
Creating Server Authentication Certificate Template
- Login to the Certificate Authority server and right-click Certificate Templates, click Manage.
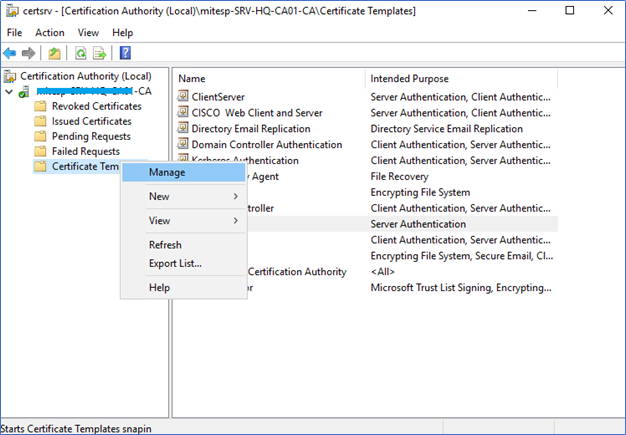
- Right-click on the Web Server template and select Duplicate Template
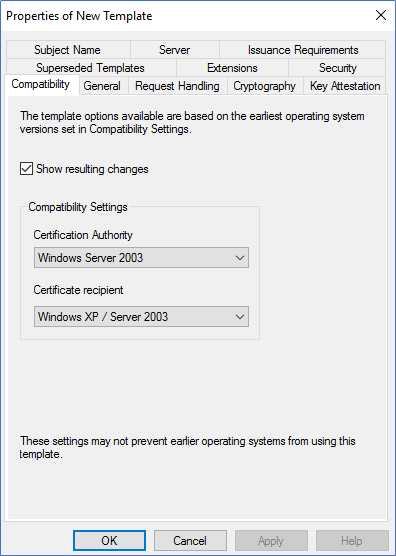
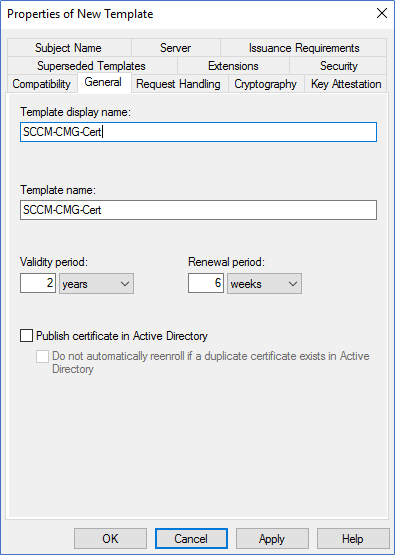
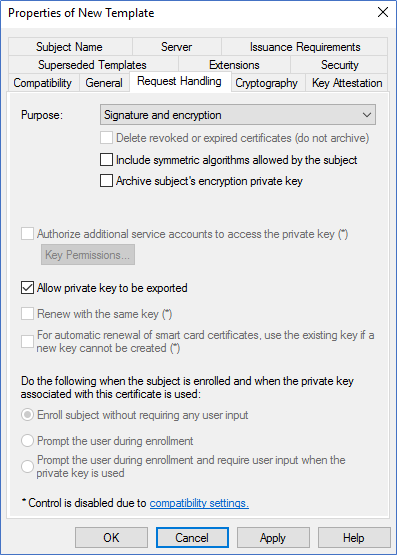
- In the New template, ensure compatibility is selected as windows server 2003. Add a new name to the template. Also, in the Request Handling tab, tick Allow Private Key to be Exported.
- In the Security tab, add the security group containing all the SCCM site server computer accounts. Ensure the group or computer account has Read and Enroll.
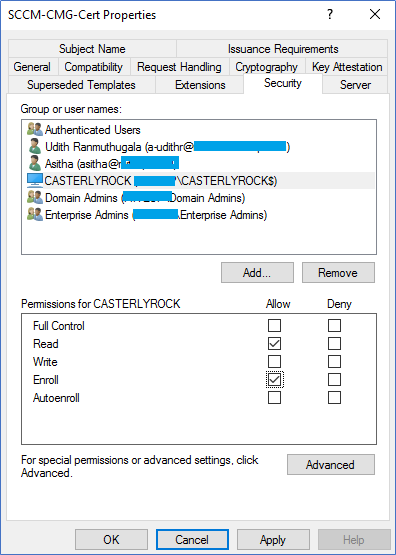
- By default, Domain admin groups and Enterprise admin group have enrolled permissions in the template; make sure to remove the Enroll permissions.
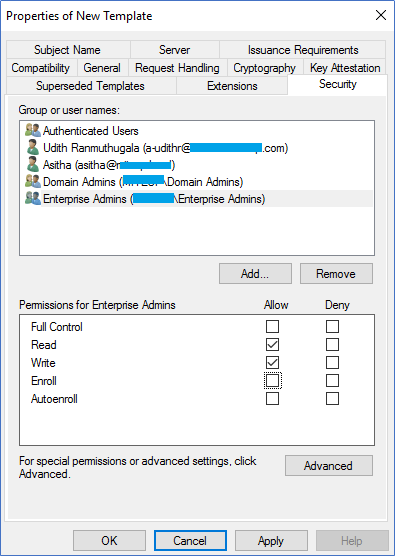
- Click apply to close the new template window.
- Next, you need to enable the Server Authentication certificate template we already created. Right-click on Certificate Templates – New – Certificate Template to issue and select the SCCM Certificate template and click OK.
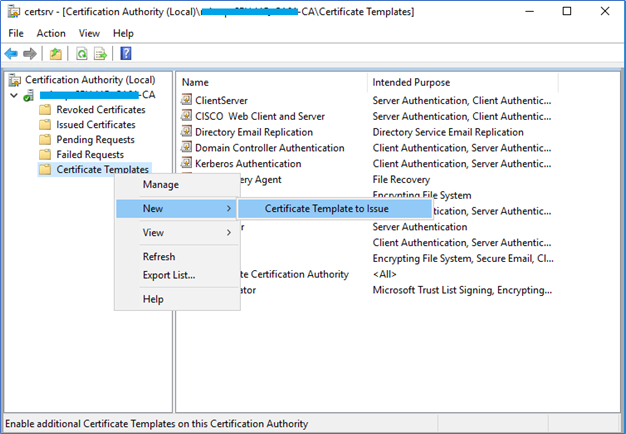

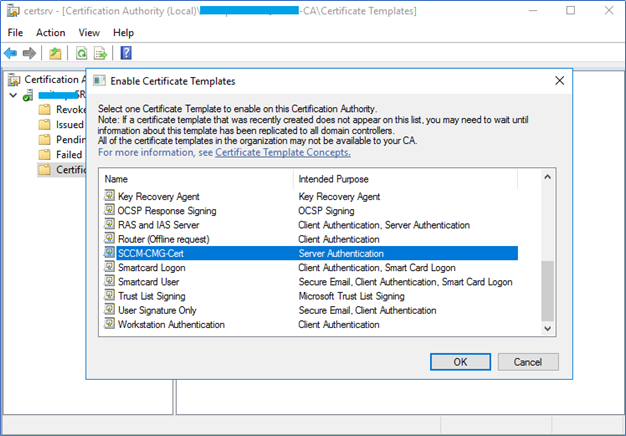
Enrolling Server Authentication Certificate from SCCM
- Login to the SCCM Server and Open local computer certificate manager by MMC – Certificate - Local Computer
- Navigate to Personal – Certificate – All Task – Request New Certificate
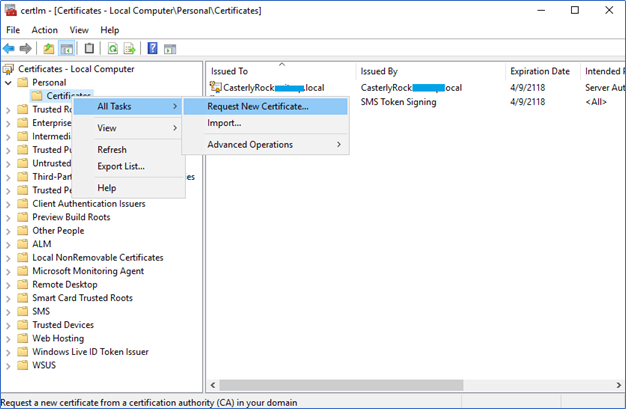
- Click Next, and Next to the Active Directory enrolment policy
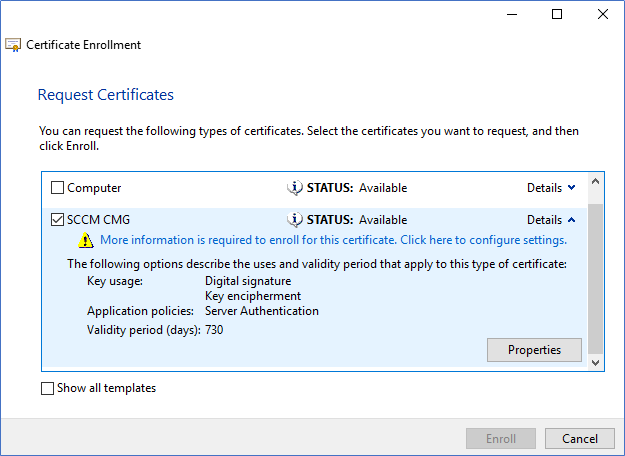
- Select the Certificate Template that you created earlier and click Details and Properties.
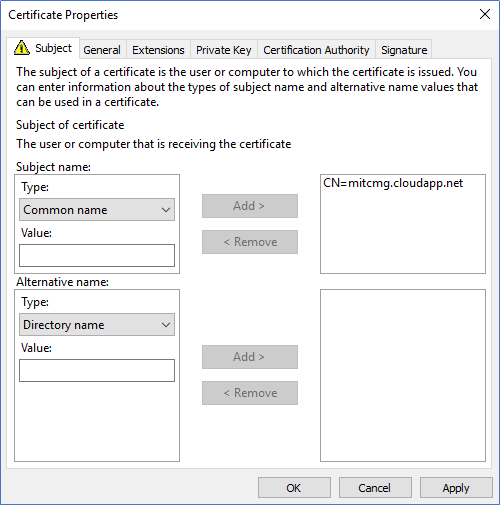
- From Certificate, properties select Common Name and type the Unique DNS name that you found earlier and Add.
- Click Apply and Enroll in the Certificate enroll window.
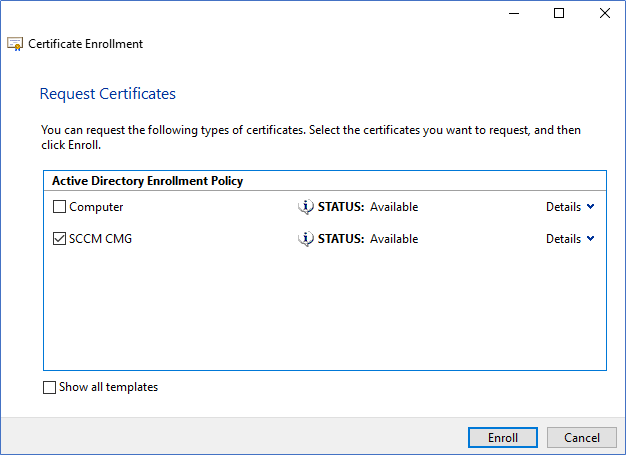
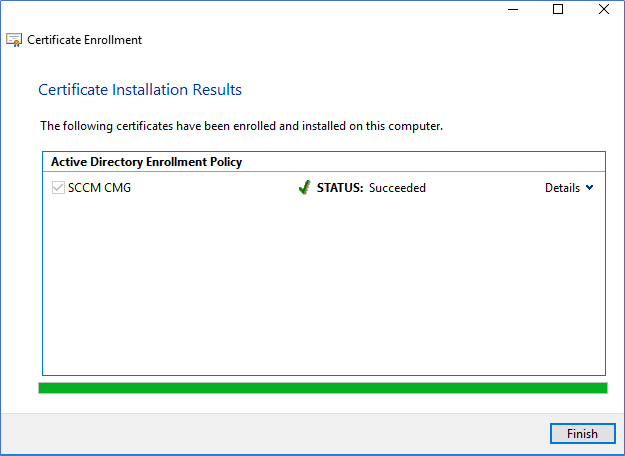
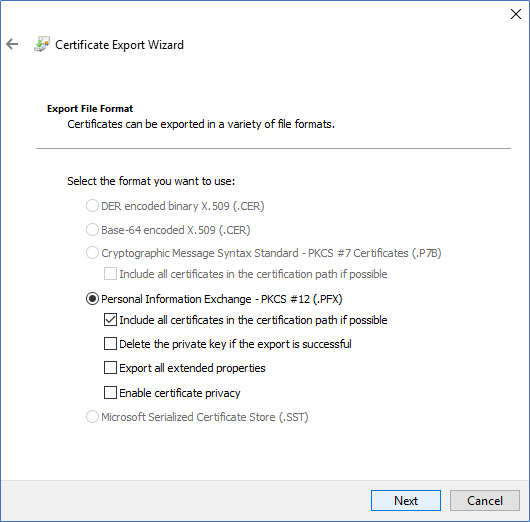
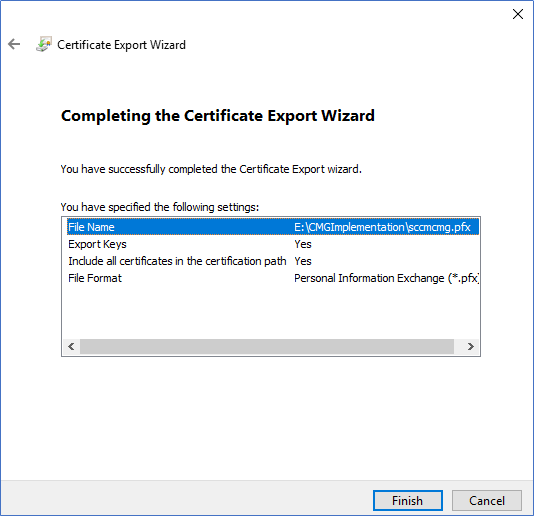
Export the Certificate
This enrolled Certificate needs to be exported with its private key to use when configuring the CMG. Right-click on the Certificate and select Export. When exporting, make sure to select Export with the private key.
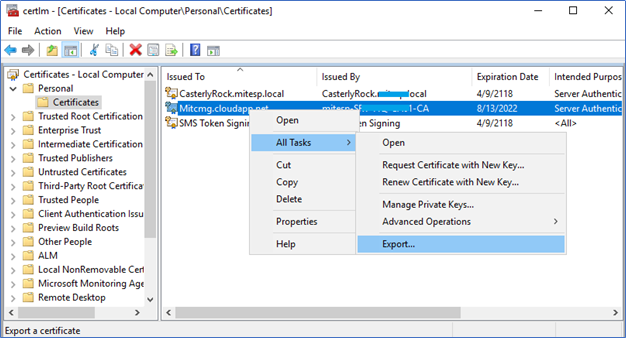
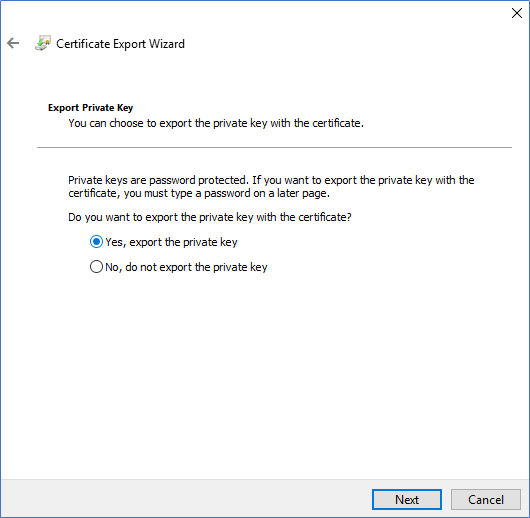
Configuring Azure services to support CMG implementation
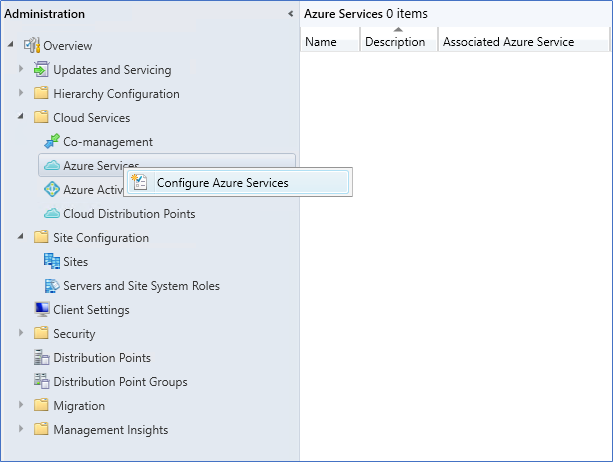
This step will integrate SCCM with Azure services. It will create a Web app and Native client app, which is required for CMG communication. On the wizard, you are required to provide the Azure Global Admin permissions.
- Login to the SCCM server – Management console – Administration – Cloud services, right-click on Azure Services, and select Configure Azure Services.
- Select Cloud Management and Name the service
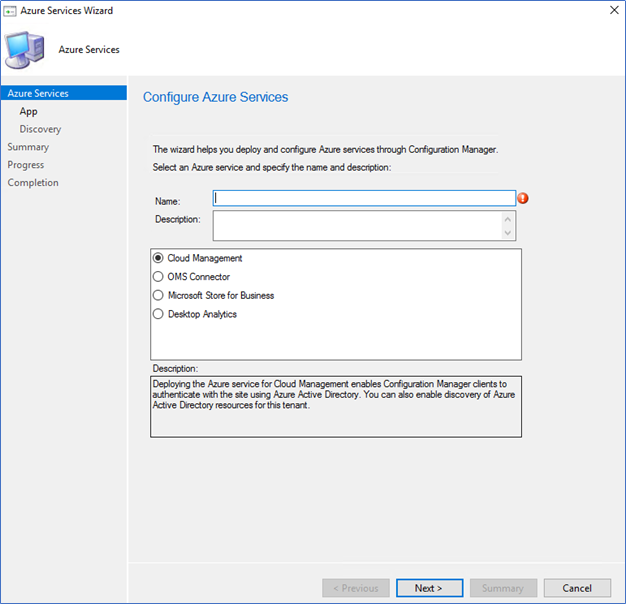
- Select Azure public cloud and click Browse on web app
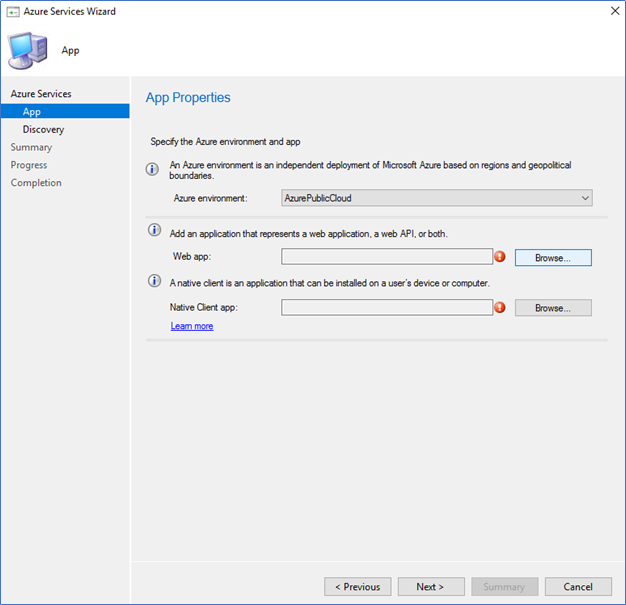
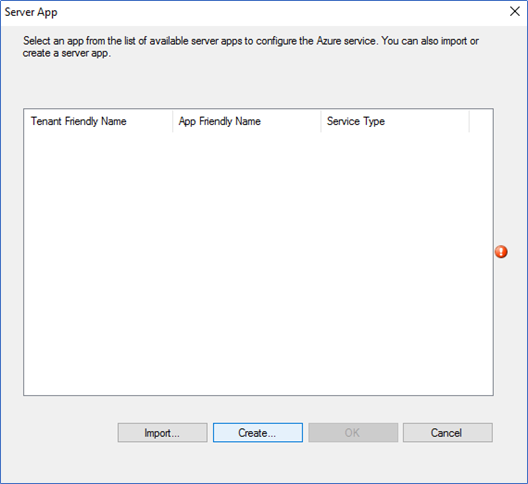
- Click Create on the server app.
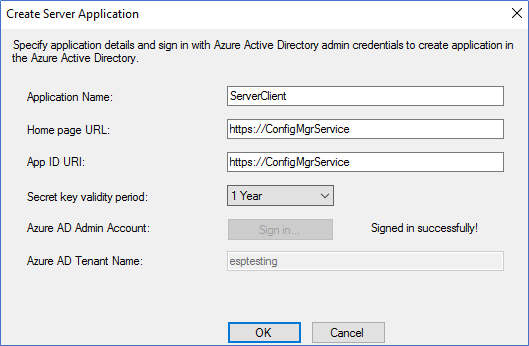
- Provide the Server application name and log in using Azure Global admin permissions.
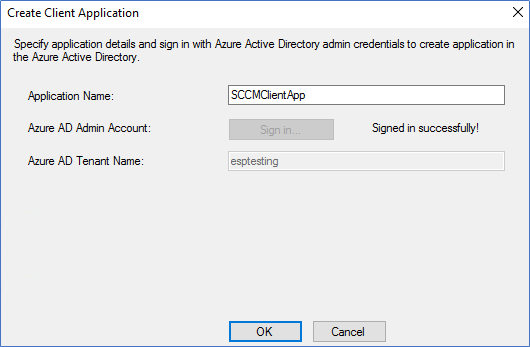
- Login and Create the client app as same as the server app.
- Verify the CMG connection from Azure Services.
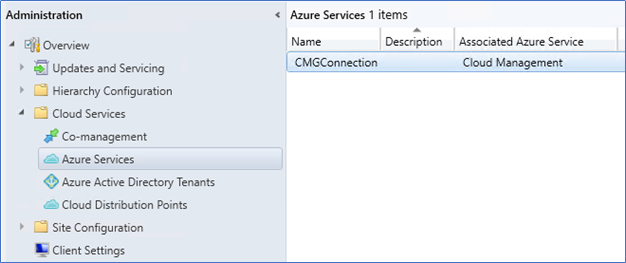
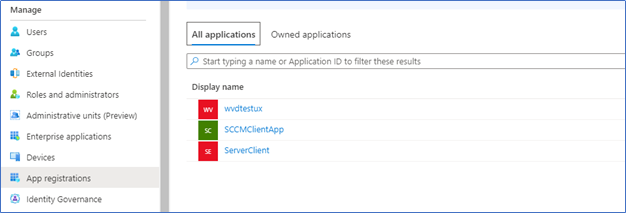
- To verify from Azure end, login to the azure.com and navigate to App registration to see the apps are created.
Deploying Cloud Management Gateway
After configuring all the prerequisites mentioned above, you can start the CMG deployment. Please note we have not configured any client authentication certificate because we are using token-based authentication on CMG. Also, the server authentication certificate should be trusted by each client.
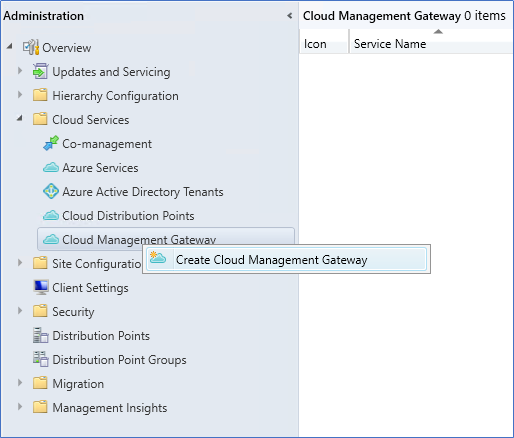
- Login to the SCCM server – Administration – Cloud Services, right-click on Cloud management gateway, and Create Cloud Management Gateway.
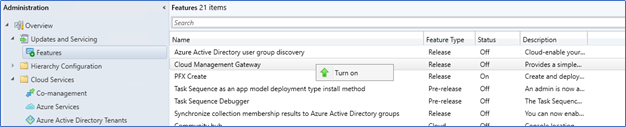
- If you cannot find Cloud Management Gateway from Cloud services, you probably have not yet enabled it from features. If so, Turn on it from Update and Services – Features.
- On Create CMG wizard, select Azure Public Cloud and sign in from the Subscription Admin account.
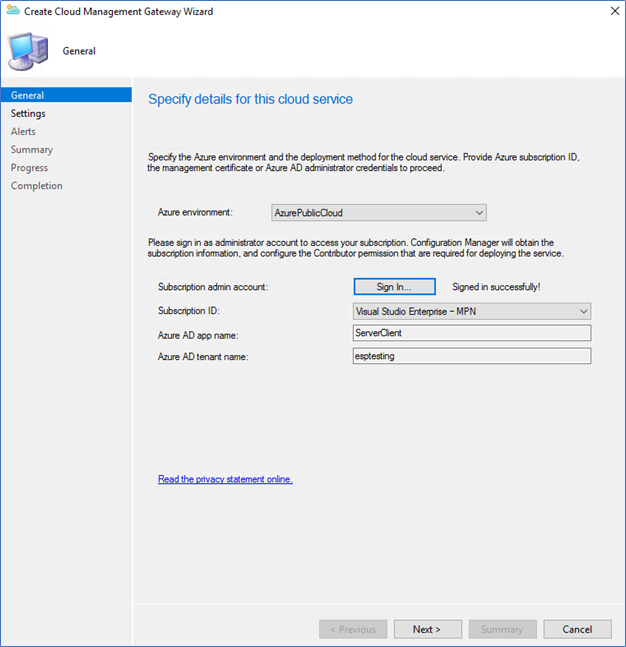
- After sign-in, browse the Server Authentication certificate, which was created earlier. The service name should be populated automatically as your selected unique DNS name. Also, select the Azure region, resource group, and a number of VM instances.
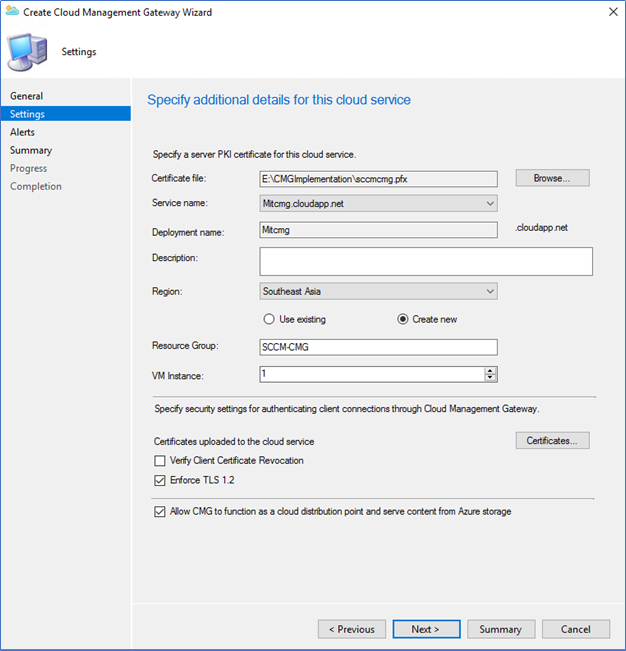
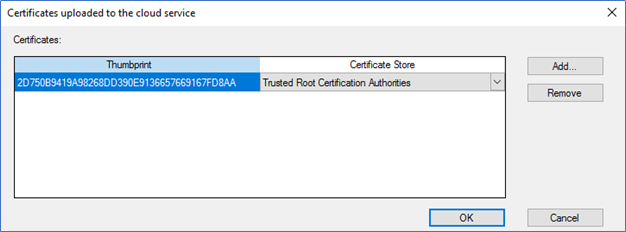
- Since we are using internal CA, you should upload the trusted root certificate by clicking.
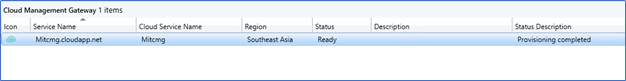
- Click Next till completion, and after 15- 20 minutes, you can see CMG is in Ready Status.
- You can monitor and troubleshoot the deployment.
SCCM Logs - CloudMgr.log, CMGSetup.log
Azure Portal - Azure->monitor–>Activity log
Installing CMG Connection point
The CMG connection point is the site system role for communicating with the CMG. You can install it in a separate site server with or without the MP role. Here I am using the same primary site server to host the connection point role
- In the Administration tab, select the site server – Add site system roles
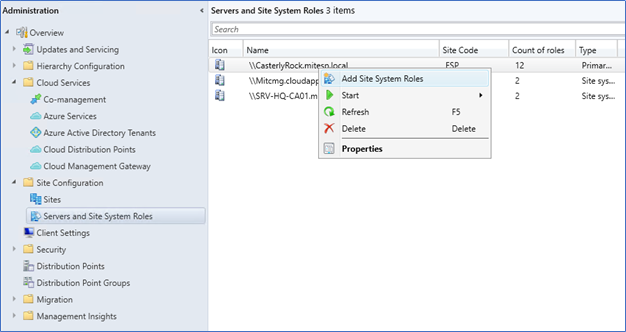
- Click Cloud Management Gateway Connection point and Next.
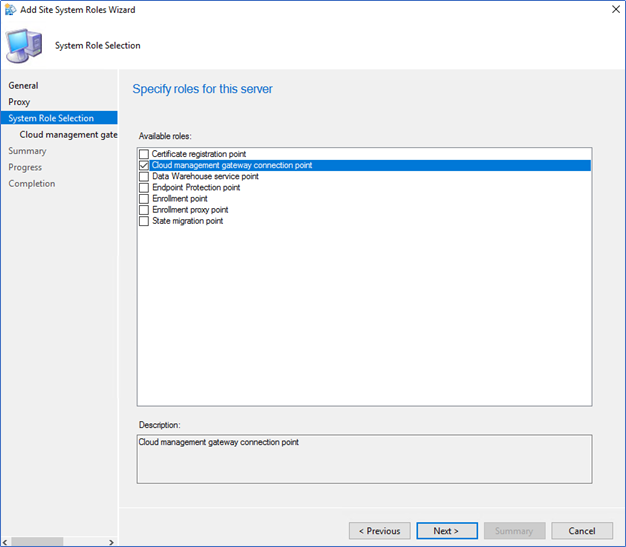
- Review the CMG name and click next to complete with the connection point role installation.
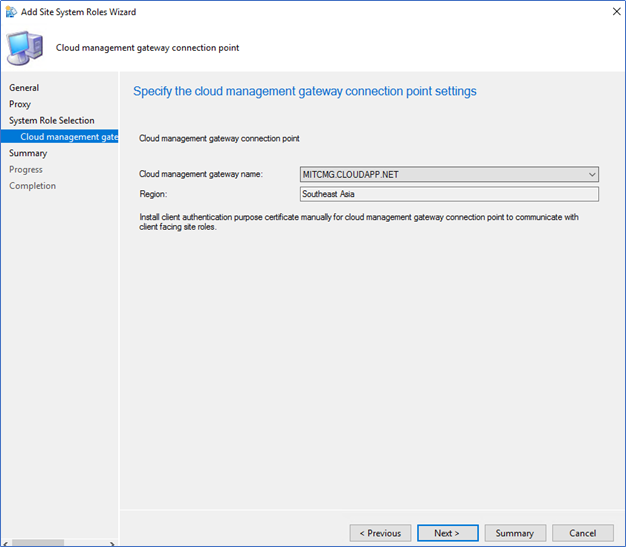
- After successfully configured, you can see the connection point server name and its connection status from Cloud Management Gateway in Administration.
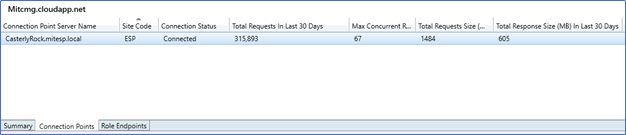
With this step, we have completed the installation of the Cloud Management point, which is to support token-based authentication; from the next post, I will cover configuring Management point, Software update point, boundary groups, and troubleshooting clients which are not communicating with the CMG.
Next - Implementing SCCM Cloud Management Gateway with Token-based Authentication – Part 02 | Configurations and troubleshooting
Hope this post is useful
Cheers
Asitha De Silva








































