
What is Kerberos?
Authentication is one of the primary concerns of network security professionals regarding the security of networks. It allows only to right people to access valuable corporate data. Therefore, a secure authentication method is essential to safeguard organizations' valuable digital assets from outside attackers. It should always be updated with the newest technologies because attackers are often one step ahead of your network security protocols. Username and password-based authentication are still among the widely used methods that make sure only the right people get access to the data and stop the rest. But, transferring user credentials back and forth over the networks is an insecure process. Because malicious attackers could launch sophisticated cyber-attacks to obtain this sensitive information. Deployment of firewalls is considered a strong approach in the prevention of network threats. But, firewalls draw a line between trusted internal networks and untrusted outside networks and assume that threats are always come from the outside.
Surveys show that internal users are responsible for a significant amount of security breaches. For example, IBM’s annual X-Force Threat Intelligence Index shows, up to 60% of cyber-attacks may be due to insider threats. These insider threats can be varied from employees’ accidental mistakes to intentional data thefts. Overall, Cybersecurity Ventures predicts cybercrime damages will cost the world $6 trillion annually by 2021, up from $3 trillion in 2015. Security experts probably warn cybercriminals will use Artificial Intelligence (AI) to power their attacks.
Cybercrimes have existed ever since the invention of computer networks and the internet. MIT developed a network authentication protocol called Kerberos to eliminate authentication-related security problems. Kerberos enables strong authentication procedures between trusted hosts in an untrusted network, usually for the client-server applications. Kerberos uses secret-key cryptography and a trusted third party to verify the user’s identity, and it also acts against the network eavesdropping.
In the 1980s, the Massachusetts Institute of Technology (MIT) first developed the Kerberos to protect network services provided by Project Athena. They make it freely available under copyright permissions, similar to those used for BSD. In 2007, MIT founded the Kerberos Consortium, and they operate Kerberos development and maintenance as an institute funded open source project. Microsoft’s started to use Kerberos as the default authentication method for windows 2000 and later versions. But, Microsoft uses their version of Kerberos, not the MIT software. Kerberos is also built into other major operating systems, including Linux, macOS, Solaris, etc.
The term Kerberos is inspired by the ferocious three-headed dog named Kerberos (Cerberus) in Greek mythology that guards the gates of the underworld. In the authentication protocol, three heads of Kerberos resemble the client, the server, and the Key Distribution Center (KDC). KDC is the main component of the Kerberos architecture, which authenticates the users and services and issues ticket-granting tickets.
Client - an end-user or an application that initiates the service request.
Server - hosts the services or resources the client wants to access.
Key Distribution Center (KDC) – a trusted third-party authentication server. KDC can be grouped into three components; the database, the authentication server (AS), and the ticket-granting server (TGS).
Database – contains all information related to the users and services.
Authentication Server (AS) responds to the client's initial authentication request and grants a ticket-granting ticket (TGT) after a successful authentication process.
Ticket-Granting Server (TGS) – grants service tickets to the clients with valid TGT to access the requested services or resources.
How does Kerberos authentication work?
As mentioned above, the Kerberos environment consists of the client, the server, and the trusted third-party authentication server, known as KDC. Kerberos uses symmetric encryption, which means only one key is used to encrypt the plaintext message and then decrypt that message. Kerberos uses symmetric keys of all components, including client, file server, and Ticket-Granting Server (TGS) for encryption.
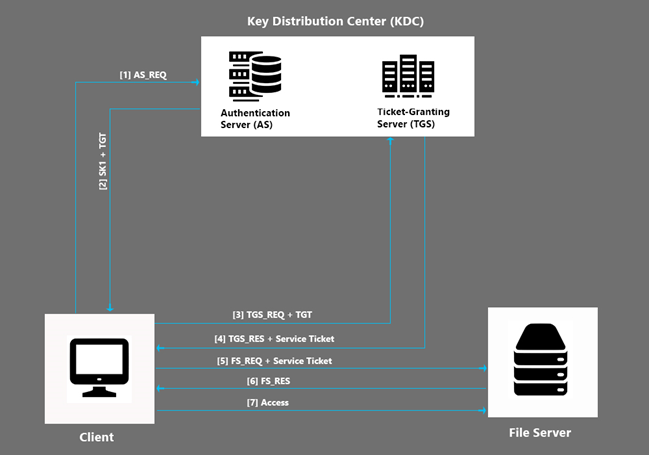
- To begin the process, the client creates a package (AS_REQ) contains information such as user ID, File Server name, client’s IP address, etc. The client then encrypts this package using the symmetric key that generates by hashing the user’s password and sends it to the Authentication Server.
- Once the package is received, the Authentication Server (AS) checks for the user ID in its database and retrieves the symmetric key to decrypts the client’s package. Then, AS creates two packages. The first package consists of a random session key (SK1), and AS encrypts this package with the client’s symmetric key. The second package consists of the Ticket-Granting Ticket (TGT), which includes a copy of the session key (SK1), user ID, client’s IP address, expiration time, ... as encrypts this package using the symmetric key of the Ticket-Granting Server (TGS). Then, both packages send to the client.
- The client decrypts the first package using its symmetric key and retrieves the session key (SK1). Then, it creates a new package, including user ID, and encrypts that with the session key (SK1). The client also creates an unencrypted plaintext message contains the request to access the File Server. Finally, it sends these two packages (TGS_REQ) and TGT to the TGS.
- TGS decrypts the TGT with the TGS key and retrieves the session key (SK1). TGS then decrypts the client package, which contains the user ID using this session key (SK1) and verifies it with TGT entries. After the verification, TGS creates two new packages. The first package includes a new second session key (SK2), user ID, client’s IP address, expiration time, etc. and encrypts it using the symmetric key of File Server. This is called Service Ticket. The second package (TGS_RES) contains a copy of a second session key (SK2), File Server name, expiration time, etc. and encrypts it with the first session key (SK1). Then, sends these two packages to the client.
- The client decrypts the second package using the first session key (SK1) and retrieves the second session key (SK2). Then, it creates a new package with a user ID and encrypts it with the second session key (SK2). This new package (FS_REQ) and Service Ticket sends it to the File Server.
- File Server decrypts the Service Ticket using its File Server key and retrieves the second session key (SK2). Then, it decrypts the client package using this key (SK2) and compares it with Service Ticket for verification. After the verification, File Server creates another package (FS_RES) containing its name and encrypts with the second session key (SK2). Then, it sends back to the client as a server confirmation message.
- Finally, the Client decrypts it using the second session key (SK2) and begins to access the services or resources in File Server.
During the authentication process, symmetric keys should always be matched; otherwise, it stops the decryption and fails the process. Kerberos is a Single Sign-On (SSO) enabled authentication protocol that users do not require to provide their login credentials repeatedly once they are signed in. Kerberos uses TGT to store the user information and prove the user identity when necessary.


