
Microsoft Information Protection is a Unified solution integrating Information protection solutions such as Office 365 Information Protection, Windows Information Protection, and Azure Information Protection. Refer (here). From this post, I am targeting a BYOD strategy where the company does not have any ownership or authority over the end-user device. Still, corporate data can be protected on this personal device.
Windows information protection deployed through Intune App protection policy on without enrolled device to Intune will achieve this scenario. Before jump into the step-by-step configurations, let's understand the overall concept.
01 - Understanding Microsoft Information Protection
02 - Windows Information Protection | Intune App Protection Without Enrolment | Step by Step (This post)
03 - Windows Information Protection | Intune App Protection Without Enrolment | User Experience
Microsoft Information Protection
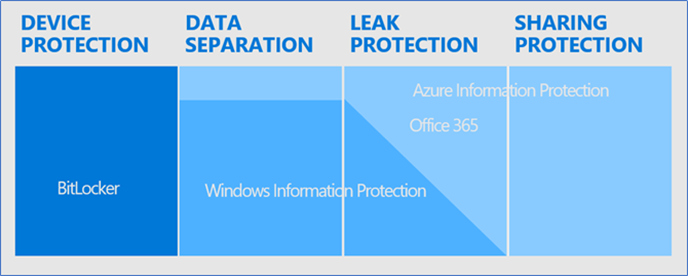
Microsoft Information Protection is a Unified solution to address Device Protection, Data Separation, Leak Protection, Sharing Protection. It uses Information protection solutions such as BitLocker, Office 365 Information Protection, Windows Information Protection, and Azure Information Protection.
Windows Information Protection
WIP helps to protect against potential information leakage without otherwise interfering with the user experience. WIP also helps to protect enterprise apps and information against accidental information leakage on enterprise-owned, corporate-owned, and employee-owned devices (BYOD) without requiring changes to your environment or other apps
Intune App Protection
App protection policies (APP) are rules that ensure an organization's data remains safe or contained in a managed app. A policy can be enforced to monitor or prohibit move corporate data from these applications. It is ensured data is safe within these manage apps. A managed app is an app that has app protection policies applied to it and can be managed by Intune.
There are two types of app protection policies that can be applied to Windows 10
- WIP without enrolment in MDM (Intune)
This is mainly to address the BYOD scenario where corporate data need to be separated from personal and protect from unauthorized use. The device will be Azure AD registered; however corporate does not have access or management capabilities. However, the company has control over the corporate tagged data through WIP policies.
- WIP with enrolled in MDM (Intune)
These devices need to be enrolled in a mobile device management solution such as Microsoft Intune. Intune will provide centralized management for the devices, and corporate can manage the device and even wipe the data. This is mostly used for corporate own devices.
Enlighten and unenlightened applications
- Enlighten apps
These are MAM-aware applications, which means these apps can differentiate corporate vs. personal data on the application. With enlighten apps, your WIP policy will only target the corporate data, and you can enforce restrictions such as cut, copy, paste. Also, the device's corporate data will be placed encrypted while personal data will be intact without restrictions.
Ex – Office applications, Edge, notepad
- Unenlightened apps
These are MAM unaware applications, which means these apps cannot identify corporate and personal data separately. thus, when these apps are managed, they consider all data to be company data and encrypt everything by default
Prerequisites
- Configuring MAM provider
I am addressing this the below topic.
- Azure AD Premium licenses
Since we are configuring without enrolment, an AD premium license is enough. If you are enrolling, you need the Intune license, which is the EMS license suite. - Windows 10 Creators update
Configuring MAM Provider
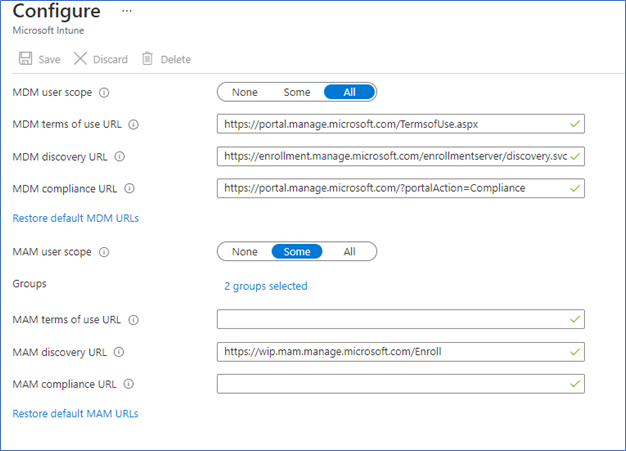
Before configuring the WIP-WE policy, you need to define the user scope of the MAM provider. This setting only affects Windows 10 devices, not Android or iOS devices.
Log in to the Azure Portal – Azure Active directory - Mobility (MDM and MAM) – Microsoft Intune - MAM user scope.
Select a group for the BYOD users or select All users. If the URL is different than what is on the screenshot, click Restore default MAM URLs to get the original.
This will register the device to the Azure Active Directory when the user signs in to the WIP policy specified protected application.
Creating WIP App Protection Policy
- Login to the Intune portal - https://endpoint.microsoft.com/
- Navigate to Apps – App Protection Policies click Create Policy – Windows 10
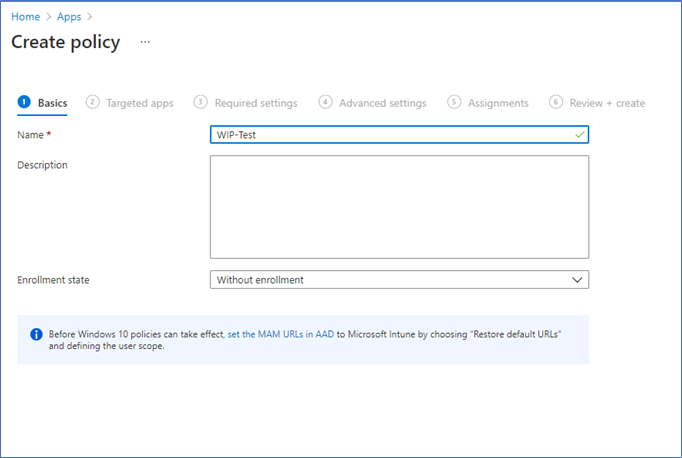
- Name the policy, and select Without Enrollment.
- Next, you need to select the protected applications; here, I’m only working with Microsoft enlighten applications, so you can click + Add - Recommended applications and select all.
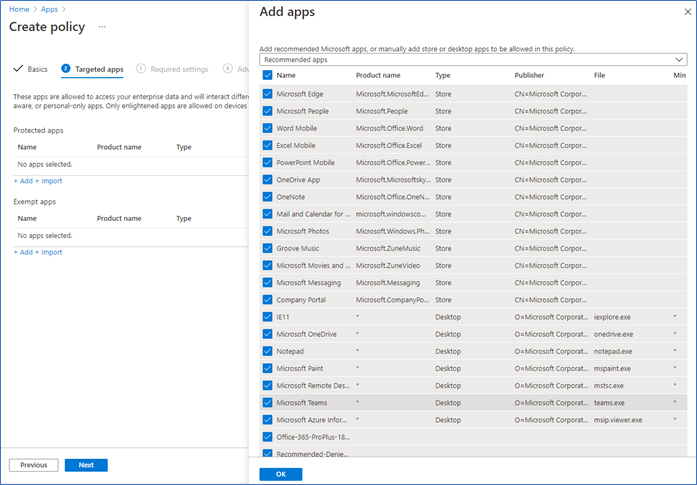
Note – you can add unenlightened apps as well. When adding a custom app, make sure to select the correct EXE name and the publisher. Also, as I explained before, unenlightened apps do not become aware of the separation of corporate and personal data, so it treats all the data as corporate and applies policies.
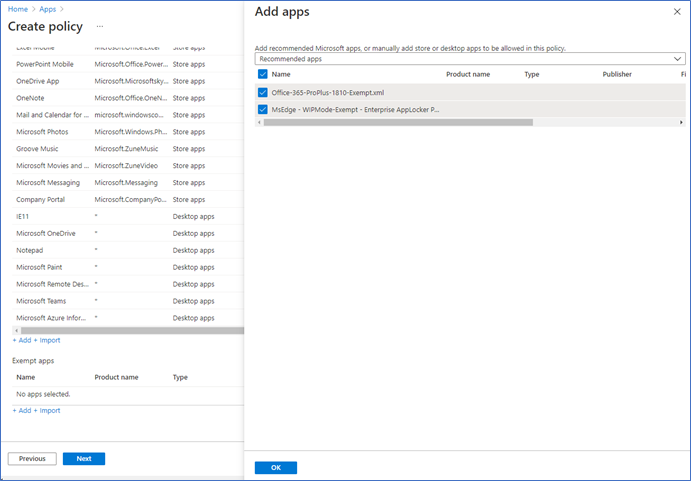
- Next, you need to Exempt some office applications, failure to do this can occur with some sign-in issues in Office 365 apps. Click +Add – Recommended apps, select all.
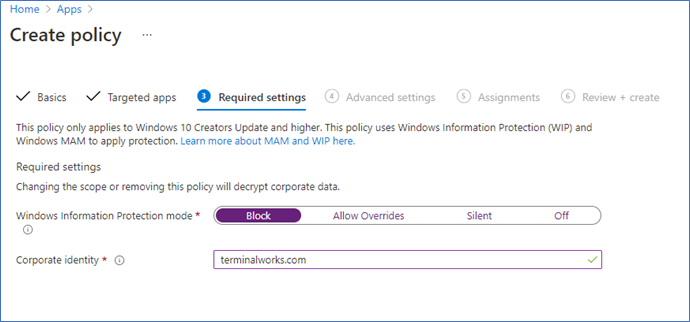
- Next, you will get the most important setting of the policy, Windows information protection mode, and corporate identity. Let's discuss it a bit before setting.
Windows Information protection mode – you can select a protection mode from below list
Block – this will block corporate data being shared with other than protected apps.
Allow overrides – Users will get notified when they tried to move the protected app's data to none protected. It will not block the action, notification, and log.
Silent – User will not get a notification when moving protected data to unprotected apps. Action will be logged.
Off – will not enforce the policy.
Corporate identity -
This is how corporate or enterprise data being identified. This field should only contain the primary domain of the company. All other corporate domains should be added to the Protected domains in the network perimeter.
Here I am selecting Block and my primary domain.
- Next, you need to define the network perimeter where protected apps can access enterprise data on your network.
Note - There are no default locations included with WIP. You must add each of your network locations. This area applies to any network endpoint device that gets an IP address in your enterprise’s range and is also bound to one of your enterprise domains, including SMB shares. Local file system locations should just maintain encryption (for example, on local NTFS, FAT, ExFAT).
here I’m only considering Office 365 and Microsoft application access, below network boundaries, should be added. If you have additional domains, add them to Protected Domains.
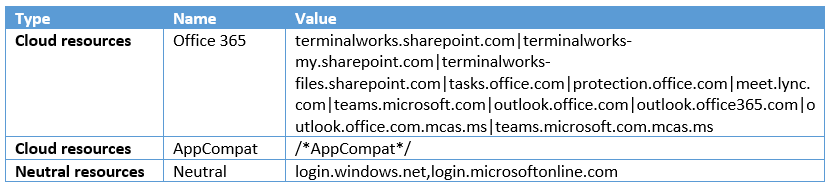
Office 365 -terminalworks.sharepoint.com|terminalworks-my.sharepoint.com|
terminalworks-files.sharepoint.com|tasks.office.com|protection.office.com|
meet.lync.com|teams.microsoft.com|outlook.office.com|outlook.office365.com|
outlook.office.com.mcas.ms|teams.microsoft.com.mcas.ms
AppCompat- /*AppCompat*/
Neutral - login.windows.net,login.microsoftonline.com
- Next, I would like to let the user know when they are acting in a corporate context. The below setting will enable overlaying the icon.
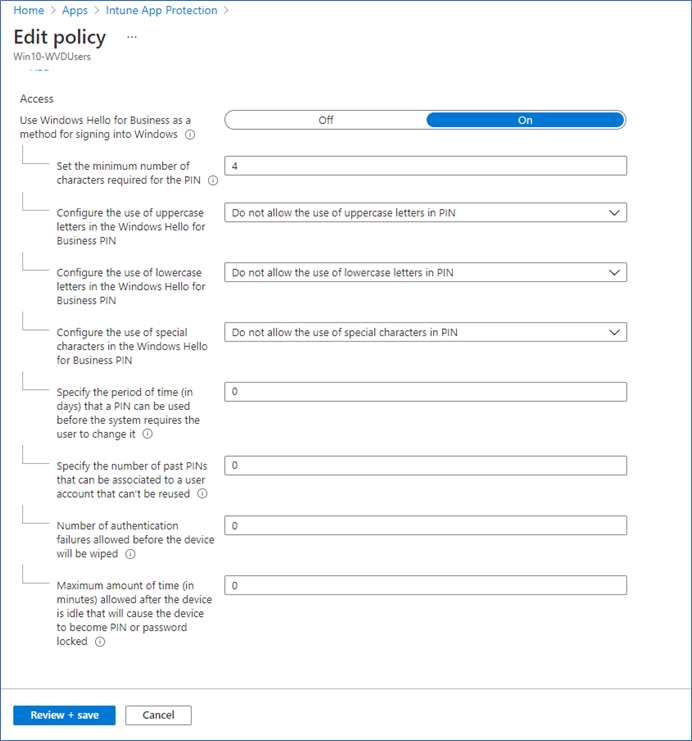
- If you are working with BYOD devices, you can consider enforcing Windows Hello authentication settings.
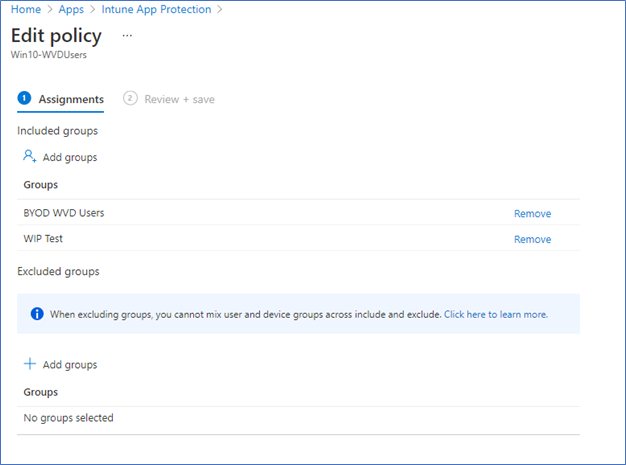
- Select the Groups you want to assign the policy, add only security groups.
- Review and Save the policy.
Monitoring status
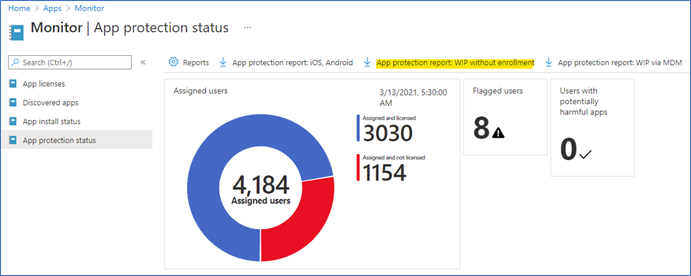
After you have assigned the policy, it will be received by the users in few minutes. There is an Azure report you can download to see the status.
Endpoint management portal – Apps – Monitor – App Protection status click App Protection report: WIP without enrolment. You can get the username, device name, policy, and last sync time.
This is how you configure a WIP policy on BYOD devices to restrict access to corporate data. From the next post, let's discuss the user experience and what to expect from this policy. This would be very important to implement BYOD hygiene and how users can work efficiently.
Next - Windows Information Protection | Intune App Protection Without Enrolment | User Experience
I hope this post is useful.
Cheers
Asitha De Silva













