Azure Sentinel is a Cloud-native, Born in cloud SIEM and a SOAR solution. It built on top of Azure while utilizing existing solutions such as Log Analytics, Security center, Logic apps, and Kusto query language to deliver intelligent security analytics and threat intelligence throughout your organizations. Additionally, it is a single product that can integrate Microsoft and none Microsoft solutions to detect alerts, Threat visibility, proactive hunting, and threat response.
Azure Sentinel Architecture
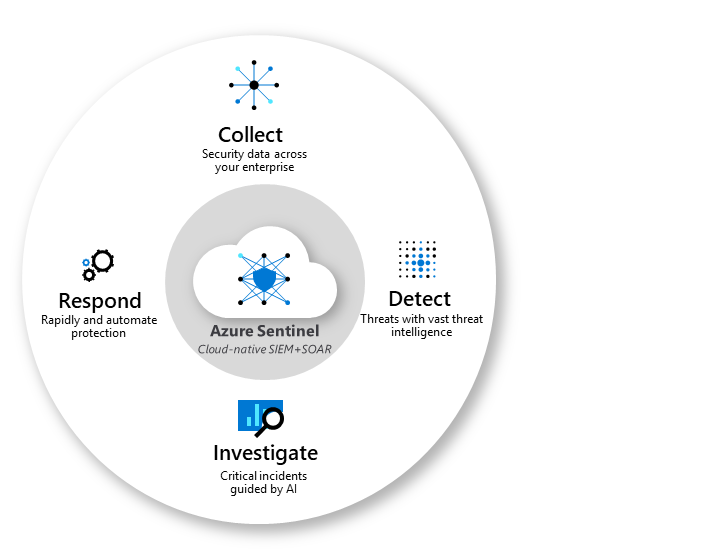
Azure sentinel can further identify by understanding its core capabilities.
Collect – collect data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
Detect can detect previously undetected threats and minimize false positives using Microsoft's analytics and unparalleled threat intelligence.
Investigate - Investigate threats with artificial intelligence, and hunt for suspicious activities at scale, tapping into years of cybersecurity work at Microsoft.
Respond – it can respond to incidents rapidly with built-in orchestration and automation of everyday tasks.
Connect with Data Sources
Azure sentinel supports many data sources. Connections to these data sources inject data into sentinel for above collect, detect, investigate and respond process cycles. In addition, it provides native, out-of-the-box connections to Microsoft solutions such as Azure AD, Microsoft 365 defender, Microsoft 365 solutions, Azure ATP, Cloud app security, and more.
Microsoft and Sentinel also support third-party integrations with common event format, Syslog, or REST-API to connect to the data sources. The below table represents the supported connections as of today.
Service to service integration
These services can be connected natively with few clicks. In addition, it supports Azure's foundation for out-of-the-box integration.
- Amazon Web Services - CloudTrail
- Azure Active Directory - audit logs and sign-in logs
- Azure Activity
- Azure AD Identity Protection
- Azure DDoS Protection
- Azure Defender for IoT (formerly Azure Security Center for IoT)
- Azure Information Protection
- Azure Firewall
- Azure Security Center - alerts from Azure Defender solutions
- Azure Web Application Firewall (WAF) (formerly Microsoft WAF)
- Cloud App Security
- Domain name server
- Microsoft 365 Defender - includes M365D incidents and Defender for Endpoint raw data.
- Microsoft Defender for Endpoint (formerly Microsoft Defender Advanced Threat Protection)
- Microsoft Defender for Identity (formerly Azure Advanced Threat Protection)
- Microsoft Defender for Office 365 (formerly Office 365 Advanced Threat Protection)
- Office 365 (now with Teams!)
- Windows firewall
- Windows security events
External solutions via API
These data sources can be connected using APIs provided by the data source. Most of the latest security tools provide a set of APIs to retrieve its logs and information. Currently, supported solutions are
- Agari Phishing Defense and Brand Protection
- Alcide kAudit
- Barracuda WAF
- Barracuda CloudGen Firewall
- BETTER Mobile Threat Defense
- Beyond Security beSECURE
- Cisco Umbrella
- Citrix Analytics (Security)
- F5 BIG-IP
- Forcepoint DLP
- Google Workspace (formerly G Suite)
- NXLog (Windows) DNS Logs
- NXLog LinuxAudit
- Okta SSO
- Orca Security
- Perimeter 81 logs
- Proofpoint On Demand (POD) Email Security
- Proofpoint TAP
- Qualys VM
- Salesforce Service Cloud
- Sophos Cloud Optix
- Squadra Technologies secRMM
- Symantec ICDX
- VMware Carbon Black Cloud Endpoint Standard
- Zimperium
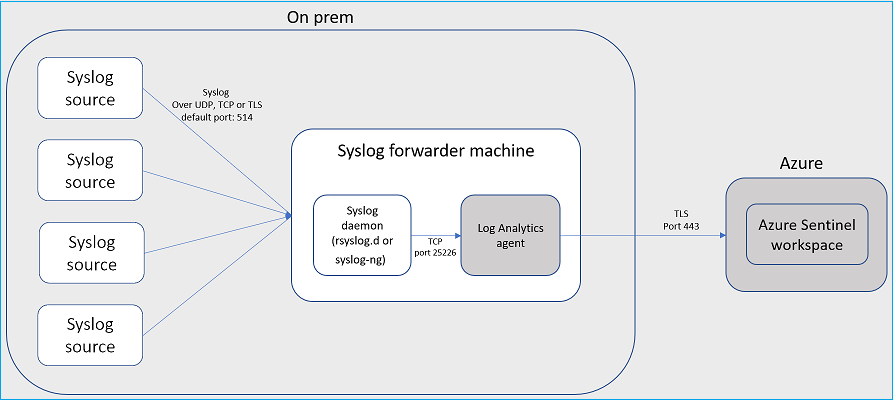
Collect data from Azure sentinel Agent
Azure Sentinel agent, also known as a Log analytics agent, can collect data from VM’s On-premises machines and external appliances. It can be deployed automatically or manually. For example, if you have multiple Syslog sources in your environment, you can create a Syslog forwarder machine and deploy a Log Analytics agent. This Log analytics / Sentinel agent will initiate a 443 connection to the Azure sentinel workspace and distribute gathered data from other Syslog sources.
Monitor and Visualize data
When you connect data sources to Sentinel, those data are placed in a log analytics workspace. The azure monitor is the native tool to visualize log analytics data. So, with Azure Sentinel, you can leverage Azure Monitors Dashboards and Workbooks to view the investigable information. Azure Sentinel allows you to create custom workbooks across your data and comes with built-in workbook templates to quickly gain insights across your data as soon as you connect a data source.
Use of Kusto KQL
Kusto is the query language that is used in the Log Analytics workspace and Azure monitor. You can use it to perform analysis on data to create Analytics, Workbooks, and perform Hunting in Azure Sentinel.
Azure Sentinel User and Entity Behavior analytics
UEBA features use analytics to build users and entities' standard profiles and entities such as hosts, applications network traffic, and data repositories. It gathers data over time to build a baseline to identify the normal behavior of each user or entity. Activity that is anomalous to these standard baselines is represented as suspicious and relevant action from the sentinel. It will support identify the following threat scenarios.
- Abuse of privileged identities
- Compromised user and entity
- Insider threats
- Data exfiltration
Architecture of UEBA
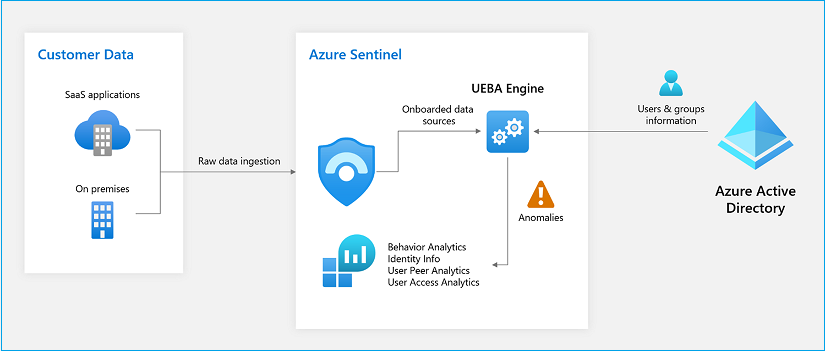
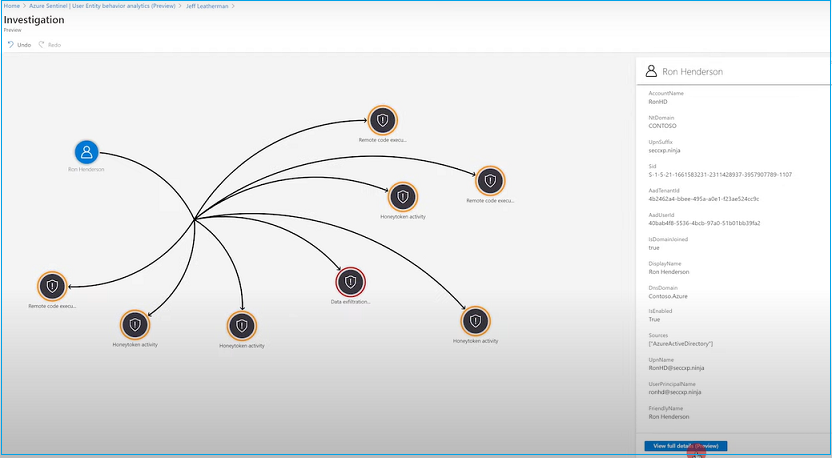
UEBA engine takes raw data of users and entities and transforms them into contextual information. For example, a user's UPN, SID, Email relate to a single user object. Then it identifies the behavior of each of these objects, such as where it is connecting. What is the network boundary, geolocation, device insights, etc.? From this analytics, the UEBA engine will able to define a baseline of behavior for each entity. After the discovering and identifying cycle completes, it can identify anomalous resource access such as unusual geolocation, unusual HVA access, and access from new devices.
UEBA will
- Detect anomalies based on entity behavior profiling
- Investigation and hunting with contextual and behavioral information
- Entity pages provide clear insight, timeline, and investigation prioritization
- Instant security value following quick and simple onboarding
Activity detention from Timeline
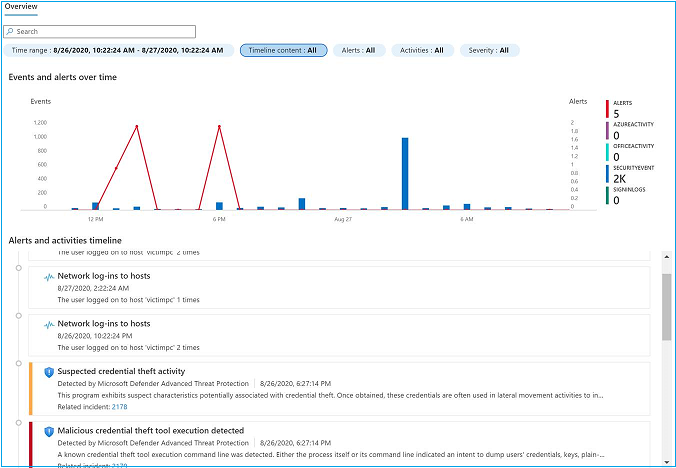
User / Entity investigation
Azure Sentinel Security Orchestration, Automation, and Response (SOAR)
Azure sentinel has the capability to act as SOAR. It can automate any recurring and predictable activities and respond and remediate tasks carried out by the Security Operations Center (SOC). This will reduce unnecessary workloads from your engineers and give more time to act to the real threats of the organization. Azure sentinel uses automation rules, and playbooks initiate actions.
Automation rules
Automation rules allow users to manage the automation of incident handling centrally. It will allow automating responses for multiple analytics rules at once. Also, it will enable you to simplify complex workflows for your incident orchestration processes.
Playbooks
The playbook is based on workflow built-in using Azure Logic Apps, a cloud service that helps to schedule, automate and orchestrate tasks and workflows across systems throughout the organization. A playbook can help automate and orchestrate your threat response; it can integrate with other internal and external systems.
Pricing Options
Azure sentinel has two main pricing options and also the free tier.
Commitment / Capacity Reservations Pricing
This is a fixed fee based on the commitment tier the customer select. You need to predict the cost and select from the available plans. It’s much cheaper when compared to the Pay as you go model. Discounts starting from 50% and go into 65% monthly. Customers can also opt-out of the contract after 31 days from the start of the contract. Below pricing for East US
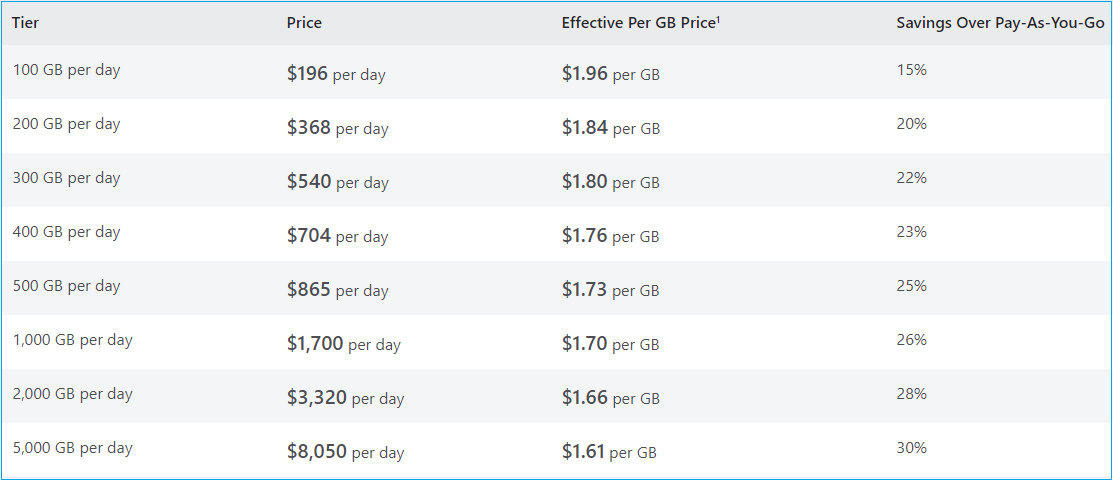
Pay as you go, model.
This option will bill each GB that is ingested into the Azure Sentinel for analysis. For East US, it is 2$ per GB.
Note – Both these pricing models do not include the related data ingestion charges for Log Analytics. It will be separately billed through Azure Monitor Log Analytics charges. (here)
Free Tier
Free trial is available for Azure sentinel. First, 31st dates will not be charged, and after 31 days above pricing models can be selected.
Data Retention
After enabling Azure sentinel, data ingested into Azure Log Analytics workspace will have 90 days free of charge retention. After these 90 days, normal Azure monitor log analytics retention charges will apply.
I hope this post is useful.
Cheers
Asitha De Silva
References
Microsoft Ignite content
Microsoft TechNet, Docs







