Microsoft Active Directory has been here for as long as we know and there is no doubt that it’s the best identity service provider. Since it’s the critical part of the whole IT environment, there are numerous targeted attacks to compromise the Identity system.
When considering the Domain Controller security, restricting communication ports to a minimum is a good way of increasing security. However, there is no such thing as a minimum, as if you restrict the ports recommended by Microsoft, some services will not work as expected. So, to optimize things, you can restrict the ports of the services you don’t use in your environment such as DHCP, AD Web services, etc. In this post, I’m going to cover what Microsoft recommends on DC to DC, DC to client and DC to DMZ communication. This post is based on articles mentioned in the references.
Domain controller to Domain controller
The following table represents the communication ports between two DCs. This applies to all Windows Server Domain Controllers from Windows Server 2000 to Windows Server 2016. However, there are differences between the dynamic ports before Windows Server 2003 and anything beyond the 2008 server versions. This port range is used to communicate the RPC traffic.
In a domain that consists of Windows Server® 2003–based domain controllers, the default dynamic port range is 1025 through 5000. From Windows server 2008 onward, the new default RPC port range is between 49152 and 65535. Also, you can restrict this communication to a specific port. That will be discussed that in this article.
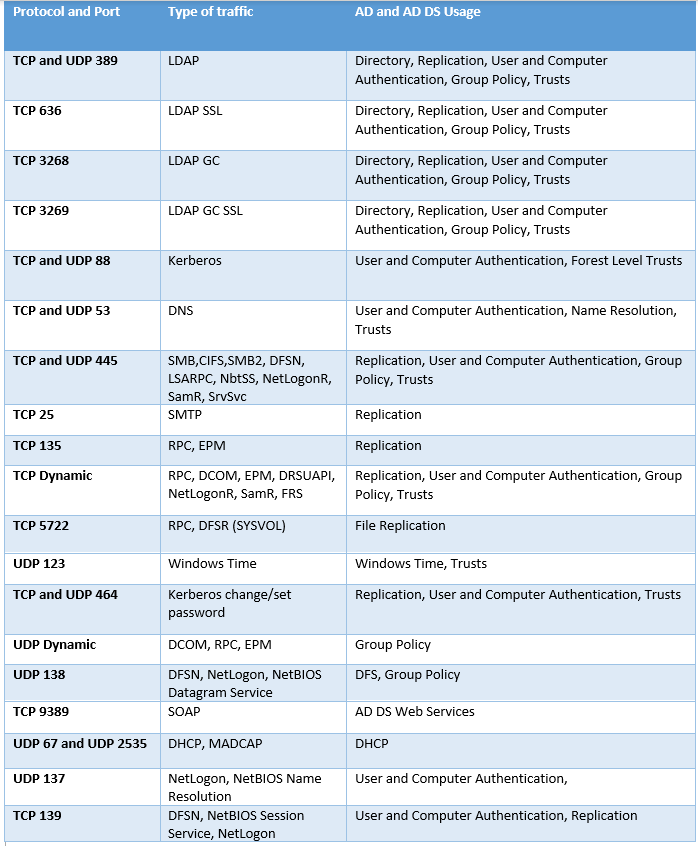
Domain Controller to Client
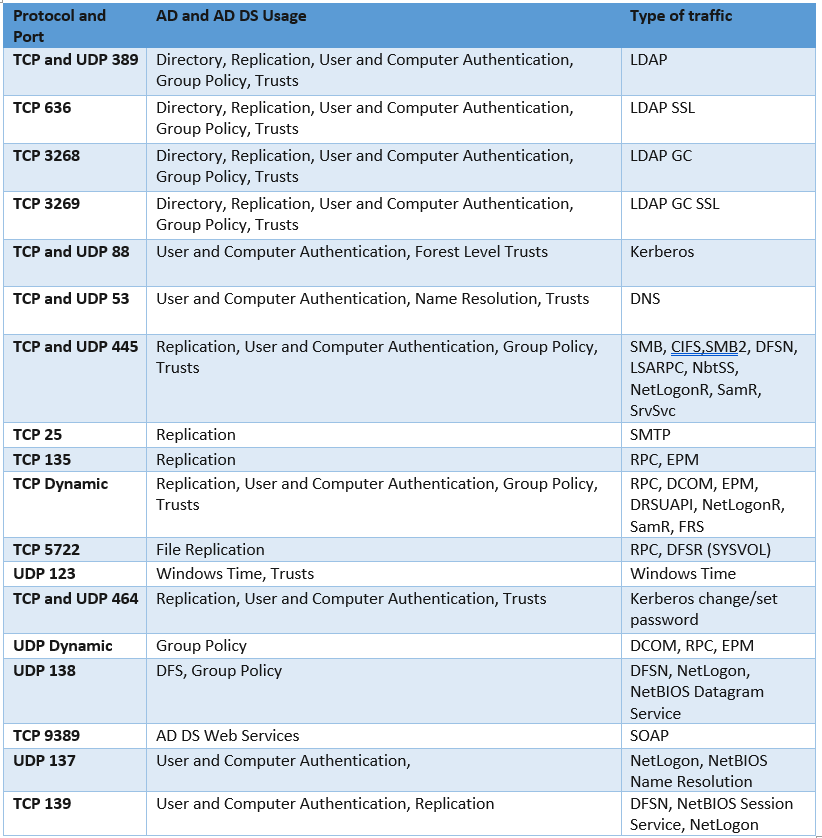
If you have additional requirements such as DFS replication, Windows Cluster, DHCP, or other services refer to the below article, however, most of these ports are already covered by the above table.
https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/service-overview-and-network-port-requirements#4
Domain Controller to DMZ
If you are running a member server or domain-joined client on a DMZ, for effective communication you need to open the ports mentioned above in the DC to Client section. However, you should try your best not to open a domain controller communication to your perimeter network. It is not recommended because you are exposing your domain controllers to a certain risk.
Nevertheless, there are other options available to consider, such as the Resource Forest concept and extending corporate forest through RODC. I’m not a fan of RODC because you need to open these network ports to the on-premises environment. So, let's discuss isolated forests (Resource Forest)
What is Resource Forest
Resource forest is an isolated AD DS forest model that is deployed in your perimeter network. All the domain controllers, members, and domain-joined clients reside in your DMZ. If your perimeter clients need to access on-premises resources you need to consider Forest trust. You can consider a One-way trust between the resource forest and the user forest. It will provide access from the trusted domain to resources in the trusting domain.
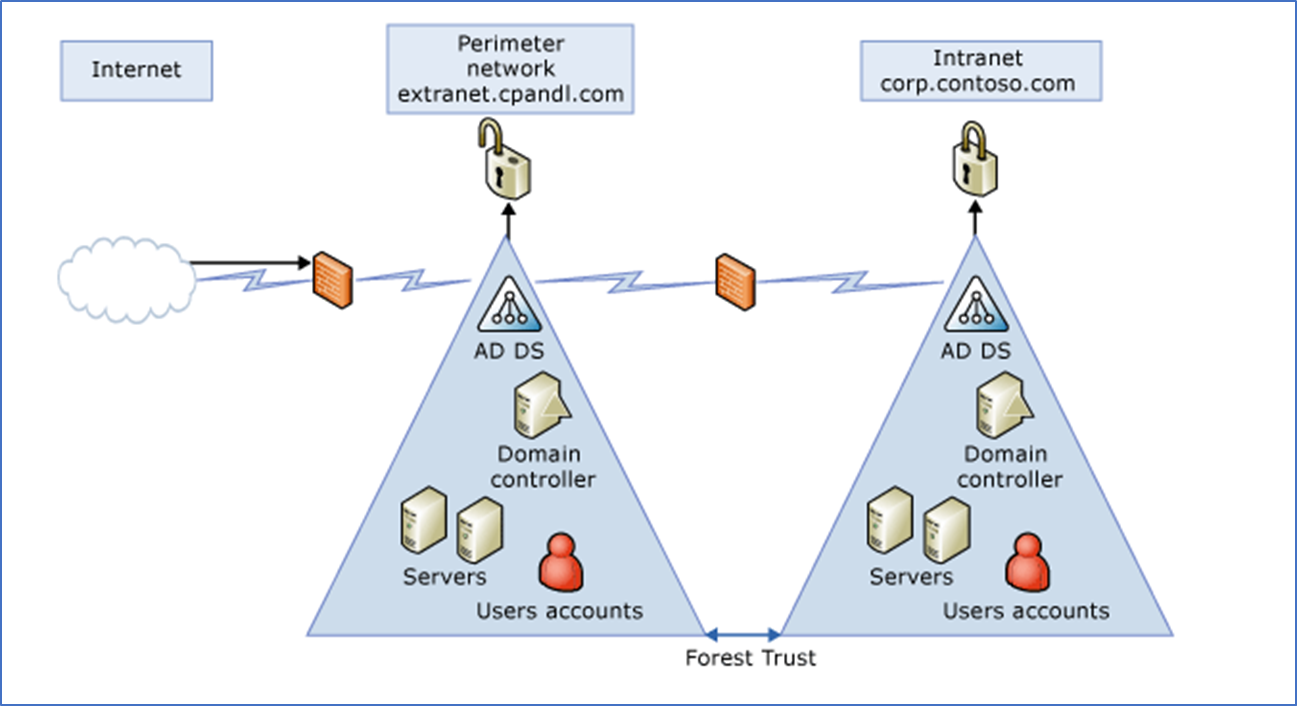
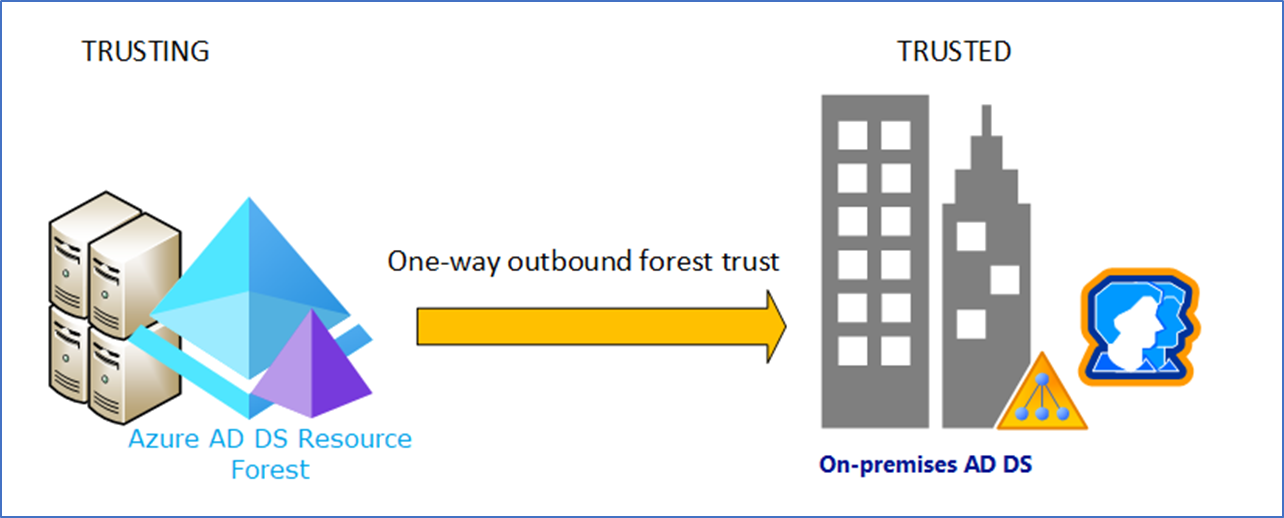
Ports required for forest trusts on windows server 2008 and above
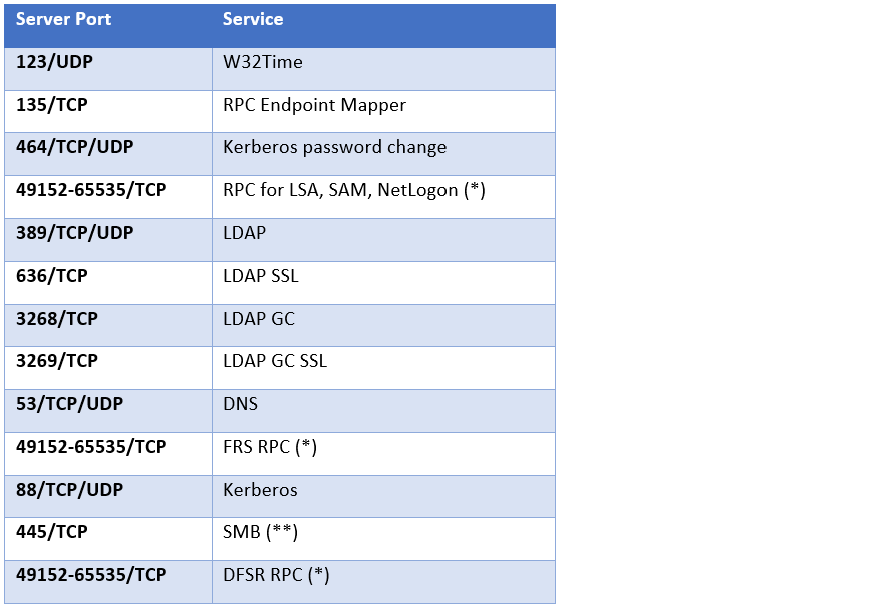
Additional – Restricting RPC port to a specific
As I mentioned before Active Directory replication remote procedure calls (RPC) use port 135 to map dynamic ports for the RPC communication. The port range is between 1025 and 5000 on Windows server 2000 to 2003 environments and 49152 to 65535 on windows server 2008 and above. An administrator can override this functionality and specify the port that all Active Directory RPC traffic passes through. This procedure locks down the port.
You need to configure this from the registry entries on all the domain controllers. After it's been configured, both Active Directory server-side replication traffic and client RPC traffic are sent to these ports by the endpoint mapper.
There is a Microsoft article (here) that specifically describes this process. Take a backup of your registry before making those changes. Also, this is a change you need to plan well, you need to do the change of all the domain controllers at once, and downtime is required.
Additional – PortQryUI Tool
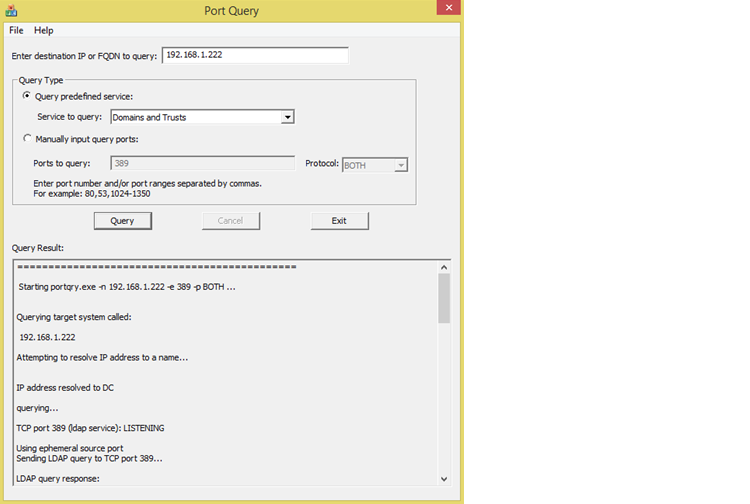
PortQry is a command-line utility that you can use to troubleshoot TCP/IP connectivity used by Windows components and features. The utility reports the port status of Transition Control Protocol (TCP) and User Datagram Protocol (UDP) ports on a remote computer. You can use this tool to see if you have access to the Active Directory recommended ports. You can query access to the following services:
- Active Directory Domain Services (ADDS)
- Active Directory for Lightweight Directory Access Protocol (LDAP)
- Remote procedure call (RPC)
- Domain Name Service (DNS)
- Other ADDS-related components
- Other components on which ADDS is dependent
Download - https://www.microsoft.com/en-us/download/details.aspx?id=24009
Hope this post is useful
Additional readings and references.
AD domain and trust ports - https://docs.microsoft.com/en-US/troubleshoot/windows-server/identity/config-firewall-for-ad-domains-and-trusts
Windows port overview - https://docs.microsoft.com/en-US/troubleshoot/windows-server/networking/service-overview-and-network-port-requirements#4
RPC port restrict - https://docs.microsoft.com/en-US/troubleshoot/windows-server/identity/restrict-ad-rpc-traffic-to-specific-port







