AVD is the Microsoft VDI solution with global Microsoft managed PAAS components such as Remote gateway, Web Access, and Broker services. Now, you can use Azure private links to connect to these remote resources privately and securely. With private endpoints, you no longer expose your services to the public internet. Using Microsoft's backbone, session hosts will connect to the PAAS components by internal IP addresses. Also, if required, Microsoft configures clients to connect only through the Site-to-site VPN or Express route.
This is Part 2 of the article series, where I will configure private endpoints for Feed discovery and Feed Download, a Full private AVD solution. In part 1 (here), I discussed configuring private endpoints for session hosts to the Microsoft AVD control plan.
This can be considered to be optional in many situations. When you configure private Endpoints for Feed Discovery and Feed download, your clients need to be on the corporate private network to access AVD. AVD traffic flow will be fully routed through the private internal network.
To configure, you need to do the same Private endpoint configurations on Workspace for Feed and Global.
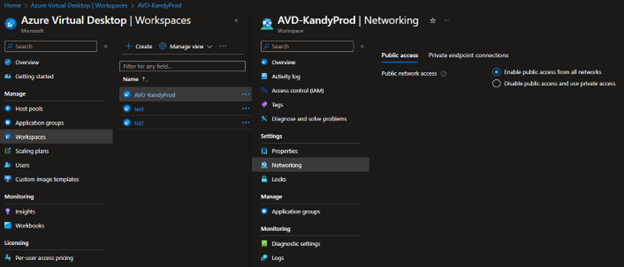
- Log in to the Azure Portal – Azure Virtual Desktop – Workspaces, click the workspace and go to Networking.
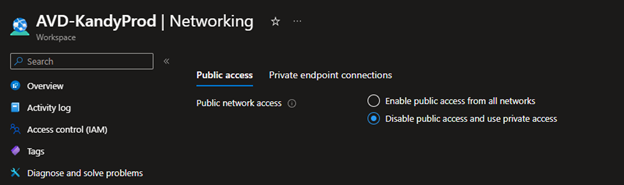
- Click Disable public access and use private access.
- Click Private endpoint connections and + New private endpoint.
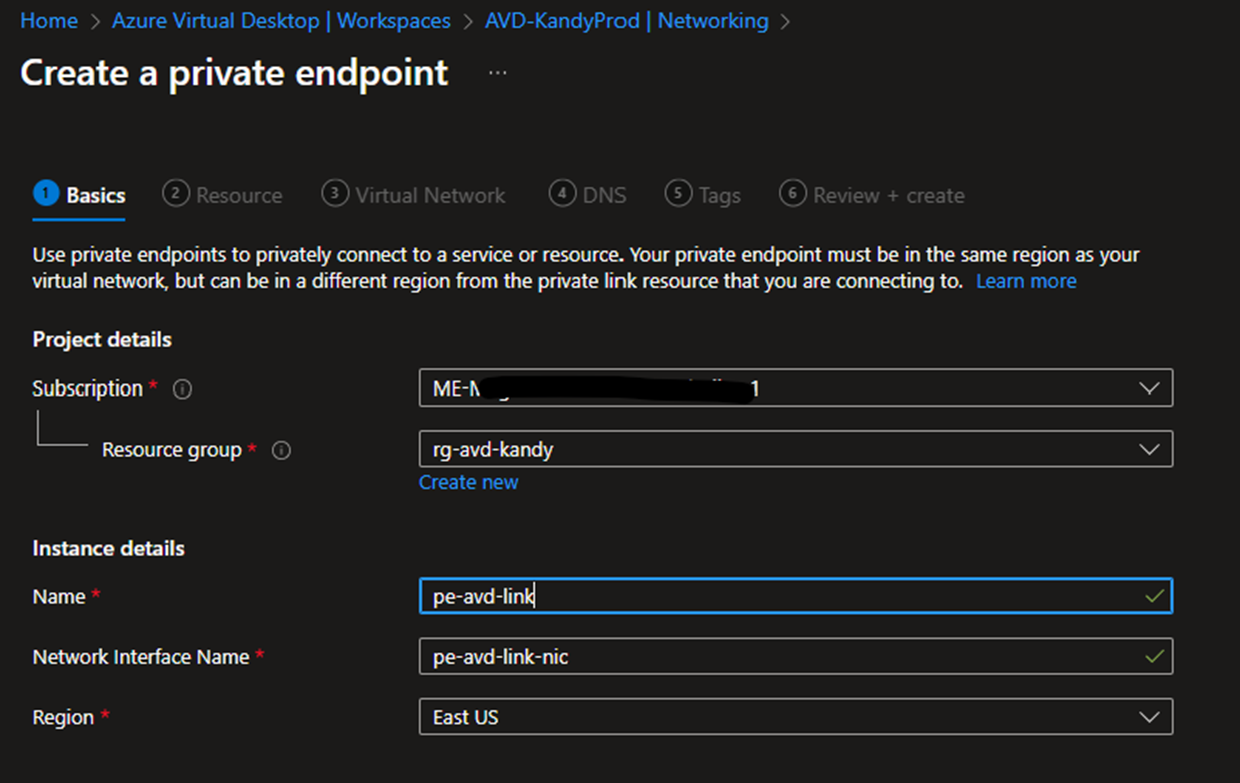
- Select Feed
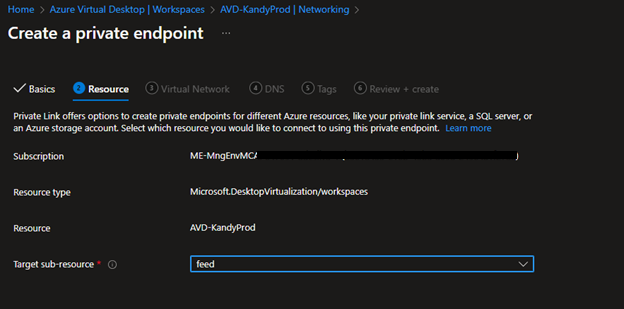
- Next, select the subnet which you want to place the Private endpoint. You can have a dedicated one if you wish.
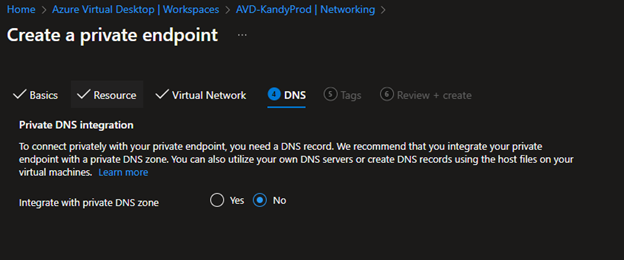
- Next, you need to select the DNS. You can use Private DNS Zone. I'm using on-premise ActiveI'mrectory as my DNS server, so I'm not integrating with private DNS Zone.
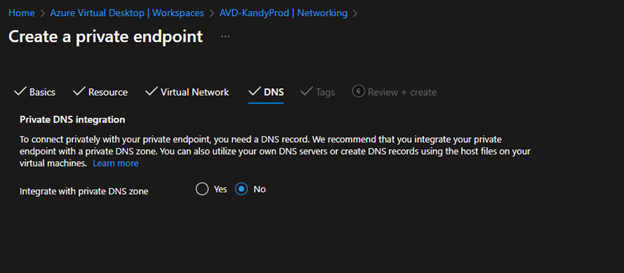
- Review and create the Private Endpoint.
- Next, you need to ensure that your clients can resolve the DNS of the private endpoints. Here, I'm using on-premises ActivI'mirectory as my DNS for clients. I'm creating a forward lookup zone and manually creating A records for private endpoint FQDN to resolve internal IP addresses.
Optional - DNS forward lookup zone
Next, you need to make sure that your clients can resolve the DNS of the private endpoints. Here, I'm using on-premises activI'mirectory as my DNS for clients. I'm creating a forward look zone and manually creating A records for private endpoint FQDN to resolve internal IP addresses.
- Login to the ADDS domain controller.
- Go to DNS – Forward lookup zone – Create new zone. Skip this if you already have a forward lookup zone for privatelink.wvd.microsoft.com
- Name the zone as – wvd.microsoft.com
- Go to the Private endpoint – DNS Configurations and note down custom DNS records.
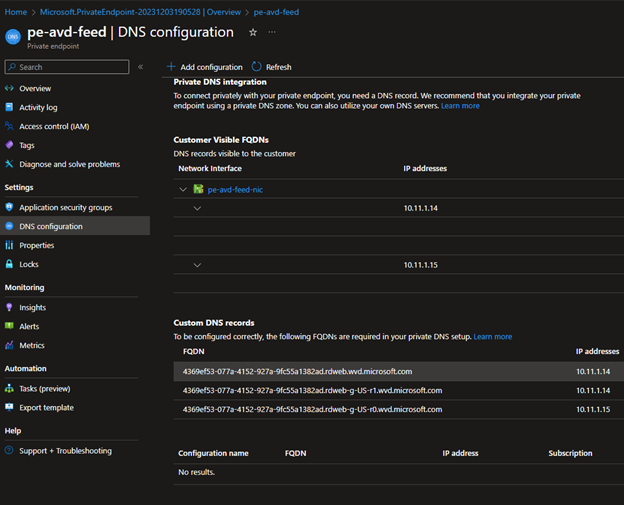
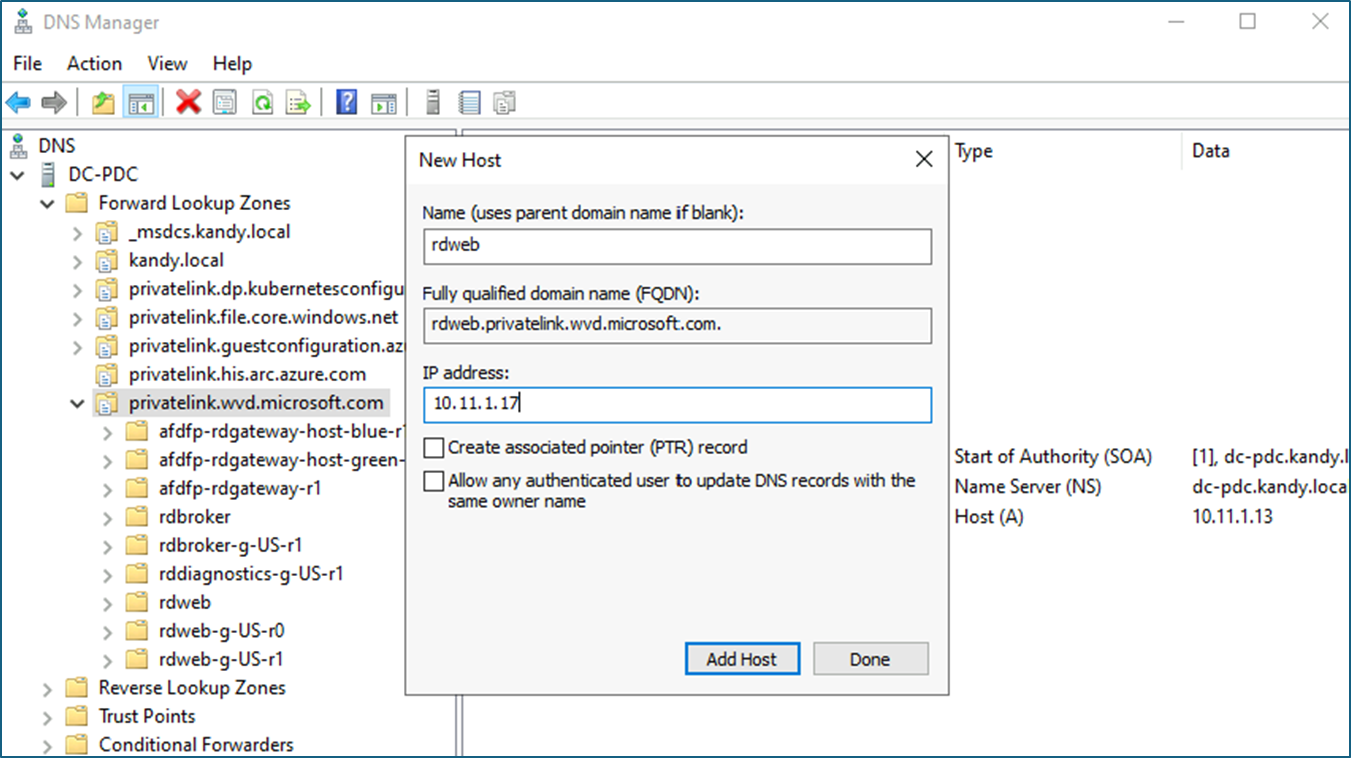
- Copy the FQDN till wvd.microsoft.com and create the A record in ADDS DNS using it.
In example -
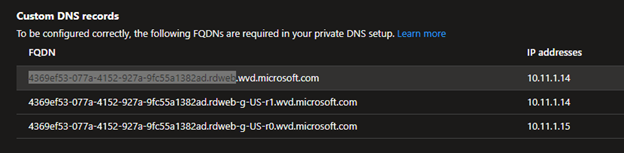
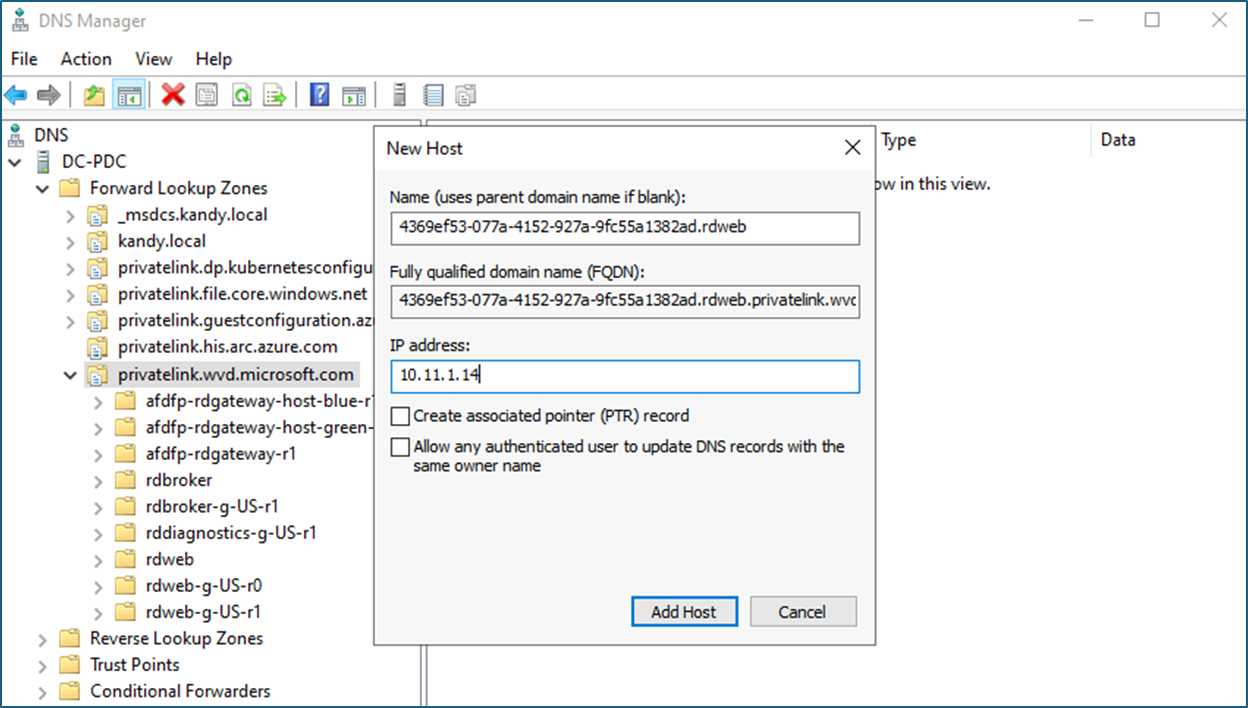
- Create all custom DNS records in ADDS DNS.
Configure Private Endpoint for Global Feed download
- Log in to the Azure Portal – Azure Virtual Desktop – Workspaces, click the workspace and go to Networking.
- If it's not already disabled, Disable public access and use private access
- Click Private endpoint connections and + New private endpoint
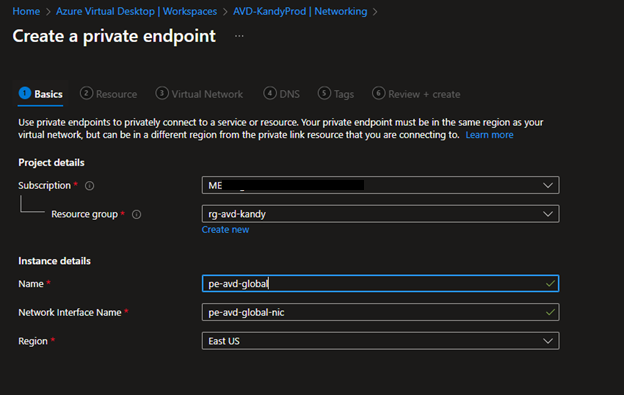
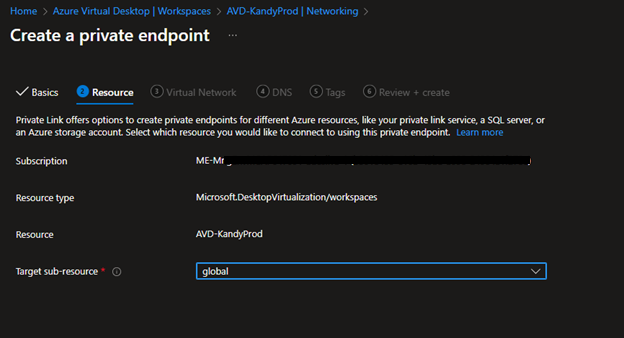
- This time, select Global.
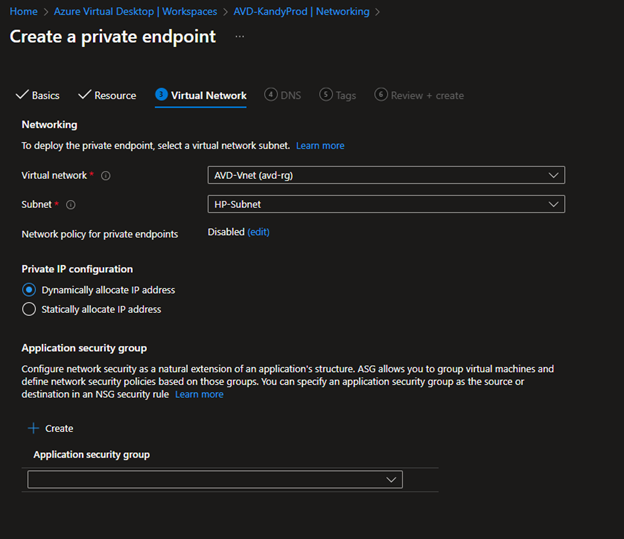
- Next, select the subnet where you want to place the private endpoint; you can have a dedicated one if you wish.
- Next, you need to select the DNS. You can use Private DNS Zone. I'm using on-premise ActiveI'mrectory as my DNS server, so I'm not integrating with private DNS Zone.
- Go to the Private endpoint – DNS Configurations and note down custom DNS records.
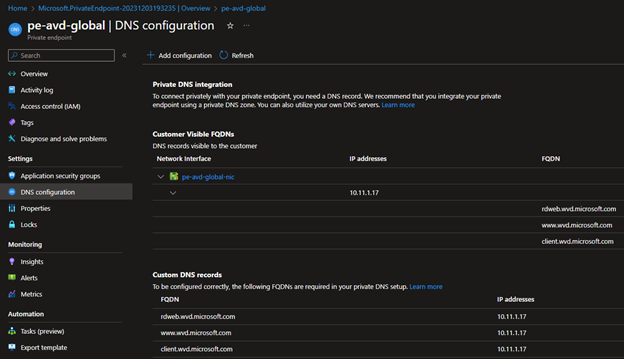
- As you did in the previous step, Copy the FQDN till wvd.microsoft.com and create the A record in ADDS DNS using it.
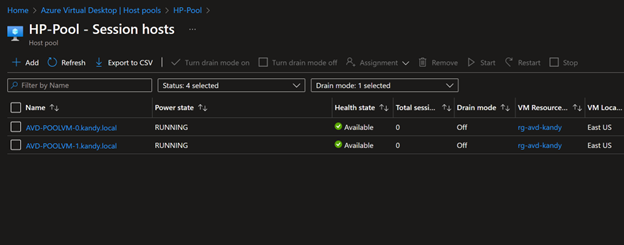
- After configuring the DNS, restart the Session host VMs. Once you have configured everything, you will see VMs connecting to the AVD VM's service through private links.
- Now, if you try to connect to the AVD session hosts using the public internet, you should see the error below, and you can now only connect from the internal network.
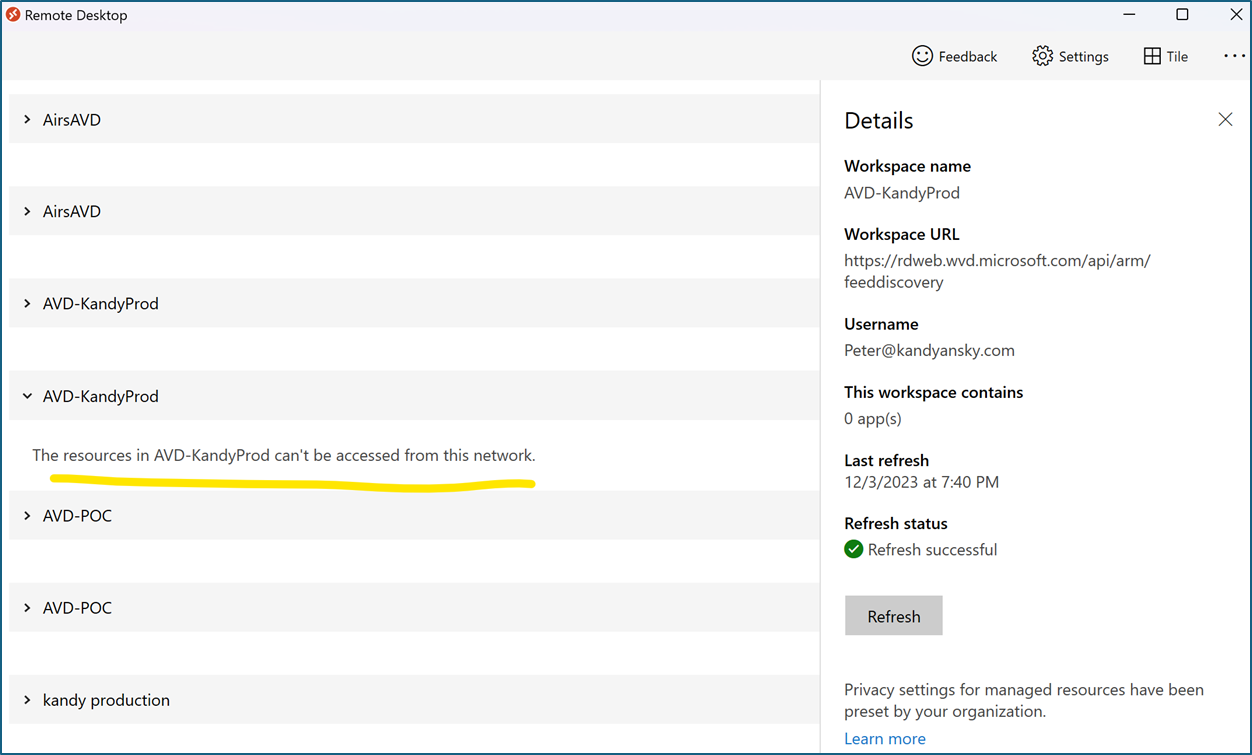
I hope this post is helpful.

















