What is Geographic Restrictions?
Geographic restrictions refer to providing services to users based on their physical location. A common analogy is school districts: if you live in a particular area, you can send your children to specific schools and access that district's resources. Similarly, geographic restrictions allow or deny access to digital resources, services, or applications based on the user's geographic location. This practice is known as geo-blocking or geo-fencing. Geo-fencing involves setting virtual geographic boundaries and controlling access or delivering content depending on whether the user is inside or outside these boundaries. This is especially relevant in media streaming, e-commerce, and online gaming. User location is typically identified through their IP addresses. Each public IP contains geolocation information, and service providers can compare this IP data against a geo-database to determine the user's location. Based on these locations, rules can be applied to either allow or deny access to services.
Imagine you have a server that receives requests from users located in different areas. On this server, specific rules are established: users from Location 2 and Location 4 are allowed access, while users from Location 1 and Location 3 are denied access to services. When users attempt to connect or request services, those from Location 1 and Location 3 will be denied access, and users from Location 2 and Location 4 will successfully view the content and use the services.

Common use cases for Geographic Restrictions
One common scenario is when content is available in multiple languages, and the goal is to present it in the user's preferred language based on their location. Streaming services often restrict content availability due to location or licensing agreements. Also, online gambling and gaming platforms may need to comply with specific local regulations, which can vary by region. E-commerce websites frequently offer different products or pricing based on geographical location. News and media websites may also restrict access to certain regions. While these are some of the most common use cases, many others exist.
Geographic Restrictions on AWS
AWS services provide tools and features that enable you to implement geographic restrictions.
Amazon Route 53
Amazon Route 53 is a highly available and scalable DNS service offering various DNS routing policies, including failover, latency-based, and geolocation routing. Geolocation routing enables you to define multiple DNS records for the same domain name, directing users to different servers based on their geographic locations. For example, you can set up three servers: one dedicated to users in the U.S., another for users in Asia, and a third for users in other regions. This allows you to create three geolocation records for the same domain name, each associated with a specific geographic area and pointing to the corresponding server. When a user from the U.S. accesses the domain, they are routed to Server 1. If a user is located in Asia, they are directed to Server 2. Users from any other location are routed to Server 3, the default record. This default record captures requests from locations not specified in the other records. Without a default record, users outside the defined locations would not receive IP addresses, restricting their access to your services.
AWS WAF
AWS WAF is a Layer 7 firewall that protects web applications from various web attacks. It enables you to create custom rules to allow, block, or monitor web requests based on specified conditions. With AWS WAF, you can set sophisticated geographic rules. For example, if your operations are primarily in Europe but you have a single client in the U.S., you can create a rule that blocks all requests from the U.S. while still allowing requests from your client's specific IP address.
Amazon CloudFront
You can implement geographic restrictions using Amazon CloudFront, a Content Delivery Network (CDN) service designed to distribute static and dynamic content quickly and reliably. CloudFront provides the capability to allow or block requests based on a user's location, using either an allow list or a deny list.
You may wonder which service to choose for your specific needs. The answer depends on your architecture, requirements, and use cases. There is no one-size-fits-all solution; AWS services can be used independently or in combination. In the following example architectures, you can see how these services work together.
Reference Architecture
In this first example, the services are hosted on a single public instance with a public IP address, and users directly access the service. You can use Amazon Route 53 with geolocation routing to implement geographic restrictions. This allows you to restrict access for users in specific locations.
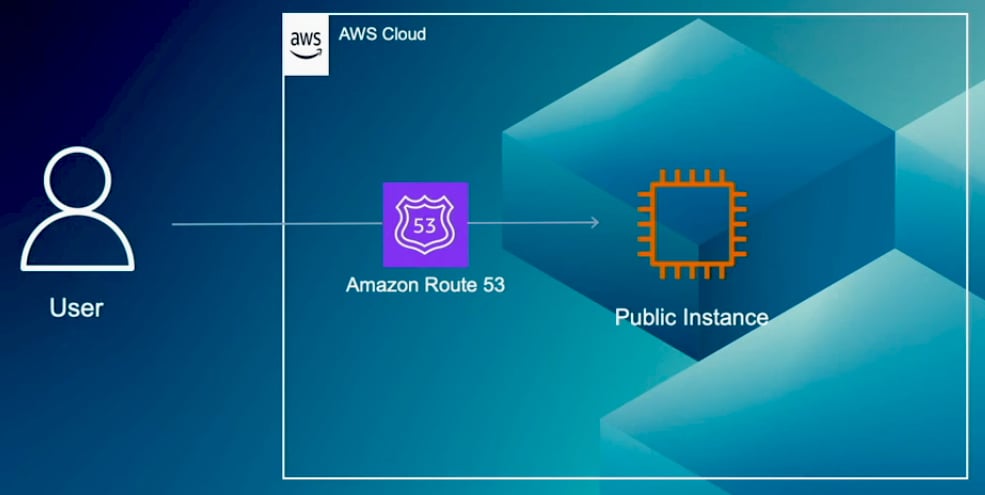
In this second example, the services are deployed on a fleet of instances, which may also include containers running on Amazon ECS or EKS. These services are front-ended by an Application Load Balancer. Here, you can use Amazon Route 53 to implement geographic restrictions and AWS WAF to protect against web attacks such as cross-site scripting and SQL injection. While it is possible to use either service independently, combining them can improve your overall security and access control. For example, if you want to provide services exclusively to users in North and South America while blocking access from two specific countries in South America, using both services simplifies the process. With Route 53, you can create two records, one for North America and another for South America. Then, using AWS WAF, you can configure rules to block access from just the two specified countries in South America.
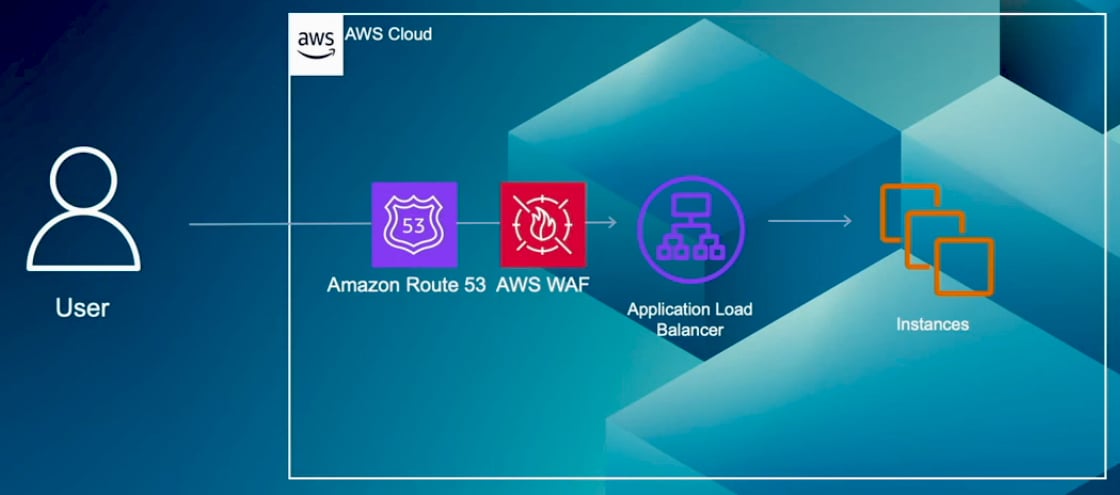
In this third example, Amazon CloudFront is configured with multiple origins, such as Amazon S3 and an Application Load Balancer. With CloudFront, you can implement geographic restrictions by either creating an allow list to permit access from specific countries or a block list to deny access to certain countries. Similar to the previous examples, you can integrate other services like Route 53 and AWS WAF to implement more complex geographic restrictions. It's important to note that when using WAF with CloudFront, the geo-restriction rules in CloudFront are applied first. These rules filter out users based on the defined allow or block lists, and CloudFront forwards the allowed requests to WAF for further inspection.
Implementing Geographic Restrictions
Amazon Route 53
In the AWS Management Console, navigate Route 53 and select Hosted Zones. Choose your hosted zone, then click on Create Record.
You can provide a Record name, and it's important to create multiple records with the same name, each pointing to different targets associated with various geographic locations. For example, you might create two records for continents: one for North America and another for South America. Also, you can create more granular records for individual countries, and within the U.S., you can further refine your records to specify individual states.
You can enter a Value for the first server and set the TTL to either the same or a lower value. For the Routing policy, select Geolocation.
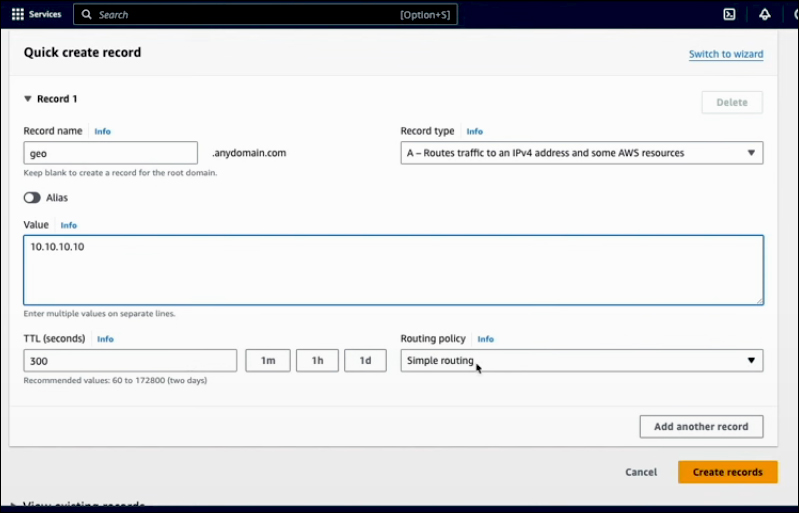
When specifying the location, you can choose from continents, countries, regions, and states in the U.S.
You can associate this record with a health check by choosing a Health check ID. The Record ID serves as a note to help identify this record; you can add any relevant text.
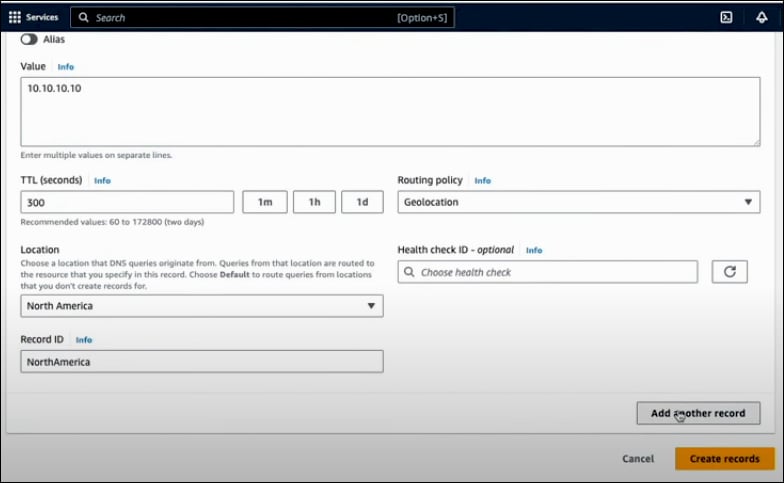
Likewise, you can create more records pointing to different servers. In this example, you have one record for North America and another for South America. In this configuration, users from North America will be routed to Server 1 (10.10.10.10), while those from South America will be directed to Server 2 (20.20.20.20). After completing this, click Create Records.
You can create a default route, which is useful for catching any requests from regions outside the specified continents. These requests will not receive IP addresses by default and will be blocked. However, if you have a server that can provide a message such as, "This service is not available in your region," you can create a default record that points to Server 3 (30.30.30.30). To do this, create a record and select Default as the location. Now, you will have three records with the same name: one default record, one for North America, and one for South America.
AWS WAF
Next, navigate to Web ACLs in the AWS Management Console, where you will find your Web ACL. Click on it to add a rule for geographic location restrictions.
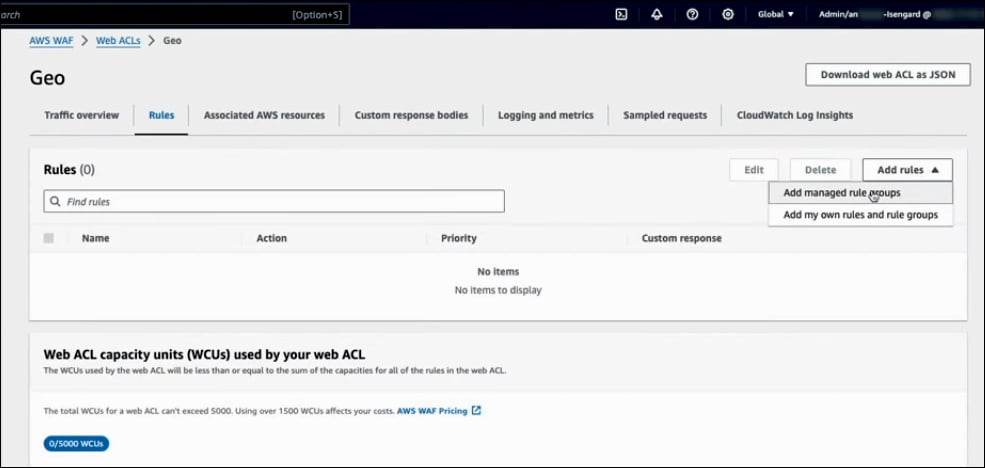
Go to Rules and click on Add Rules. Here, you have the option to use managed rules (Add managed rule groups) or create your own custom rules (Add my own rules and rule groups).
When adding a rule, choose the Rule Type and assign it a Name. You can select either a Regular Rule or a Rate-Based Rule. A Regular Rule will apply continuously, while a Rate-Based Rule monitors the source IP and limits requests based on the number of requests received over a specified period.
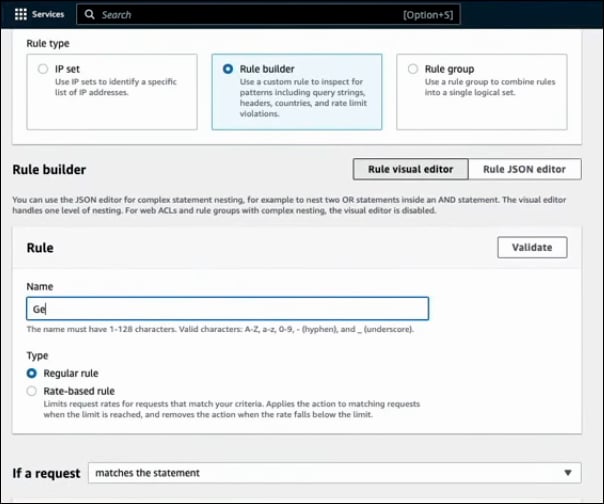
When creating a Statement for your rule, you have several options: Matches the statements, Matches all the statements (AND), Matches at least one of the statements (OR), Doesn't match the statement (NOT). Next, you can build your statement. For example, you could specify that the rule applies if the request originates from a country. You can select the relevant Country codes to enforce your geographic restrictions.
When setting up the rule, you can choose to determine whether the request is originating from the Source IP address or the IP address in header. This choice is important because there may be CDNs in front of your resources that receive traffic and forward it to you. If you select Source IP and there is a CDN in place, you will only be checking the IP addresses of the CDN, which may not be useful for geographic restrictions. Instead, you should inspect the Source IP address provided in the headers, as CDNs add the IP addresses in the headers. On the other hand, if you know that no CDNs or proxies are involved and users connect directly to your services, you can rely on the Source IP addresses in the request.
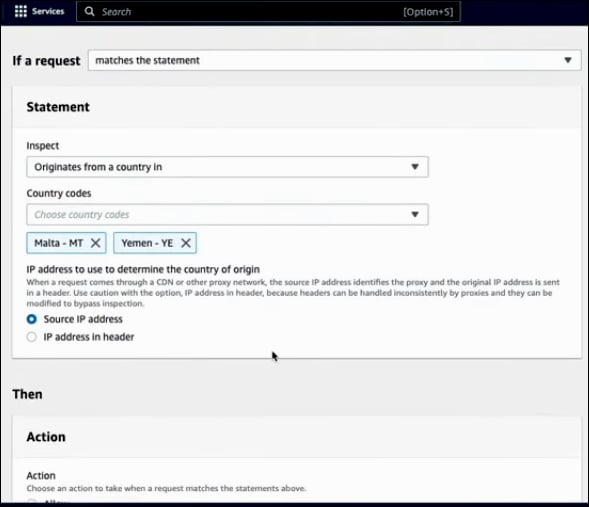
Next, you need to define the Action. You have several options: Allow, Block, Count, CAPTCHA, or Challenge. After selecting the action, click Add rule to finalize the configuration.
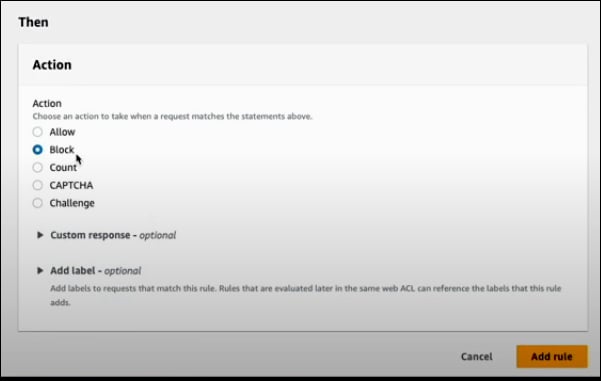
After validating your rule, you can adjust priority by moving it up if you have other rules in your Web ACL. Once the priority is set, click Save. Your Web ACL for AWS WAF will include this rule, implementing geolocation restrictions based on the specified countries.
Amazon CloudFront
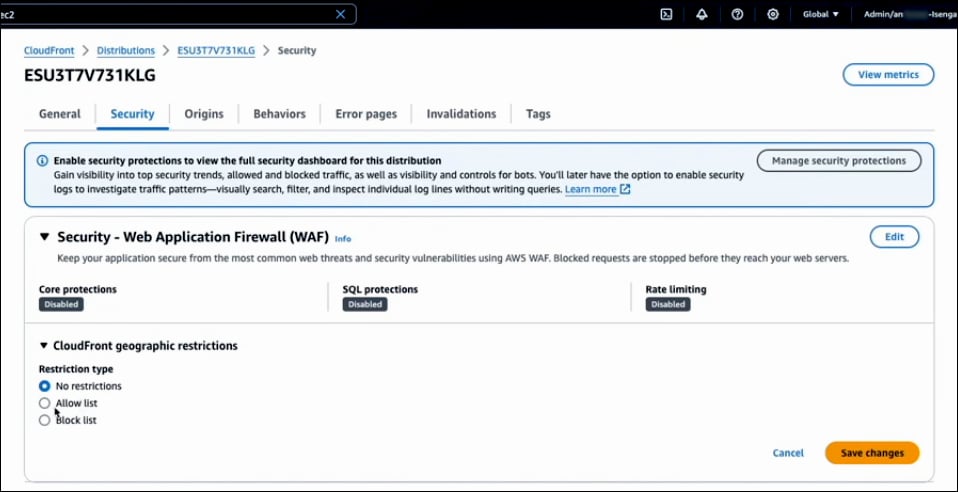
Next, let's switch to the CloudFront console. Click on Distributions, then navigate to the Security tab. Scroll down to find CloudFront Geographic Restrictions and expand it. Click on Edit to modify the settings.
You can choose either an Allow List or a Block List. Select the Countries you want to include in your chosen list. Once you have made your selections, click Save Changes. CloudFront will now enforce these geographic restrictions, allowing or blocking access based on the countries specified in your list.
Reference:
AWS Events














